Protecting and Responding to Ransomware Attacks – A Best Practice
Let’s start with the basics: ransomware, a malicious software, poses a significant threat to organizations by encrypting their data and demanding payment for its restoration. This type of attack disrupts business operations and presents management with a dilemma: to pay the ransom or restore operations themselves. Unlike other cyberattacks that steal data for monetization, ransomware demands immediate action and often leaves little time for remediation or communication.
In most cases, ransomware is spread through phishing emails containing malicious attachments, portable computers, exposure to public WiFi, Zero-Day vulnerabilities, and drive-by downloading. Drive-by downloading occurs when a user unknowingly visits an infected website, and then malware is downloaded and installed without their knowledge.
For example, a malware variant known as crypto-ransomware encrypts files and has been spreading through social media platforms such as Web-based instant messaging apps and similar methods. Additionally, newer methods of ransomware infection have been observed. For example, vulnerable Web servers have been used to gain access to an organization’s network.

Figure 1 – NIST’s Ransomware Prevention and Response Infographic
Immediate Download of the Infographic Here
It is crucial for organizations to be educated and prepared to prevent or handle a potential compromise. The National Institute of Standards and Technology (NIST), the Federal Bureau of Investigation (FBI), and the Department of Homeland Security (DHS) offer excellent resources to assist organizations. The recommended steps towards protection include identifying and protecting critical data, early detection of ransomware events, and preparing for response and recovery.
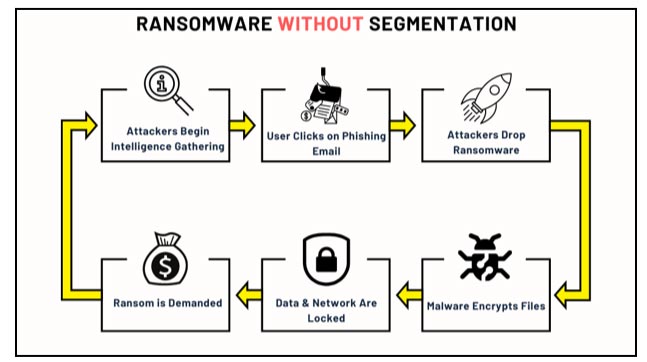
Figure 2 – How Ransomware Encrypts Files Without Network Segmentation
Related Blog Post – “Organizations Struggle Implementing Compliance Requirements, Including NIST & Zero Trust Mandates”
www.secureops.com/blog/implementing-NIST-security-controls.com
Ransomware Protection and Response Resources
- The National Institute of Standards and Technology – https://csrc.nist.gov/projects/ransomware-protection-and-response
- The Federal Bureau of Investigation – https://www.cisa.gov/stopransomware
- Department of Homeland Security – https://www.fbi.gov/how-we-can-help-you/safety-resources/scams-and-safety/common-scams-and-crimes/ransomware
How to Respond and Report a Ransomware Attack to the FBI and IC3
The FBI does not support paying a ransom in response to a ransomware attack. Paying a ransom doesn’t guarantee that you or your organization will get any data back. It also encourages perpetrators to target more victims and offers an incentive for others to get involved in this type of illegal activity.
If you are a victim of ransomware:
- Contact your local FBI field office to request assistance, or submit a tip online.
- File a report with the FBI’s Internet Crime Complaint Center (IC3).
Basic Ransomware Prevention and Response Tips
Even without undertaking all of the measures described in this Ransomware Profile, there are some basic preventative steps that an organization can take now to protect against and recover from the ransomware threat. These include:
- Educate employees on avoiding ransomware infections.
-
-
- Don’t open files or click on links from unknown sources unless you first run an antivirus scan or look at links carefully.
- Avoid using personal websites and personal apps – like email, chat, and social media – from work on computers.
- Don’t connect personally owned devices to work networks without prior authorization.
-
- Avoid having vulnerabilities in systems that ransomware could exploit.
-
-
- Keep relevant systems fully patched. Run scheduled checks to identify available patches and install these as soon as feasible.
- Employ zero trust principles in all networked systems. Manage access to all network functions and segment internal networks where practical to prevent malware from proliferating among potential target systems.
- Allow installation and execution of authorized apps only. Configure operating systems and/or third-party software to run only authorized applications. This can also be supported by adopting a policy for reviewing, then adding or removing authorized applications on an allow list.
- Inform your technology vendors of your expectations (e.g., in contract language) that they will apply measures that discourage ransomware attacks.
-
- Quickly detect and stop ransomware attacks and infections.
-
- Use malware detection software such as antivirus software at all times. Set it to automatically scan emails and flash drives.
- Continuously monitor directory services (and other primary user stores) for indicators of compromise or active attack.
- Block access to untrusted web resources. Use products or services that block access to server names, IP addresses, or ports and protocols that are known to be malicious or suspected to be indicators of malicious system activity. This includes using products and services that provide integrity protection for the domain component of addresses (e.g., hacker@poser.com).
