Stopping Corona Virus Cyber-Scams Before They Start
How to Identify Corona Virus Cyber-Attacks
This blog post was written to help our customers and readers of our blog identify scams that were created by cybercriminals to leverage the Corona Virus pandemic that we are all trying to endure. This blog post WAS NOT written to fearmonger or increase the stress we are feeling from the impact this illness is having on us from a health, economic, and personal perspective.
Corona Virus Cyber-Scam 1 – AZORult Malware
The Corona Virus or COVID-19 is, as every other emergency or urgent political, business or economic issue, has provided hackers the opportunity to infect our computers. In our first example of a Corona Virus cyber-scam, the criminals are infecting computers with the AZORult malware.
While the AZORult malicious code has existed for some time, the US Government issued warnings that cyber-scams using malware like AZORult would increase as the malware was being packaged for “script kiddies” and would be available for sale on the black market. In addition, as emails and websites with information about the virus increased, our ability to accurately identify phishing or watering-hole attacks would ultimately decrease.
The malicious online map, found at www.Corona-Virus-Map.com, appears very polished and convincing, showing an image of the world that depicts viral outbreaks with red dots of various sizes, depending on the number of infections. The map offers a running total of confirmed cases, total deaths and recoveries by country. It cites Johns Hopkins University’s Center for Systems Science and Engineering as its supposed data source.
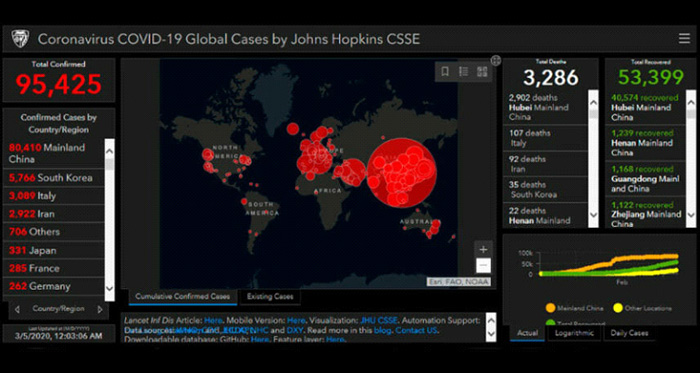
The malware, found within a file called corona.exe, carries typical AZORult functionality; the malware has the capability to steal personal information or PII like log-in credentials, credit card numbers, cookies, and other browser data. The malware can also take screenshots, uncover a victim’s public IP address, and gather specific information on infected machines, including the OS system, hostname, and username.
Where Did the AZORult Trojan Come From?
According to Digital Shadows, in February 2020, a user initiated a discussion on the Russian cybercriminal forum XSS to advertise a method to deliver malware via an email attachment disguised as a John Hopkins map of the virus’s outbreak. The offering was priced at $200 for a “private build”, and if buyers also required a Java CodeSign certificate, the price would be $700.
In this case, the cybercriminals provide an online and a full working map of the COVID-19 global infection rate by country. The map is resizable, interactive, and buyers are lured by the real-time data. Further, they believe the data is provided from the World Health Organization (WHO) as well as other high-integrity sources. The victims think that the “pre-loader” is the actual map, however by opening the map they download the malicious code onto their system.
The Cyber-Infrastructure (CERT) organization within Homeland Security in the United States warned against such scams and recommended to only use government sources like the CDC website on the Corona Virus here: https://www.cdc.gov/coronavirus/2019-ncov/index.html
Removing the AZORult Malware from Your System
Research shows that cybercriminals typically spread this malware using spam email campaigns. The emails typically contain deceptive text to trick users into opening attached files like fake job application forms delivered in Microsoft Word. Thus, embedding the trojan into the map is a fairly new tactic.
PC Risk suggests, “if you think you have recently opened suspicious email attachments or see the “sAMsUNg” process in Windows Task Manager, there is a high probability that your computer is infected with AZORult malware. If so, you should immediately scan your system with a legitimate anti-virus/anti-spyware suite and eliminate all detected threats.” They also provide excellent information about how to manually uninstall the malicious code and recommend automated anti-virus products that will do the job as well: https://www.pcrisk.com/removal-guides/13200-azorult-virus
Corona Virus Cyber-Scam 2 – CovidLock, Android Ransomware
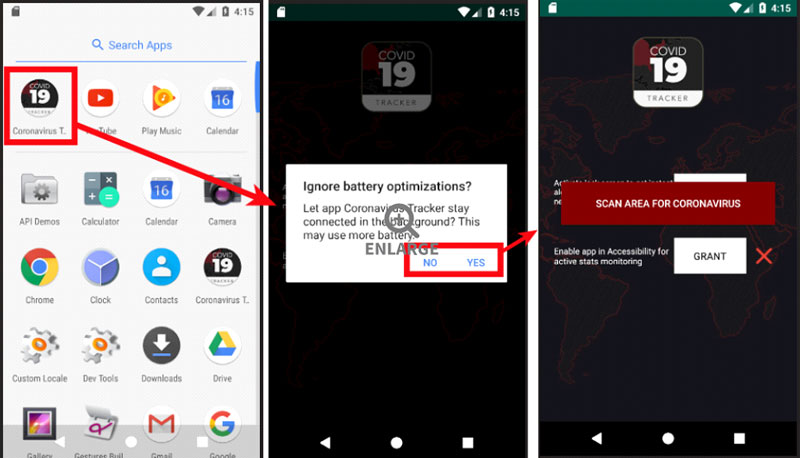
The CovidLock Ransomware again leverages a Corona Virus map tracking scam to spread the malware. An Android app available at coronavirusapp[.]site claims to provide access to a map that provides real-time virus-tracking and information, including heatmap visuals and statistics. However, the map, as you may have guessed contains the CovidLock Ransomware. CovidLock uses techniques to deny the victim access to their Android phone by forcing a change in the password used to unlock the phone. This “screen-lock” attack has been seen before on Android ransomware, however, this specific strain is fairly new.
