Turnkey MDR Services
SecureIST™ powered by SecureOps
Let our experts manage your entire security ecosystem with our new turnkey MDR service.
OVERVIEW
SIEM-as-a-Service
Our SecureIST offering combines state-of-the-art technology with expert human oversight to provide continuous monitoring, advanced threat detection, and rapid incident response.
By leveraging an industry-leading data pipeline platform and correlation engine, alongside our customized detection rules and dedicated SOC team, we deliver a security solution that is both powerful and adaptable to your specific needs.
This service is not just about monitoring; it’s about managing your entire security ecosystem—from log ingestion and analysis to incident management and comprehensive reporting. With our SecureIST SOC-as-a-Service, you gain the peace of mind that comes from knowing your environment is continuously monitored by experts, your incidents are managed with precision, and your security posture is constantly improving.
Your logs, our platform
We’ll assist you in configuring your log sources to be ingested into our SIEM platform, ensuring that we’re monitoring the right data.
Once your logs are connected, our SecureIST platform will begin monitoring your environment, providing you with real-time insights and daily, weekly, & monthly reports. You can then review the detailed reports and our team’s findings to understand how our service has enhanced your security posture.
What we offer
Powered by leading technologies
A cloud-based data pipeline platform is at the heart of our data processing, allowing us to efficiently collect, filter, and route your logs to our SIEM for real-time analysis.
A cloud-based SIEM supporting advanced correlation powers our advanced threat detection, leveraging machine learning and built-in AI to identify and respond to threats faster and more accurately.
Tailored security solutions
We understand that every organization has unique security requirements, which is why our SOC-as-a-Service offering is designed with flexibility in mind. Whether you need real-time alerting to enhance your internal security operations or a fully managed service to handle incidents from detection through resolution, we provide options that are tailored to your specific needs.
Scheduled & customizable reporting
SecureIST goes beyond monitoring and incident response by offering regularly scheduled reports that provide you with a clear, comprehensive understanding of your organization’s security posture.
Customize your reports to focus on specific areas of interest, whether it’s particular types of threats, compliance requirements, or specific timeframes.
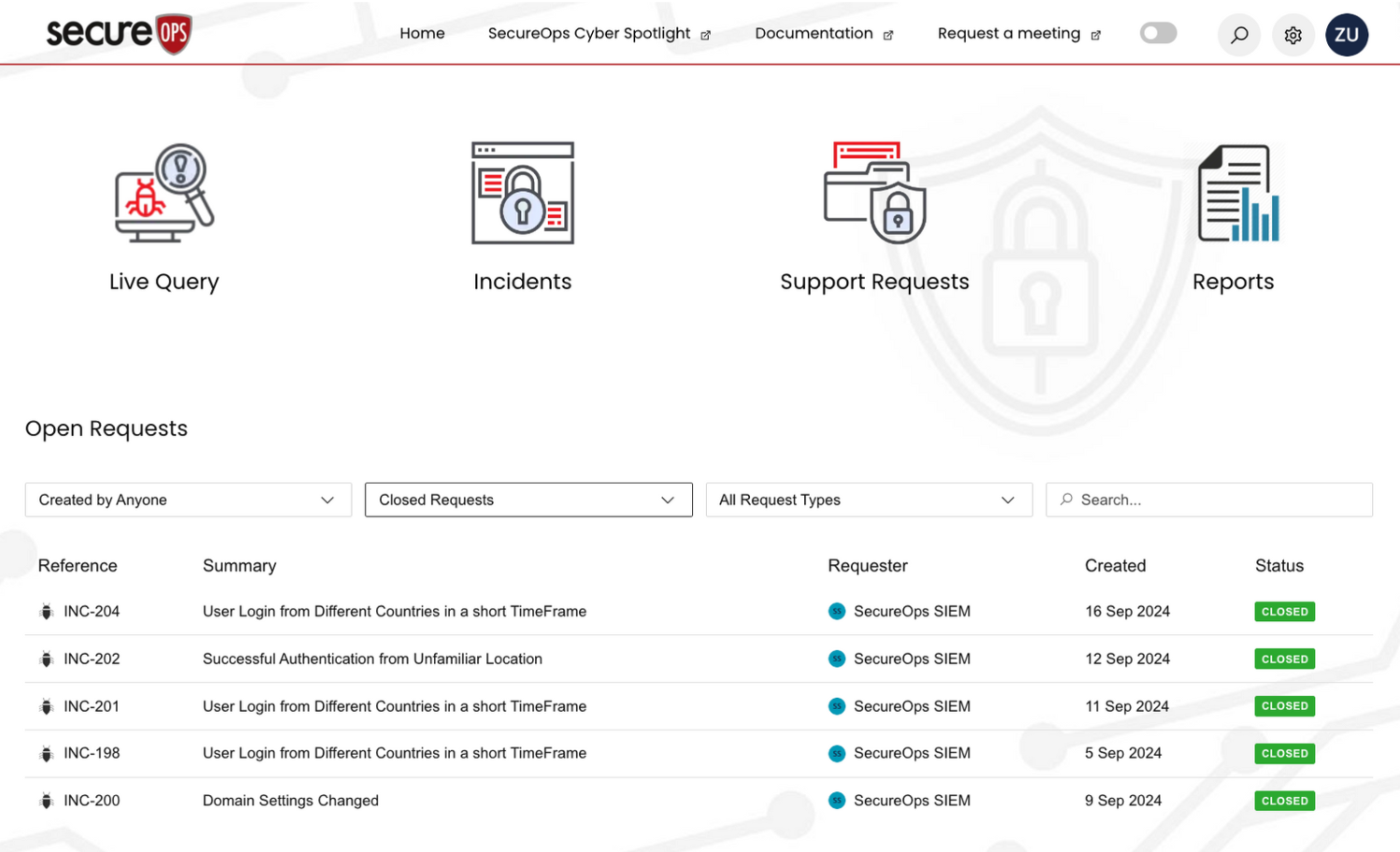
User-friendly management portal
The SecureIST portal is designed with simplicity and efficiency in mind, providing you with an intuitive interface that makes managing your security environment straightforward and hassle-free.
Whether you’re reviewing real-time alerts, managing incidents, or generating compliance reports, our portal simplifies every aspect of your security management, making it easier for you to stay in control and ahead of potential threats.
Live alerting & threat notification
The Live Alerting Solution gives organizations real-time visibility into their security environment. Using advanced analytics and custom threat rules, it sends immediate alerts whenever a potential threat is detected, enabling your internal security team to act quickly and effectively.
This solution is perfect for organizations that need proactive monitoring and fast response but prefer to manage incidents themselves. It equips your team with the essential tools and insights to stay ahead of emerging threats and protect your environment.
Managed incident response
The Managed Incident Response service provides organizations with comprehensive support for handling security incidents. When a threat is detected, our dedicated SOC team takes immediate action, managing the entire incident lifecycle—from detection and analysis to containment and resolution—so your business remains secure and operational.
This service is ideal for organizations that need expert oversight and management of security incidents. It ensures that every threat is addressed promptly and thoroughly, giving you peace of mind that your security is in the hands of experienced professionals.