The NIST Cybersecurity Framework Functions
The five Cybersecurity Framework Functions used to organize the Categories are:
- Identify – Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities. The activities in the Identify Function are foundational for the effective use of the Framework. Understanding the business context, the resources that support critical functions, and the related cybersecurity risks enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs.
- Protect – Develop and implement appropriate safeguards to ensure delivery of critical services. The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event.
- Detect – Develop and implement appropriate activities to identify the occurrence of a cybersecurity event. The Detect Function enables the timely discovery of cybersecurity events. 2 The Ransomware Profile
- Respond – Develop and implement appropriate activities actions regarding a detected cybersecurity incident. The Respond Function supports the ability to contain the impact of a potential cybersecurity incident.
- Recover – Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The Recover Function supports timely recovery to normal operations to reduce the impact from a cybersecurity incident.
Ransomware Response Checklist
The Cybersecurity and Infrastructure Security Agency (CISA) strongly recommends responding to ransomware using the following checklist in a Joint CISA and Multi-State Information Sharing and Analysis Center (MS-ISAC) Ransomware Guide. This information will take you through the response process from detection to containment and eradication. Be sure to move through the first three steps in sequence.
Detection and Analysis
- Determine which systems were impacted and immediately isolate them.
- Only if you cannot disconnect devices from the network, power them down to avoid further spread of the ransomware infection.
- Triage-impacted systems for restoration and recovery.
- Consult with your incident response team to develop and document an initial understanding of what has occurred based on initial analysis.
- Engage your internal and external teams and stakeholders with an understanding of what they can provide to help you mitigate, respond to, and recover from the incident.
Containment and Eradication
- Take a system image and memory capture of a sample of affected devices (e.g.,
workstations and servers). Additionally, collect any relevant logs.
NOTE: Take care to preserve evidence that is highly volatile in nature – or limited in retention – to prevent loss or tampering (e.g., system memory, Windows Security logs, data in firewall log buffers).
- Consult federal law enforcement regarding possible decryptors available, as security researchers have already broken the encryption algorithms for some ransomware variants.
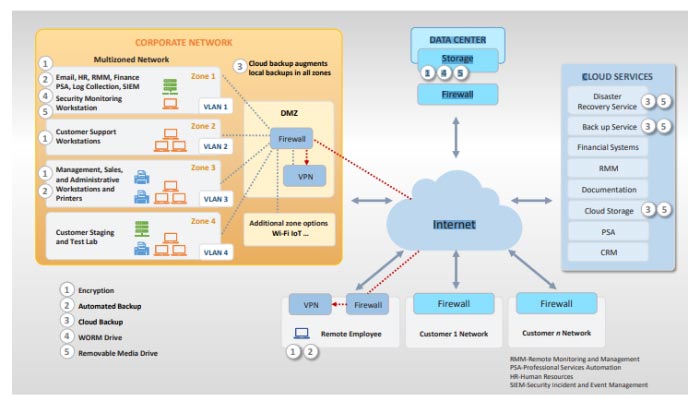
Figure 3 – NIST’s Corporate Network Architecture Diagram
Conclusion
One strategy to ensure you extract maximum value – and security protection – from this guidance is to work with a managed services provider to understand where implementing these best practices will be most impactful and cost-effective.
As always, we do not want to make this a commercial for SecureOps but we do want to help you set several expectations for your MSSP to help protect against Ransomware attacks.
- Start With Email – Email remains a primary ransomware delivery method. MSSPs can differentiate themselves in the market by providing a secure email gateway solution with multilayered protection.
- Monitor the Endpoints – By delivering malware to a user’s device, the attackers can use it as part of the next step in an attack. For example, malware may be used to exploit a web browser or software vulnerability that leads to gaining unauthorized web application access or spreading the ransomware across the network. With advanced endpoint detection and response (EDR), MSSPs can also provide risk mitigation at this point in the attack.
- Implement Zero Trust Network Access – By providing zero-trust policies both on and off the network, plus automatic encrypted tunnels to hide applications from the internet, MSSPs offer robust zero-trust architecture capabilities to meet customers’ on-premises, hybrid, and cloud security needs.
- Protect the Web Applications – As part of an MSSP’s Web Application Firewall, customers will want something that:
- Blocks known and unknown threats.
- Regularly updates signatures.
- Protects against OWASP Top-10 threats.
- Protects APIs while supporting mobile.
- Mitigates malicious bot activity.
- Segment the Networks – One of the issues with malware is its ability to move laterally throughout the network to find its target. To mitigate this risk, organizations need to segment their networks. Logical segmentation using firewalls separates sensitive data from general information, mitigating the data exfiltration that can occur during a ransomware attack.
To Learn More About How to Defend Against Malware Attacks or If You Have Been Attacked, Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/







