Why and How DNS Hijacking is Increasing
The IDC Global DNS Threat Report released last summer revealed that 82% of organizations were victims of DNS attacks with each suffering an average of 9 DNS attacks which was an increase of 34%. In addition, over 63% of the attacks caused application downtime and the average cost per attack increased by 49% to almost $1.1M. This means that one in five businesses lost over $1 million per attack!
What is DNS Hijacking?
It basically works as follows:
- You type in a website’s address in the URL bar (like “SecureOps.com”).
- Your device will send a query to a DNS server asking what SecureOps.com’s IP address is.
- The DNS server tells your device what the IP address is.
- Your device uses that IP address to connect to Google’s website.
DNS Hijacking occurs when a cybercriminal takes over the server of the destination site and pretends to be that site, like your bank. You enter your sensitive information on the site just as though it was actually your bank’s site (this is now a man-in-the-middle attack) and the criminals collect your information and get rich by using it to buy merchandise or simply impersonate you.
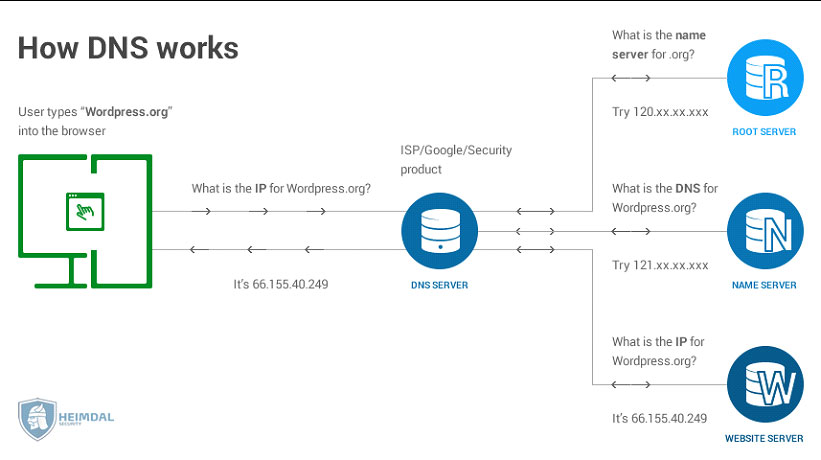
Image Provided by Heimdal Security
Why is DNS Hijacking Increasing?
Based on the IDC report and recent other breaches DNS attacks appear to be increasing and spreading in terms of diversity and intensity. For example, this week a variety of cyberattacks targeting governments and other organizations in Europe and the Middle East are believed to have been cybercriminals acting on behalf of the Turkish government.
These attacks involve intercepting internet traffic which may have allowed hackers to obtain access to the networks of government organizations and perhaps other organizations. The hackers used DNS hijacking as described which redirected visitors to imposter websites that they cybercriminals created to collect sensitive data. As we suggested earlier, many of the imposter websites mimicked authentic websites and the victims entered sensitive information like usernames, passwords, credit card numbers, social security numbers or other text.
According to the IT security experts that studied the attacks, all of the victims had traffic to their websites hijacked. Most of the traffic was visiting login portals for email services, cloud storage servers, and online networks.
Examples of DNS Attacks and DNS Hijacking
Let’s provide a couple more examples of DNS attacks and then get into how they work:
In October of 2016, hackers used DNS hijacking to redirect traffic to all 36 of a Brazilian bank’s domains, according to an analysis by the security firm Kaspersky. For as long as six hours, they routed all of the bank’s visitors to phishing pages that also attempted to install malware on their computers.
In another DNS hijacking incident in 2013, hackers known as the Syrian Electronic Army took over the domain of the New York Times, Financial Times and Washington Post and shut them down for hours. And, of course, in perhaps the most notorious DNS attack in history, cyber-criminals controlling the Mirai botnet used compromised IoT devices including CCTV cameras to attack servers of the DNS provider Dyn with a massive amount of traffic in a DDoS attack. It’s not exactly a DNS hijacking attack so much as a DNS interruption, but one that caused Amazon, Twitter, and Reddit to go offline for hours.
Finally, last year, a criminal organization named Sea Turtle carried out a broad campaign of espionage via DNS hijacking, hitting 40 different organizations. Cisco believes, the targets were a collection of mostly governmental organizations, including ministries of foreign affairs, intelligence agencies, military targets, and energy-related groups, all based in the Middle East and North Africa.
DNS Hijacking Allows Criminals to Send Victims to Fake Websites to Collect Sensitive Information
In the attacks on behalf of Turkey this week the attackers corrupted the internet’s directory system and hackers were able to silently use “man in the middle” attacks to intercept all internet data from email to web traffic sent to those victims organizations. They used fake or stolen SSL certificates to make their attack look like legitimate.
DNS hijacking, DNS poisoning, or DNS redirection is the practice of subverting the resolution of Domain Name System (DNS) queries. Cyber attackers can use malware typically delivered through a phishing attack that overrides a computer’s TCP/IP configuration and points any request to a rogue DNS server that is controlled by the criminal. The server can then send them to any IP address they choose – usually, a fake one that will attempt to collect sensitive data.
DNS Hijacking Attacks Send Users to Fake Sites Operated by the Criminals
One of the functions of a DNS server is to translate a domain name into an IP address that applications need to connect to an Internet resource such as a website. This functionality is defined in various formal internet standards that define the protocol in considerable detail. DNS servers are implicitly trusted by internet-facing computers and users to correctly resolve names to the actual addresses that are registered by the owners of an internet domain.
DNS is not just a technical service running on recursive and authoritative servers in the cloud and the internet. It’s also a naming system where authority is key for the system to be organized and coherent. Domains are managed by specific entities called registrars; they are the guardians of the internet so to speak. But if the information on a domain at the registrar level is corrupted or changed by malicious activity, the whole DNS system essentially fails.
Conclusion – How to Protect Yourself from DNS Attacks
Let’s try and itemize these and list them out with an explanation as briefly as possible:
- Eliminate Vulnerabilities – Just like most cyber-attacks, DNS Hijacking uses phishing or some other scam to get you to give their malware access to exploit a software vulnerability.
- Social Engineering – Again, just like so many attacks, an e-mail is typically opened which will either have a link to a malicious site or a file to download that will install malware on your system. Be careful not to open suspicious e-mail and screen which sites you visit.
- Web Content Filtering – Filters will essentially send traffic through an intelligence database that will stop redirects, exploit kits, malicious downloads and more.
- Router Security – Believe it or not many folks don’t change the usernames and passwords of the routers from the factory settings. Also, they may not update the firmware which creates vulnerabilities.
Obviously, there are many other defense measures you could put in place to protect your organization including integrated, end-to-end change management under a single system. This will help in protecting an organization’s DNS. The system should include secure, multi-factor password access. Zero trust implementation can keep attacks from moving throughout the organization.
Ok, let’s stop here, for now, however, please add your comments below if you have questions or just want to make a point. We are here to learn from one another, and we are always looking to learn.
To Learn More About How to Protect Yourself from DNS Attacks Please Call Us – as Always We Are Happy to Help – 1 (888) 982-0678







