Bug Bounty Programs are Becoming Increasingly Effective
What is the Difference Between Bug Bounty and Vulnerability Management Programs?
In this blog, SecureOps Senior Penetration Tester Jasmin Landry has provided us deep insight into bug bounty programs in two previous posts:
Bug Bounty Programs – Uncovering Critical Vulnerabilities
https://secureops.com/penetration-testing/bug-bounty/
Unleashing Bug Bounty Programs
https://secureops.com/penetration-testing/bug-bounty-programs/
To provide a bit of background, Jasmin leads SecureOps clients with their vulnerability management, pen testing, and bug bounty programs. He is certified in CEH or ethical hacking, GWAPT, and has an OSCP certification from Offensive Security. In addition, he is #48 all-time on Bug Crowd’s rankings – here is a great picture of Jasmin on the Bug Crowd website. In addition, he is ranked in the top .1% in HackerOne’s all-time rankings of their top bug bounty participants.
Vulnerability Assessments, Penetration Testing, and Bug Bounty Programs
In Jasmin’s interview in the “Unleashing Bug Bounty Programs” blog post Jasmin suggested that a vulnerability assessment is the process of identifying, quantifying, and prioritizing the vulnerabilities in a system. Vulnerability assessments will include the prioritization of each system with systems holding PII or other critical data landing at the top of the list. He further suggested that vulnerability management is the systematic process of scanning and eliminating vulnerabilities by priority.
We also discussed the role of Penetration Tests which Jasmin suggested is an ethical hacking exercise and an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system and perhaps the entire IT environment. A pen test will typically identify the target systems and a specific goal, such as stealing PII – the sensitive, personal information of the organization’s customers. Depending on the type of pen test, the ethical hacker may have almost zero information on the system and will undertake various means to attack the system and steal the information. Pen testing is a point-in-time exercise geared specifically to uncover an organization’s weaknesses against diverse cyber-attacks.
A bug bounty program is a reward offered by an increasing number of organizations and software developers. Folks like Jasmin who participate in the programs receive recognition and compensation for reporting bugs, especially those that are unknown (Zero-Day) and vulnerabilities or exploits that are critical and could be target by hackers to do significant damage. Bug Bounty programs are specifically geared to supplement vulnerability assessments and penetration tests by adding an ongoing practice of scouring software programs to find “unknown” vulnerabilities.
Hackers working on the Bugcrowd platform prevented $8.9B of cybercrime in 2019. In the next five years, hackers on the Bugcrowd platform are projected to prevent more than $55 billion in cybercrime for organizations worldwide.
I quoted “unknown” vulnerabilities because “known” vulnerabilities should be found and patched in the process of conducting a sound vulnerability assessment and management program. Last year we saw 22,000 vulnerabilities published by the CVE which is 3 times as many as they published in 2016 and nearly 8,000 more than they published in 2017. Once published by the CVE, these “unknown” vulnerabilities become “known” vulnerabilities and vulnerability scanning should identify them.
Why are Bug Bounty Programs Critical to Preventing Cyber-Attacks?
A software vulnerability that can be exploited to steal sensitive information or simply to provide access to an organization’s systems is making cyber-criminals rich. The market for zero-day software vulnerabilities had been growing steadily over the past several years, however, since the Covid-19 pandemic started the market for the bugs has exploded. In the black market, an operating system vulnerability may be worth more than $1 million.
The FBI reported a 400% rise in cybercrime after COVID-19 was declared a pandemic and organizations are investing more in bug bounty programs as a result. More than half of hackers (61%) have noticed an increase in available bug bounty programs to participate in due the increased number of remote workers related to the Coronavirus.
New malware is being created constantly; 360,000 new malware files a day are documented by anti-virus companies. While many of these new malware programs or malicious code are simply rehashes of previous malware programs that have been changed just enough to make antivirus programs useless to defend against them, new malware is being deployed at an increased pace as well.
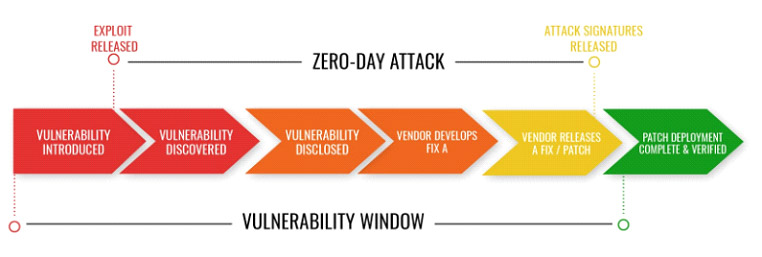
How most cyber-attacks work leveraging new malware is hackers write code to target a specific security weakness. They package it into malware called a zero-day exploit. The malicious software takes advantage of a vulnerability to compromise a computer system or cause some unintended behavior. In most cases, a patch from the software developer can fix this, however, if the bug doesn’t cause the software to malfunction in some way, developers are often times not made aware of the bug until after it has been used by criminals to breach an organization.
Programming bugs and unanticipated code interactions are among the most common security vulnerabilities; criminals are constantly probing systems to find the bugs and exploit them. Unfortunately, predicting the creation of these vulnerabilities is difficult because there are almost no limits to the number of combinations of software that are used on a single system and a network will have literally countless numbers of bugs.
To be clear as possible, a computer system vulnerability is a flaw or weakness in a system or network that could be exploited to allow an attacker to manipulate the system or cause damage, in the case of a ransomware attack for example. These vulnerabilities can exist because of unanticipated interactions of different software programs, system components, or security flaws in a specific software program.
