The Benefits of Using a SIEM to Improve IT Security
A SIEM’s Role in Network Security Analysis and Monitoring
We put together a series of blog posts that deal with Network Security Design and Log Monitoring that are hopefully providing you clear, straightforward information about the real basics of Network Security. In our last blog post we addressed Log Monitoring and Management and why they are so critical to gathering insight into an organization’s IT Security status and issues.
Previously, we addressed “The Fundamentals of Network Security Analysis and Monitoring” in a blog post where we discussed active versus passive security devices, flow analysis versus packet analysis, and several of the security technologies used to analyze or stop traffic including IDS/IPS technology. Prior to that blog post, we wrote another post titled “Network Security Design is Critical to Eliminating Security Gaps and Reducing Costs” – “The 5 Pieces to the Cybersecurity Puzzle,” where we discussed the five core elements of Secure Network Design.
We’ll end this blog series with this post that will discuss SIEM’s. In this post, we would like to analyze SIEM’s and their function within the SOC or Security Operations Center.
What is the Value and Function of a SIEM?
SIEM’s have 3 critical capabilities in most organizations: (1) Threat Detection (2) Investigation and (3) Time to Respond. SIEM’s were developed to collect, store, analyze, investigate and report on a log and other data for incident response, forensics and regulatory compliance purposes. Prior to SIEM’s, the logs and other data were often manually collected and logs from a variety of different technologies including servers, firewalls, antivirus, spam filters and more had to be collected, normalized and analyzed.
Even in small organizations, there could be over 300 software and hardware products producing logs and a large enterprise will likely have thousands. Thus, as you can imagine this was a brutally slow and monotonous process that was costly and ripe with errors. Now, after ingesting and normalizing the logs SIEM’s typically have the ability to analyze the event data in real-time to provide the early detection of targeted attacks, advanced threats, and data breaches.
So, let’s boil this down into a couple of sentences to provide a clean clear definition of a SIEM.
A SIEM ingests log data from a variety of network hardware and software and analyzes the data in real-time. A SIEM’s purpose is to correlate events and identify anomalies or patterns of behavior like traffic from suspicious IP addresses or unusual exfiltration of data that may indicate a breach.
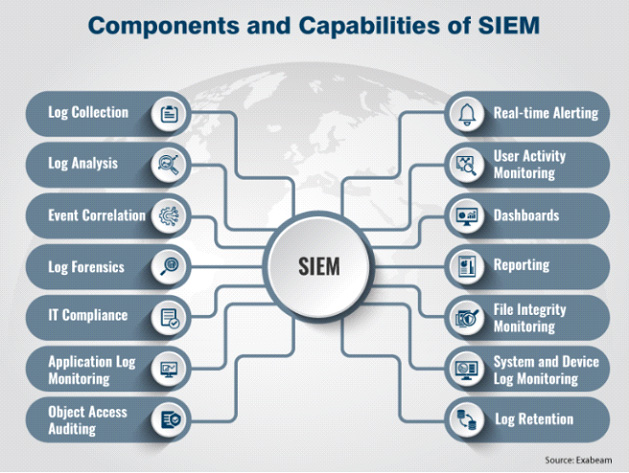
Most SIEM’s have a variety of features and functionality including:
- Basic security monitoring – The basic collection, normalization, correlation, and analysis of logs. This is the fundamental responsibility of a SIEM.
- Security incident detection – The second basic function of a SIEM is to alert security teams to anomalies or policy violations in an automated way with clear information.
- Advanced threat detection – SIEM’s integrate intelligence feeds that provide data on current threats that SIEM’s use to identify threats.
- Notifications and alerts – SIEM’s can be tuned to alert security analysts when policies have been violated or threats have been identified.
- Forensics & incident response – SIEM’s have the ability to store logs so that when a breach or incident occurs, IR teams and digital forensic investigators have the ability to perform root cause analysis.
- Compliance information – SIEM’s are increasingly being used to demonstrate compliance by providing auditing and reporting concerning log-in data, user information, IP address information, and data flow.
How Does a SIEM Help with Log Monitoring and Management
Let’s take a step back and go over some quick information that we introduced in the last blog post titled Log Monitoring and Management. Effective log management is essential to an organization’s security. Monitoring, documenting and analyzing system events is a crucial component of IT security. Log management software or SIEM’s automate many of the processes involved. A SIEM handles the two following jobs that prior to today’s SIEM’s were handled individually:
- SIM – Security information management – Long-term storage as well as analysis and reporting of log data. This was and is still tricky and time-consuming if you must build your own connectors to your IDS/IPS, Firewalls, DLP solutions, Application servers and so many other log generating assets in your IT environment. Most SIEM’s have some connectors out of the box today.
- SEM – Security event manager – Real-time monitoring, correlation of events, notifications and console views. This is the key benefit of SIEM’s because a good SIEM will turn data into insights and a great SIEM, tuned correctly will turn insights into visual dashboards to assist analysts in uncovering anomalies and threats.
