Verizon’s 2019 Data Breach Investigations Report (DBIR) – Preventing Public Sector Attacks
On May 8, 2019, Verizon released the 12th edition of its Data Breach Investigations Report (DBIR) in which Verizon’s researchers studied 41,686 security incidents. Analysts found that 2,013 of those incidents were data breaches in that information was compromised.
One of the most interesting findings in the report this year is that public administration saw a disproportionately larger number of security events during Verizon’s reporting period this year – they were the victims of 56% of all analyzed security incidents. The sector also accounted for 16% of all publicly disclosed data breaches.
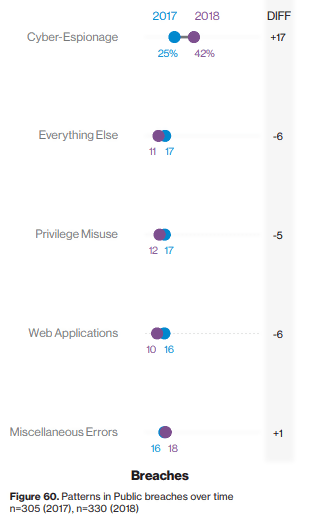
Details about these public sector security incidents indicate that digital espionage was the most common attack pattern for this industry. Espionage played a pivotal role in 42% of data breaches reported by public organizations, a 168% increase from 25% of all breaches in the report the previous year.
Source: 2019 Data Breach Investigations Report
Interestingly, the motivation for the vast majority of attacks is not espionage rather the motivation is financial. In fact, 71% of breaches are all breaches in the Verizon data set were financially motivated. Attackers sell personal data or PII, email addresses, log-in credentials and credit card numbers. They also use the stolen data to steal victim identities and commit direct fraud. In many breaches, multiple types of data are compromised in attacks outside public administration.
Verizon’s analysis shows that external attackers were primarily responsible for public sector data breaches, however 30 percent of security incidents with confirmed data disclosure involved internal actors. Meanwhile, partners were involved in only 1 percent of public sector security incidents. The bottom line is that state-affiliated actors were responsible for the vast majority of public administration security events.
The main issue with an insider threat incident is the massive cost. On average, the cost of a breach activated by an insider in an agency is $8.7 million. Agencies are investing millions of dollars to combat the risks associated with insider threats. The United States government alone has invested more than $1 billion per year on countermeasures, such as founding the National Insider Threat Task Force.
The Public and Private Sector – Collaboration and Incident Prevention
The public sector provides critical infrastructure that millions of citizens rely on for living their day-to-day lives. Even though public sector agencies often work closely with private sector organizations such as MITRE, Verizon’s public sector findings stand in stark contrast to their private sector findings.
Again, attackers were primarily financially motivated when targeting private sector industries. These bad actors are more interested in how much money they can get for selling an organization’s stolen data than learning what secrets that data could reveal.
The more staggering difference between the public and private sector findings is that security professionals in the public sector are 2.5 times more likely than those in the private sector to take years to discover that a data breach has occurred.
As the threat landscape continues to evolve, many organizations are looking towards sharing research, data, and intelligence across both the public and private sector. The Department of Homeland Security, for example, has a free and voluntary Automated Indicator Sharing (AIS) capability that allows bidirectional sharing of cyber threat indicators.
How Public Organizations Can Defend Themselves Against the Insider Threat
Over $1 billion has been invested in protecting U.S. agencies against the insider threat. Verizon’s 2019 DBIR highlights IT areas in which public sector agencies need to begin strengthening their digital security.
Increase Email Security
According to Verizon’s findings, of all the malware attacks in every sector, email was used as a delivery method 94 percent of the time. Implementing these four technology controls will bolster email security:
- Control access to email attachments. Prevent unrestricted access to email attachments on vulnerable and unmanaged devices, such as in a bring-your-own-device environment.
- Ensure the confidentiality of email communications. Enable the secure delivery of communications using encryption.
- Protect end users from spam and phishing attacks. Detect unwanted spam and unsafe phishing emails. The majority of attacks on organizations in both the public and private sector are phishing, spearphishing, and whaling e-mails sent to unsuspecting victims.
- Educate users through security awareness programs. Teach users about phishing and social engineering through standardized security awareness training. Studies indicate that even basic training with reminder e-mails from the IT security team will reduce successful attacks by more than 60% in most organizations.
Implement Change Control and Continuous Monitoring
Using change control in conjunction with continuous automated monitoring allows organizations and agencies to more efficiently and effectively detect an insider threat. These two tools combined can enable organizations to:
- Detect user actions within IT infrastructure in real-time using event-driven data collections on end-user machines, servers, and networks.
- Validate changes by using attribute matching, which provides a high level of control for protection purposes while maintaining a high level of operability for system administrators.
- Enforce policies surrounding the identification, delegation, notification, and remediation of security threats through violation notifications.
- Report on policies using an integrated data repository which acts as a single authoritative source.
Reduce the Attack Surface
Attack surface refers to the total number of resources exposed to attackers within an agency or organization. New technology such as cloud computing and software-defined networking has exponentially increased the attack surface that organizations now face.
The previous two controls that we discussed, will help work to defend the attack surface of complex infrastructures, but the best defense is actually reducing the attack surface of an agency or organization.
These five methods can begin the process of attack surface reduction:
- Eliminate unnecessary complexity and thereby reduce technical policy mistakes, stagnant and outdated rules, and overly permission rule definitions. Unnecessary complexity increases the probability of human error, which opens up an organization to both internal and external threats.
- Visualize your vulnerabilities by creating a real-time model using attack surface modeling, attack simulation, and patch simulation.
- Manage your endpoints by monitoring independent processes, sending automated notifications when suspicious behavior is detected, and implementing endpoint control policies.
- Segment your network and increase the number of barriers an attacker will encounter in your infrastructure. Network segmentation helps reduce the attack surface and minimizes dwell time by stopping attackers in their tracks.
- Prioritize analytics, such as security configuration assessments, traffic flow analysis, and quantitative risk scores.
Conclusion
Cyber espionage is becoming more and more prevalent. The UK’s Government Code and Cipher School (GCCS) estimates that at least 34 nations have well-funding cyber espionage teams that attack from the outside, and it’s only a matter of time before that threat also evolves to include empowered insider threats.
The 2019 Verizon DBIR provides a vital insight into public sector attacks and allows us to determine the best steps to take for preventing insider threats. By increasing email security, implementing change control, improving continuous monitoring, and reducing the attack surface, public sector agencies and organizations will be able to better defend themselves against both internal and external threats.