Bug bounty programs were created to find these Zero-day exploits that vulnerability scanners are not able to uncover. And as more Zero-days or unknown vulnerabilities are created because of an increase in software, systems, IoT devices and the digital transformation in general, the more organizations will need the good guys in the bug bounty programs to defend against the bad guys. Also, the number of bad guys is clearly increasing, and they are becoming more sophisticated, so the Jasmin’s of the world must increase just to keep the playing field level.
How are Organizations Benefitting from Bugcrowd and HackerOne Bug Bounty Programs?
Bugcrowd, the #1 crowdsourced bug bounty security company, released its 2020 Inside the Mind of a Hacker report, which has become known as the most comprehensive study on the global hacking community. The Inside the Mind of a Hacker Report analyzes 3,493 survey responses from active “good guy,” “white hat” or non-criminal hackers, plus hacking activity on the Bugcrowd platform between May 1, 2019, and April 30, 2020, to highlight insights from its growing and incredibly intelligent cybersecurity workforce. The report incorporates data from 1,549 programs and 7.7 million platform interactions to provide a striking and in-depth view of emerging trends among Bug Bounty, Penetration Testing, Attack Surface Management, and Vulnerability Disclosure Programs.

The most interesting finding in my opinion is that almost nine out of 10 hackers, 87%, say that vulnerability scanners cannot find as many critical or unknown assets as skilled hackers. While last year was a record year for data breaches, the report found that hackers working on the Bugcrowd platform prevented $8.9B of cybercrime last and earned 38% more than they did in the prior year. In the next five years, hackers on the Bugcrowd platform are estimated to prevent more than $55 billion in cybercrime for organizations worldwide.
Almost nine out of 10 hackers, 87%, say that scanners cannot find as many critical or unknown assets as humans
Jasmin’s insight concerning vulnerability scanning leveraging artificial intelligence versus the near-genius hackers at Bugcrowd is this, “hackers will always be one step ahead of AI when it comes to cybersecurity because humans are not confined by the logical limitations of machine intelligence.” Jasmin goes on to suggest, “for example, hackers can adapt four to five low-impact bugs to exploit a single high-impact attack vector that AI would likely miss without the creative flexibility of human decision-making. Experience allows hackers to recognize vulnerable misconfigurations that represent a true risk to organizations without all of the false positives that typically come with AI-powered solutions.”
Jasmin’s interview and other information about Bug Bounty programs, AI-powered vulnerability scanning, and the benefit of human intelligence in finding and eliminating bugs can be found in the following articles:
Yahoo – Bugcrowd Report Highlights Need for Blend of Human Ingenuity and AI-Powered Security Solutions to Protect Critical Infrastructure
Security Informed Online Magazine – Bugcrowd Releases 2020 Inside The Mind Of A Hacker Report
https://bit.ly/2OwLHCI
Security Informed – People – Jasmin Landry’s Profile
https://www.securityinformed.com/people/jasmin-landry.html
Conclusion – Prioritizing Bug Bounty Programs with other Security Programs
One of the key findings of Inside the Mind of a Hacker report’s was that as Jasmin suggested, human ingenuity supported by actionable intelligence of the Bugcrowd platform were found to be critical ingredients to maintaining a hardened, resilient IT environment. In fact, 78% of hackers indicated AI-powered cybersecurity solutions alone are not enough to thwart cyber-attacks in the future.
Organizations typically conduct point-in-time assessments of their systems; either by conducting their own scans and assessments or collaborating with an external provider like SecureOps for a vulnerability scan, web application assessment or penetration test.
Just a note about vulnerability scanners and vulnerability management; there are a variety of both open-sourced (e.g. OpenVAS) and commercial (e.g. Tenable Nessus, Qualys Guard, Rapid7 Nexpose, Core Impact, SAINT scanner) products available. These applications are designed to identify vulnerabilities that may exist within a target by comparing these hosts against a database of known vulnerabilities. The ability to detect vulnerabilities can vary widely from product to product, as the vulnerability databases are managed by the application and not a common repository.
Vulnerabilities are the curse of any organization’s security defense. Vulnerabilities are weaknesses or flaws that increase the risk of attackers being able to compromise an information system.
Vulnerability Management, on the other hand and as we suggested earlier, is the process of identifying, classifying, remediating, and mitigating vulnerabilities. Quality vulnerability management programs are the core security process in any organization. However, as most organizations have learned, setting up the process to manage risk effectively and handle critical patches immediately is another matter.
Basic antivirus can protect against some “known” malware, but a multilayered security solution that uses antivirus, deep-packet inspection firewalls, intrusion detection systems (IDS/IPS), email virus scanners, and employee awareness training is needed to provide a viable level of defense.
That said, vulnerability scanning and management will uncover “known” vulnerabilities for the most part and as Jasmin suggested, “find the low hanging fruit” concerning security flaws. Web application assessments will uncover code that could be exploited, and penetration testing will hopefully uncover any sensitive data that is not protected, vulnerabilities in critical systems, and attack vectors that have not been protected. In the 80/20 world, these are excellent steps to improve your security posture.
However, for organizations whose businesses relies on the protection of its customers, their data and ultimately their privacy, bug bounty programs are critical. The thousands of zero-day or unknown exploits and flaws in software code that these brilliant hackers find was absolutely bound to be used to attack your organization or mine.
There are always going to be insider attacks like the one that may have been the cause of the Twitter Crypto Scam, however, those are few and far between compared to the attacks that leverage both known vulnerabilities or the zero-days that are constantly leveraged by cybercriminals.
To Learn More About How to Defend Against Cyber Attacks or If You Have Been Attacked Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/







