5 Steps to Uncovering Malware on Your Network
How to Detect Malware and through Anomalous Behavior on the Network
According to a recent Symantec survey, 90% of CIOs believe they are wasting millions of dollars on insufficient cybersecurity, while 87% believe their security measures are not adequately protecting their business. (Source: https://bestvpn.org/cybersecurity-statistics/)
Despite the increased use of Antivirus, Firewalls, Endpoint Security, and other security technology that makes up the “layered” security approach that most organizations use; malware is entering networks and doing damage at an increased rate.
The question most CISO’s and heads of security are asking is how is malware evading my organization’s defenses and what can I do to eliminate the malware before it does damage?
Let’s look at the research published by CSO Online last month:
- 94% of malware is delivered via email
- Phishing attacks account for more than 80% of reported security incidents
- $17,700 is lost every minute due to phishing attacks
- 60 percent of breaches involved vulnerabilities for which a patch was available but not applied
- 63 percent of companies said their data was potentially compromised within the last year due to a hardware or silicon-level security breach
- Attacks on IoT devices tripled in the first half of 2019.
- Fileless attacks grew by 256 percent over the first half of 2019
These statistics point to one fact; malware is infiltrating networks in ways that perimeter technology was not designed to defend. For example, 1 in 7 emails that are sent contain a malicious link or attachment. Firewalls and other perimeter technology are not specifically geared to defend against e-mail communication. Further, secure e-mail gateways and other content filtering security devices can’t keep up with the increasing sophistication and diversity of malicious code.
Perimeter Defenses are NOT Stopping Malware
While experts discuss and implement a wide range of solutions to stem them from attacks, two facts are clear:
- Current perimeter technology is less than effective against advanced persistent malware
- Malware’s effectiveness is evolving faster than is the effectiveness of security defense.
Hundreds of breaches, including attacks on Fortune 100 organizations and massive government bureaucracies with the best security technology and IT security organizations have shown that leveraging best practices in IT security will not stop all attacks.
The 5 key methods to detect malware and anomalous network behavior that we introduce in this blog will provide a framework for identifying and eliminating malware from your network. The recommendations are based on 20 years of static and dynamic malware analysis by leveraging the data from sandboxes and the study of thousands of samples of advanced malware.
Note: What is a Sandbox – In cybersecurity, a sandbox is an isolated environment on a network that mimics end-user operating environments. Sandboxes are used to safely execute suspicious code without risking harm to the host device or network.
Using a sandbox for advanced malware detection provides another layer of protection against new security threats—zero-day malware and stealthy attacks. For this study, sandboxes were used by researchers to study the effects and behavior of malware on the network.
For this study, sandboxes were used by researchers to study the effects and behavior of malware on the network.
The 5 Key Ways to Detect Malware through Anomalous Network Behavior
Here’s a quick look at common malware problems and the solutions that help fix them. We dive into these topics in detail below.
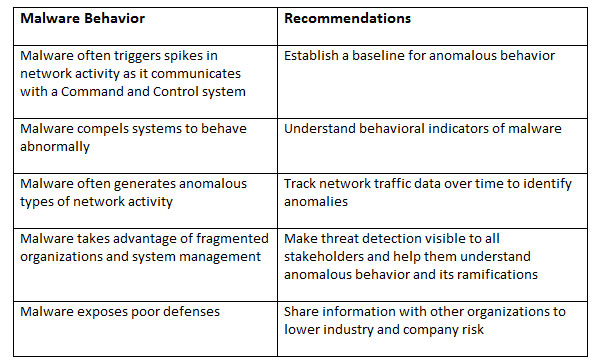
Let’s dig a little deeper into the 5 key ways to identify malware when it has already infiltrated the network.
Establish a Baseline for Anomalous Behavior
Organizations must establish a baseline for normal network traffic, including both human and machine data. Once security analysts have developed an understanding of what is normal, they are able to understand normal traffic flow, patterns, and behavior. These baseline measures, just like any limit, level, or ceiling, can be used to trigger alarms or notifications for further analysis. Attackers today feel as though once they are safely in an environment they have little risk of being discovered. Creating baselines significantly increases the likelihood that security analysts will uncover spikes in traffic.
Understand Behavioral Patterns or Indicators of Malware
Now that a baseline for normal traffic has been established, the next step is to understand the behaviors of malware. Any network traffic or behavior that crosses over the traffic flow, patterns, or behavior that were established in step 1 will trigger an investigation.
The investigation will focus on victim-zero and the behavior of the suspected malware on their system. An understanding of fundament malware behavior is critical to scope and stop the attack’s advance. Essentially investigators are looking for IOCs or indicators of compromise in these first two steps.
Learn more about IOC’s here: https://www.darkreading.com/attacks-breaches/top-15-indicators-of-compromise/d/d-id/1140647
Track Network Traffic Data Broadly and Over Time
Step 3 is about using the baselines and malware behavior data to take a time-based view of network activity to find malware on the network. With a solid understanding of the system and human baselines, analysts can view network traffic over time to identify anomalies or, more importantly, to understand if a breach has occurred and how to scope the attack advancement.
By analyzing network traffic going to suspicious domains, security analysts could detect malware infections weeks or even months before they’re able to capture a sample of the malware. In fact, in numerous studies, the malware was on the network for weeks doing damage before it was found and eliminated.
Make Threat Detection Visible to IT Security Staff
Communication gaps have surfaced as security solutions have fragmented in the environment to address firewalls, IDS/IPS, packet sniffers, endpoint solutions, and others that now comprise an organization’s layered security solution. Individual reports or analyses need to be combined to provide a comprehensive picture of the activity and health of the network. Thus, effective security defense requires security teams to evolve to become consultants who provide information to security team members who manage the system logs, firewalls, IDS/IPS tuning, and more.
Threat Intelligence Sharing Has Improved but We Need More
One of the major advantages attackers exploit is the failure among competitors across industries to share threat intelligence. Specifically, organizations in the same industry view one another as competitors and rarely share threat information between security teams. This approach has clearly damaged organizations as ransomware attacks that have devastated hospitals, government agencies, and now manufacturers. They could have been mitigated with threat intelligence sharing.
Conclusion
The IT Security industry has clearly understood for some time that phishing is the most used and successful attack vector and further, that perimeter technology is a poor record defending it. Unknowing users click on a link or attachment and malicious malware is released onto the network and more times than not; security technology inside the perimeter cannot mitigate the attack before damage has been inflicted.
Creating a traffic and user behavior baseline, establishing a sensible network and system limit, understanding malware activity and behavior are key to exposing malware before it does damage. Further, developing a model of sharing internally across the IT Security team and externally with partners and competitors alike will provide a higher level of visibility concerning attack and defense trends and innovation.
In a future blog post, we will dig into Network behavior analytics (NBA), or network behavior anomaly detection (NBAD). This network traffic analysis approach focuses on behavior patterns attributed to a variety of systems and technologies (i.e., machine ids, IP addresses, etc.) associated with the network. This analysis is like the analysis that we discuss in the post, however, it relies on big data and automated data analytics. We wanted to stay fundamental for now and simply introduce the theory.
We hope this process helps you and your IT security organization network behavior analysis in 5 easy steps. If you have questions, you can certainly reach out and we’ll be glad to help you put a process or solution in place.