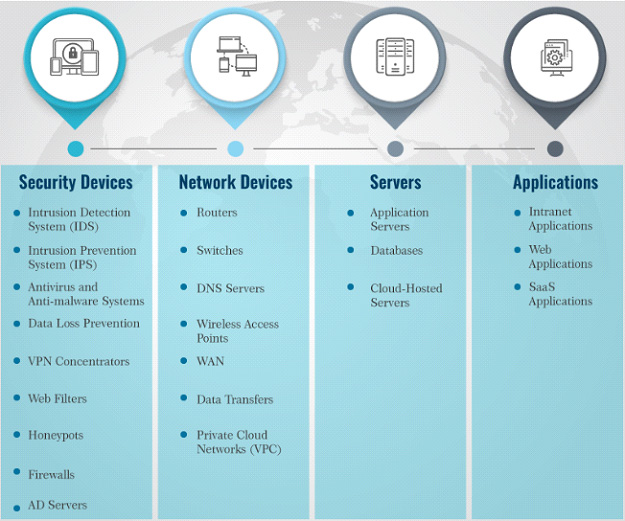
So, if we go back over what we address in the last blog post, a SIEM combines SIM and SEM and provides real-time analysis of security alerts generated by network hardware and applications. They employ or handle the following:
- Data aggregation: SIEM’s aggregate data from many sources, including network, security, servers, databases, applications. They provide the ability to consolidate monitored data so that analysts can monitor and analyze data in a “single pane of glass.”
- Correlation: SIEM’s search for common attributes, and link security events together in order to make sense of the information. The technology provides the ability to perform a variety of correlation techniques to integrate different sources.
- Alerting: SIEM’s are configured to alert analysts when events such as intrusion detection, access control or compliance controls are triggered. SIEM’s are far from perfect and are often blamed for being inaccurate and causing “alert fatigue” from analysts.
- Dashboards: SIEM’s provide dashboards so that data can be charted, and patterns of the data more easily identified.
- Retention: SIEM’s can employ the storage of historical data to facilitate the correlation of data over time, and to provide the retention necessary for compliance requirements.
- Forensic analysis: Because SIEM’s can retain data, and because breaches are not normally detected in real-time, the archived logs are critical to forensic investigations to conduct the post-mortem of a breach and understand its root cause.
The Costs and Benefits of a SIEM
The Costs and Drawbacks of a SIEM
- They are Expensive! In most cases and for most organizations they start in the tens of thousands and can easily cost over $100,000 depending on the brand and the amount of log data that is processed.
- They are Difficult to Operate and Manage. In various surveys, 40% or more of the organizations that responded suggested that they don’t have the expertise in-house to manage a SIEM. SIEM’s are notoriously “noisy” generating many false alerts, so the better the operator, the more effective the technology.
- Deployments are Difficult. Splunk and LogRhythm are the market leaders for the most part and both have their benefits, however, both can be difficult to deploy but it is getting easier with cloud and hybrid deployments. Basic setups of the SIEM’s are fairly straightforward, however, “tuning” them to ingest the correct logs, designing access control, setting up correlations, integrating intelligence feeds and so much more can be time-consuming.
The Benefits and Advantages of a SIEM
- Help Understand Security Threats. Plainly, the reason that companies need SIEM systems to monitor logs and report suspicious events is that most organizations generate far too much event data for any human to be able to make sense of it.
- Correlate Data to Provide IOC’s. Ok, this is a little like benefit #1, however, beyond just collecting, normalizing and analyzing logs, SIEM’s can ingest threat intelligence feeds and many are now integrating machine learning to understand what a real indicator of compromise (IOC) is and what it isn’t.
- Data Presentation. SIEM’s have the ability to present data in a variety of ways including out-of-the-box reporting and customizable reports. The advantage is that analysts can visually spot trends, anomalies, traffic spikes, and so much more. The reports and dashboards can serve as the cornerstone information hub to determine where and how to drill down on any suspicious activity.
- Compliance Assistance. Finally, with GDPR, CCPA, HIPAA, PCI-DSS and so many other pieces of compliance legislation on the horizon, SIEM’s can make reporting on how organizations are safeguarding PII, who is accessing data, and from where.
Conclusion and 3rd Party Assistance
At this point, SIEM’s are clearly proven technology if deployed, implemented and tuned correctly. However, the upfront cost, training, operating manpower and complexity are often overwhelming for security teams. MSSP’s or Managed Service Providers are doing an excellent job of managing SIEM’s for many organizations. The benefits start with the ability to lease, rather than buy SIEM technology; enormous upfront cost savings.
“SIEM-as-a-Service” as it is typically called by MSSP’s also provides seamless implementation and ongoing maintenance so that analysts can immediately use the technology to protect the organization, its customers and employees rather than spending time implementing and deploying.
We got a little long-winded here and certainly, there are a variety of points made about SIEM’s in this post that could be argued including the costs and benefits that were presented. We would love to hear your feedback and certainly thank you for reading the post.