6 Steps to Create a Program to Meet CCPA & GDPR Compliance Requirements
A 6-Step Guide to Creating a Privacy and Compliance Program
CCPA, GDPR and the coming second wave of new, stricter co
mpliance regulations being put in place globally is resulting in higher costs and IT disruption across organizations regardless of industry. We have written extensively in this blog on CCPA, GDPR, and their impact on organizations; specifically, how DPO’s, IT security, and the Information Technology staff, in general, will have to evolve to deal with this legislation.
We list the blog posts and the CCPA SecureOps service page here so that you have easy access to our thinking on the legislation as well as our best advice on how to manage the different aspects of the law including DSAR’s/SSR’s. In this post, we’ll discuss how organizations, including IT security, should deal with their customer’s personal information (PII) and how to create a security and compliance program to manage the implementation of a new data privacy approach.
- Blog – 6 Keys to Automating the DSAR Process Under CCPA https://secureops.com/privacy/processing-dsars-under-ccpa/
- Blog – Executing DSAR’s Under CCPA & GDPR https://secureops.com/security/ccpa-dsars/
- Blog – Are Organizations Ready for The California Consumer Privacy Act (CCPA)? https://secureops.com/privacy/blog-not-ready-for-ccpa/
- Blog – How the California Consumer Privacy Act (CCPA) Will Impact Business https://secureops.com/security/blog-ccpa/
- Blog – Four Data Protection and Privacy Laws You Must Know https://secureops.com/privacy/data-privacy-legislation/
- Service Page – CCPA Guidelines and Requirements https://secureops.com/solutions-portfolio/ccpa/
Introduction
Technology and systems that hold PII are critical pieces of managing privacy, other elements of achieving data privacy compliance will require assistance outside of IT and IT security. According to Privacy Management Software provider TrustArc, 61% of companies will need 3rd party IT technical consulting and 55 percent expect to need legal or compliance consulting. Further, 45% will need additional personnel training to develop, deliver, and follow augmented policies and procedures for privacy compliance including collecting and processing DSAR’s (SSR’s). Don’t worry, this is not a commercial for Service Providers like ourselves – we are just laying the groundwork to create a practical guide.
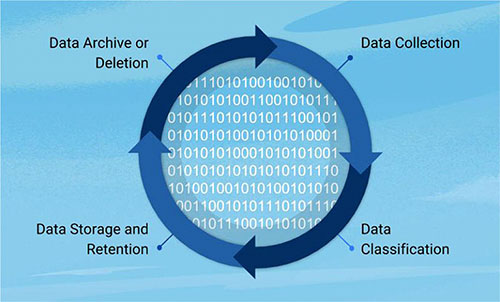
We created a straightforward 6-step process for creating a data privacy and compliance program that starts with identifying PII across the organization through to creating an ongoing procedure for managing, handling, and retaining sensitive data going forward.
A 6-Step Data Privacy and Compliance Program to Meet CCPA & GDPR
Step 1: Identify and Map PII
Compliance programs by nature start with trying to understand if the legislation affects your organization and if so how? Then, organizations will need to start the hard work of going through and managing data discovery, data identification, or data mapping as well as doing data and PII inventory.
Start by gathering answers to the following questions in writing:
- What personal data do you currently collect?
- What are your methods for data collection?
- Where and how do you store this data?
- Do you share the data you collect? If so, with whom?
- Do you sell the data, provide in exchange for a service, or use it for a different purpose?
Identify what categories of PII you collect, what you’re using that information for, and who you may share that information with, including third parties. Understanding the information collected in the questions will allow you to set up your DSAR or SSR process more effectively. Further, you will have all the details and transparency of your data to create data retention and destruction policies and how you will manage the PII throughout its lifecycle in your organization.

Step 1 should also include Identifying the business stakeholders that are affected by the change in your compliance requirements; including all organizations that are responsible for the collection, maintenance, and use of personal data. Also, understand which resources you will need in terms of specialists, technology, and software you will need to implement your compliance strategy.
CCPA and GDPR have advanced a variety of industries including Privacy Management Software providers who provide solutions for organizations to manage their PII and respond to DSAR’s with an automated process.
Step 2: Organizational, Data and Policy Assessment
Now that you have mapped your sensitive data the next step is understanding the type of data you have, the privacy regulations that affect the data, and how to manage the data going forward. Organizations should be able to answer and document the answer to the following 6 questions:
- What privacy regulations must you adhere to with respect to where you operate your business and where your current and target customers live.
- Which applications or processes are currently collecting and storing PII?
- What categories and types of PII data are you storing? Also, a tough question for many businesses will be “Do you have a valid business need for maintaining that data?”
- We mapped the PII in step one so Step 2 will focus on who has access to the data, and what access do they have?
