The Difference Between a Penetration Test and Vulnerability Assessment (2 of 2)
What is the Difference Between a Penetration Test and Vulnerability Assessment? Part 2 of 2 Comparing Penetration Tests and Vulnerability Assessments In part 1 of this post, we focused on the Vulnerability Scans,
The Difference Between a Penetration Test and Vulnerability Assessment (1 of 2)
What is the Difference Between a Penetration Test and Vulnerability Assessment? Part 1 of 2 Comparing Penetration Tests and Vulnerability Assessments The staff here at SecureOps is consistently asked the purpose and the
Intensity and Diversity of Attacks Are Paying Off for Cybercriminals
The REAL State of Cybercrime Cyberattacks have been expanding rapidly over the past decade; according to Juniper Research, the costs of cybercrime are estimated to reach over $2 trillion in 2019.
60% of Businesses Have Experienced a Breach in the Past Two Years
IT security professionals have seen the number of breaches as well as the percentage of organizations that admit to being breached increase year after year. However, Vanson Bourne, a UK-based
Cyber-Attacks Rank First as Company Worry
Cyber-attacks are the top concern among businesses of all sizes globally for the first time since the Travelers Companies’ survey began 5 years ago. The research was conducted by Hart Research
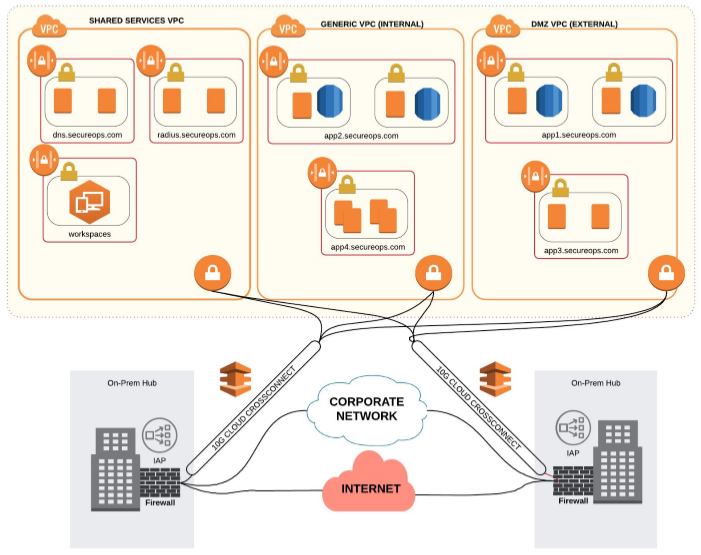
The 4 Key Benefits of Micro-Segmentation
Getting Started with Micro-segmentation Written by Javier Hernandez, Senior Security Architect @ SecureOps What is Micro-Segmentation Micro-segmentation is an emerging security best practice that offers a number of advantages over more established approaches
Critical Cybersecurity Statistics You Must Know
We just posted a 24-page report packed with dozens of remarkable statistics about the IT security industry. We are providing a summary of the top 10 most interesting statistics here
Vulnerability Management – A Best Practice
3 Keys to Effective SMB Vulnerability Management Small and medium-sized businesses have been facing an increased number of threats from cyberattacks over the past several years. According to Verizon’s 2019 Data
Unleashing Bug Bounty Programs
How to use Vulnerability Assessments, Penetration Testing, and Bug Bounty Programs Together to Improve your Security Posture An Interview with Jasmin Landry, Sr Cyber Security Engineer at leading MSSP SecureOps Jasmin Landry
Four Factors that will Change Cybersecurity
Cybercrime is changing according to the Accenture Threatscape Report. New threats from Ransomware, crime syndicates and vulnerabilities in the cloud may create havoc.