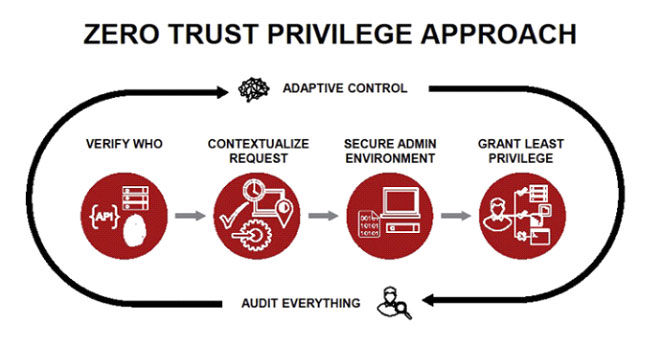
The 5 Steps to Building a Zero Trust Network

Zero Trust is a network security model, based on a strict identity verification process. The framework dictates that only authenticated and authorized users and devices can access applications and data – period. It also protects those applications and users from advanced threats on the Internet. At the heart of Zero Trust is data security and specifically sensitive data or personally identifiable information (PII).
Data is the asset attackers want to steal, whether that’s PII, protected health information (PHI), payment card information (PCI), or intellectual property (IP), all of it has value.
The Zero Trust model is the response to the realization that the perimeter security approach hasn’t been effective. Many data breaches happened because attackers who got past corporate firewalls managed to move through internal systems without discovery. In addition, the perimeter is no longer clearly defined because applications and data stores are on-premises and in the cloud, with users accessing them from a variety of technologies.
How a Zero Trust Framework Better Protects Sensitive Assets
Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.” Every access request is fully authenticated, authorized, and encrypted before granting access. Zero Trust applies microsegmentation and the principle of least privilege to minimize lateral movement. Rich intelligence and analytics are utilized to detect and respond to anomalies in real-time.
Zero Trust is crucial for many reasons:
First, Zero Trust collapses or shrinks attack surfaces. For example, a user logs into an application connected to a data storage server. The user authenticates through an Identity and Access Management (IAM) system and performs an activity then logs out. Upon logout, all IT services to the application and storage server shut down, and the attack surface closes. Even in a hostile network, lateral network traffic is stopped in its tracks and can no longer escalate privileges and move from system to system.
Second, the Zero-Trust model is critical when migrating on-prem systems to cloud-based environments. With most organizations, the internal network perimeter has expanded into the cloud, blurring the boundaries of the security perimeter.
Third, the Zero-Trust framework lays the foundation for a faster, more robust security posture. Zero-Trust can replace traditional VPN access. For example, in a conventional network, a device and user must authenticate to the VPN before they are allowed access to applications and data on enterprise networks. For Zero-Trust, the VPN is eliminated, and users and devices authenticate to the web apps and data themselves without automatically being granted any other access rights to other IT resources. This direct access method is faster because the users will not authenticate to inherited services, only the specific IT system.
5 Steps to Implementing a Zero Trust Network
The Zero Trust model is recognized to successfully prevent cyberattacks. Fortunately, building a Zero Trust architecture is much simpler than it appears. Because Zero Trust is simply a reorganization of most organizations’ existing architecture, it does not require new technology or a complete revamp of technology and security investments. Rather, you can deploy it iteratively while taking advantage of the tools and technologies you already have.
Using a five-step model for implementing and maintaining Zero Trust, you can understand where you are in your implementation process and where to go next. A comprehensive Zero Trust maturity assessment framework can help organizations evaluate their current capabilities and identify the most impactful next steps.
Step #1 – Define the Attack Surface
Most IT security teams work tirelessly to reduce the attack surface which has become overwhelming with “work from home,” IoT, Cloud, and other evolving technology. The attack surface is always expanding, making it difficult to define, shrink, or defend against.
Zero Trust focuses on the surface you need to protect, rather than focusing on the macro-level of the attack surface. The “protect surface” encompasses the critical data, application, assets, and services most valuable to your company.
Here are some examples of critical assets companies typically focus on protecting in a Zero Trust model:
- Sensitive Data – Credit card information (PCI), protected health information (PHI), personally identifiable information (PII), and intellectual property (IP)
- Critical Applications – Databases, transaction, authentication
- Physical Assets – SCADA controls, point-of-sale (POS) terminals, medical equipment, manufacturing assets, and IoT devices
- Corporate services – DNS, DHCP, and Active Directory®
Under Zero Trust, organizations often move their security controls as close as possible to that protect surface to create a micro perimeter with policy statements that are limited, precise, and understandable.
Step #2 – Implement Controls Around Network Traffic
The way network traffic moves across a network determines how it should be protected. Thus, it’s imperative to gain contextual insight around the interdependencies of critical assets. Mapping network traffic allows IT security to add controls to the assets to properly enforce access and provides a big picture understanding of any weak points in how the data and assets are being protected.
Step #3 – Design a Customized Zero Trust Network
While a Zero Trust model provides a blueprint for implementation, monitoring, and defense, Zero Trust networks are almost completely customized, not created from a universal design. The architecture is constructed around the assets an organization deems critical.
Once organizations have identified the assets, data, and services they want to protect and mapped flows relative to the needs of the business, they can map out the Zero Trust architecture, starting with a next-generation firewall (NGFW). The next-generation firewall acts as a segmentation gateway, creating a micro perimeter around the attack surface. With a segmentation gateway, you can enforce additional layers of inspection and access control, all the way to Layer 7 to stop any type of attack trying to navigate around the controls and safeguards.
Step #4 – Design Your Zero Trust Policy
Once the Zero Trust network is created, organizations will need to create Zero Trust policies using the “Kipling Method” to whitelist which resources should have access to others. Kipling, well known to novelists, put forth the concept of “who, what, when, where, why and how” in his poem “Six Serving Men.” Using this method, we can define the following:
- Who should be accessing a resource?
- What application is being used to access a resource inside the protect surface?
- When is the resource being accessed?
- Where is the packet destination?
- Why is this packet trying to access this resource within the protect surface?
- How is the packet accessing the protect surface via a specific application?
With detailed security policy enforcement only known allowed traffic or legitimate application communication is permitted.
Step #5 – Monitor and Log Traffic to Improve Security
Review all logs, internal and external, all the way through Layer 7, focusing on the operational aspects of Zero Trust. Since Zero Trust is an iterative process, inspecting and logging all traffic will provide valuable insights into how to improve the network over time. This monitoring capability becomes the foundation for establishing a comprehensive SOC implementation guide to centralize security operations and incident response.
Now You Can Iterate
Once you have completed the five-step methodology for implementing a Zero Trust network for your first protect surface, you can expand to iteratively move other data, applications, assets or services from your legacy network to a Zero Trust network in a way that is cost-effective and non-disruptive.
Back to blog