- What are the current policies and procedures for managing the collection, storage, processing, distribution, and disposal of privacy-related data?
Step 3: Understand the Risk of Managing and Storing PII
Conducting a risk assessment for all PII stored across the organization is critical to putting a revenue and cost projection to managing and storing PII. The more data you collect and manage, the more effective your organization will likely be at marketing to your customer base, increasing share of wallet and customer lifetime value. However, with CCPA, GDPR, other privacy legislation with fine and penalties, and now lawsuit costs, that data presents a real financial risk.
Thus, you must decide whether the expense of protecting the data is appropriate for the benefit it provides. Much of the data that is retained for convenience or for possible future use may unnecessarily increase risk. Conducting a risk assessment will identify controls and process gaps associated with the collection, processing, storage, and use of personal information.
The assessment results will identify your greatest risks and document the severity of security gaps, allowing you to focus on areas of improvement. Within your assessment, you will look at policies that explain in detail how data should be managed and steps that should be followed if that data is compromised.
Based on the data privacy protection strategy you decide to adopt following the risk assessment, you will need to update existing policies and procedures, create new ones to cover the gaps, and conduct training on them.
Step 4: Design Controls and Procedures to Manage PII
Many organizations have started with Step 4 in trying to comply with CCPA by updating their privacy, data collection, cookie, and other data-related notices on their website and have distributed them through e-mail. I have received countless notices in the first 90 days since CCPA was activated on January 1, 2020.
Updated privacy information and controls should be accompanied by the safeguard policies that essentially protect the data from breaches, misuse, and other security issues. These policies should address who can handle or manage the data, what they can do with the data, and how the data will be protected when a breach happens. Thus, unlike the past, not everyone in the marketing department will have full access to a database containing all the organization’s customers.
In addition, organizations will need to create a data dispute resolution process and procedures so those customers who request to remove consent through a DSAR or SSR can do so in a reasonable amount of time and in a manner that is not too time-consuming. Also, reports should be reviewed on a periodic basis concerning who is handling and managing customer information.
Step 5: Create and Monitor a Data Retention Policy
A Harris Poll conducted last year indicated that 63% of employees do not believe that their companies have policies regarding email retention. Because storing data has become so inexpensive and because there was no compelling reason to sift through analyze petabytes of data across the organization, companies simply didn’t delete data without a good reason.
Wikipedia has an excellent definition of a data retention policy, “The objectives of a data retention policy are to keep important information for future use or reference, to organize information so it can be searched and accessed at a later date and to dispose of information that is no longer needed.”
Do you have a plan to use the data you are collecting?
This is the critical question organizations will have to answer and document in their data retention policy. Most organizations will likely improve in terms of collecting, handling, and managing PII, however, the difficult part after they get all the PII “marbles on the table” will be how they deal with data that may have no value but poses some risk to the organization.
Step 6: Maintaining and Demonstrating Ongoing Compliance
Last step: You know where the PII is in your organization, you estimated its value and cost, you created policies and procedures concerning how it is handled and managed, and you figured out whether or not it should be retained and for how long. It is not an easy process and for many organizations; steps 1 through 5 could take quite a bit of time.
Compliance will require ongoing, nearly continuous improvement and maintenance Organizations will need to continue to assess policies and procedures to understand their effectiveness. For CCPA, GDPR, and other fairly new compliance regulations, we will likely get new provisions added and clarity on other provisions through legislation and through the courts. While I wouldn’t watch the news nightly to look for changes, an annual audit should be enough to update your compliance policies and procedures with changes.
Privacy regulations are evolving and expanding. As you build your program, you will need to be forward-thinking to address new privacy challenges that will inevitably arise from the locations in which you currently operate a business and/or the areas you plan on entering. A good example is that not all privacy regulations currently require subject consent for data collection, but the number of geographies requiring consent is increasing. Consider this part of your plan as a data collection best practice.
Use these guidelines to help address operational aspects related to data prepared for the swath of globally expanding privacy legislation.
Conclusion
Hopefully, this article was helpful in creating a process to help navigate the process of dealing with and securing your organization’s sensitive data. We’ll list the steps below just so you can review them again after having read through all the detail.
We hope this series on privacy, data compliance, and dealing with CCPA, GDPR, and other privacy legislation will provide the information you need to created robust programs that will minimize risk, improve data security, and create an efficient process of handling and managing the sensitive data that you collect.
- Step 1: Identify and Map PII
- Step 2: Organizational, Data and Policy Assessment
- Step 3: Understand the Risk of Managing and Storing PII
- Step 4: Design Controls and Procedures to Manage PII
- Step 5: Create and Monitor a Data Retention Policy
- Step 6: Maintaining and Demonstrating Ongoing Compliance
Please let us know if you have any questions concerning data privacy and compliance management. We would love to help your organization.