CovidLock criminals charge about $100 in bitcoin to unlock infected devices. Since version 7, Android has provided protection against screen-lockout attacks, however, only if users have set a password to lock their device screens, to begin with. Meaning, if they didn’t set up a screen lock password they are susceptible to the attack. DomainTools researchers have reverse engineered the ransomware and plan to release decryption keys that will unlock phones for free.
Until the decryptor keys are released Zscaler does a good job of explaining how to remove CovidLock from your Android phone here: https://www.zscaler.com/blogs/research/covidlock-android-ransomware-walkthrough-and-unlocking-routine
Corona Virus Cyber-Scam 3 – Phishing Campaigns
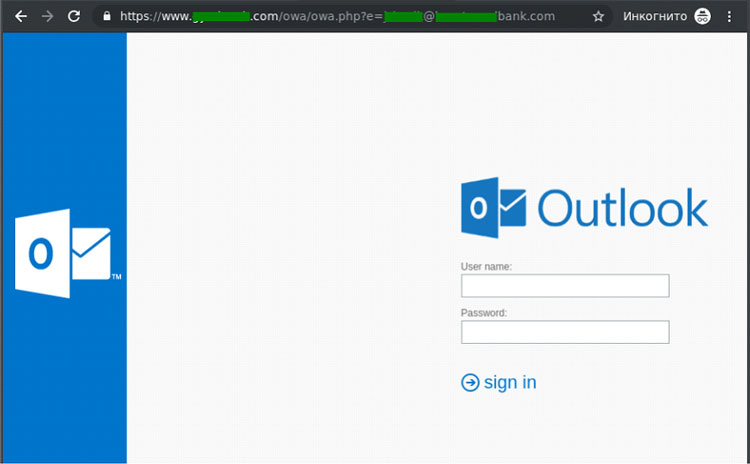
This Office 365 phishing attack leverages the ongoing news of universities canceling classes, moving them online, or shutting down entirely due to the Corona Virus infections. The attacker creates an email that looked as though it was coming from a university’s board of trustees and directed users to a webpage with updates on the attack from the university’s “health team.”
As with most phishing attacks, the URL written in the email does not match the actual URL to which students were directed. The URL directed students to a page that was spoofed to look like an Office 365 login page. The cybercriminal’s strategy is to convince the student that they had been logged out of Office 365 and to re-enter their log-in credentials to re-gain access to their account.
The attackers use the stolen log-in credentials to steal other personal information (PII) in the student’s Office 365 including searching through e-mails and browser information and either sell the information on the dark web or use it to open accounts and make fraudulent purchases.
Conclusion
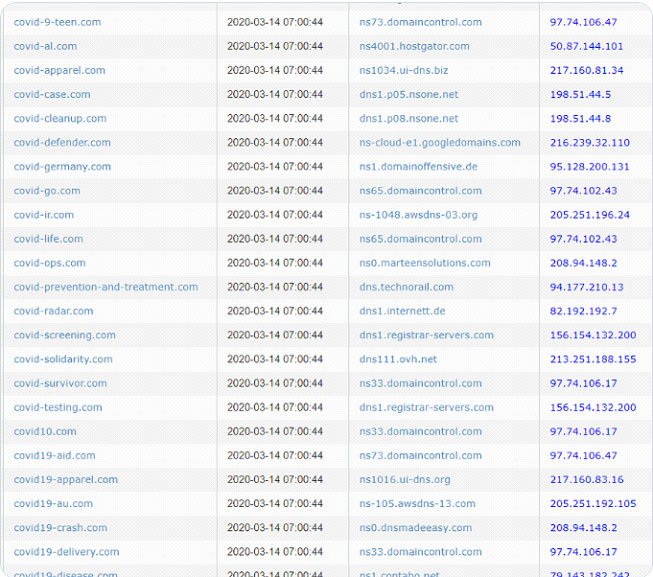
We have seen new domain purchases related to the Corona Virus increase dramatically in the past several weeks as you can see from the image below provided by Sophos. Certainly, many of the domains are legitimate and provided serious information about the virus and its effects on our personal lives, however many are intended to harm.
Please use the following pieces of advice from our team here as well as other thought leaders in IT Security to stay safe from these attacks:
- Check e-mail addresses from the sender and look for misspellings or extensions that may not be legitimate – cdc.org rather than cdc.com for example.
- Check the actual URL of the link. If you hover over the link without clicking on it, you’ll see the actual URL address that you are being directed to – make sure this is a legitimate site.
- Check the design of the page that you were directed to. The official Microsoft Outlook website actually looks completely different than the image of the one above. And, no website other a website with a Microsoft domain should ask for your Outlook credentials.
- Be wary of e-mail attachments, particularly MS Office docs – criminals are notorious for hiding malware in attachments.
- Do not download mobile or desktop programs from sites that even have a hint of illegitimacy. Use Google Play or the App Store.
- Keep your computer and phone updated with the latest software updates. Criminals use software vulnerabilities to attack your system.
- Run your anti-virus software regularly. Antivirus software is consistently being updated to identify and mitigate new attacks.
We hope this information helps keep you protected from the Corona Virus related cyber-scams and certainly wish you, your family and friends the very best.






