Compare Monitoring Service Packages
Whether MDR Plus, a Co-Owned MDR agreement or fully customized SOC, SecureOps has the service packages to protect your environment against today’s threats.

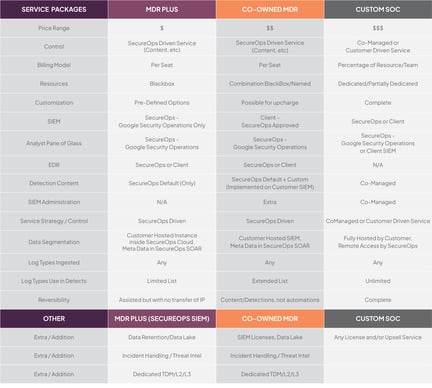
SERVICE PACKAGES
From Purpose-Fit to Fully Customizable
Our monitoring services grow with your needs and security maturity.
MDR Plus
MDR Plus invites you to bring your EDR and use our expertise to strengthen endpoint security 24/7. We'll integrate MDR services using our SIEM to strengthen your security posture.
Co-Owned MDR
Co-Owned MDR invites you to bring your SIEM (and EDR) and grow your investment with our expertise, and stronger current detection rules and content that you'll also own. Your logs stay in your SIEM.
Custom SOC
Custom SOC means just that. Your SOC tailored specifically to your security requirements using your security tooling and our expertise. You make the rules and retain as much control as you want.
Compare Plans

Let’s Find the Right Package for Your Environment
Contact us today to discuss our service packages and find a tailored approach to your security needs.