Stopping Coronavirus Cyber-Scams Before They Start – Part 2
How to Identify Coronavirus Cyber-Attacks – Part 2
In our first post concerning Corona Virus cyber-scams named “How to Identify Corona Virus Cyber-Attacks,” we wanted to warn our customers and readers of several prominent attacks by cybercriminals. As new, and in many cases, more destructive attacks were launched we wanted to write a Part 2 to our earlier blog post to make sure our readers and customers were aware of these new attacks. Coronavirus or COVID-19 scams and cyber-attacks have continued with fervor over the last couple of weeks as documented in the Wall Street Journal in the article Cybercriminals Sweep In to Take Advantage of Coronavirus (Warning: You need a subscription for WSJ – it is free if you connect through Starbucks WiFi but obviously that is difficult right now so our apologies). Thus, we’ll walk you through the newest cyber-scams so that you can defend yourself, your organization and your customers effectively.
Again, this post IS NOT intended to scare but to inform you. This means that you can take the steps necessary to avoid these threats.
Coronavirus Cyber-Attacks Aimed at New Remote Employees
We recently looked at the security challenges that are faced by having a growing remote workforce. Here we look at some new ‘phishing’ and ‘malware’ scams that have been targeting remote employees.
New phishing and malware fraudsters “posing as a vendor, member of the supply chain, or other familiar entities that would not seem out of place”
A reminder: ‘phishing’ occurs when a fraudster impersonates another through e-mail to lull the victim into a false sense of security. In some phishing attacks, the victims provide voluntary information or take some action for the fraudster. For example, this could involve entering personal information into a fake form such as in the ‘Office 365’ attack we previously discussed.
In related malware (or even ‘ransomware’) campaigns, the victim is encouraged to click on a link on an email, site or a message, which downloads malicious software onto the computer or device.
The US Secret Service has warned against recent COVID-19 phishing and malware campaigns stating:
“Corporations should be aware they are being targeted, with the attackers potentially posing as a vendor, member of the supply chain, or other familiar entities that would not seem out of place,”
Some prevalent phishing and malware campaigns related to COVID-19 include:
- Emails supposedly from the World Health Organisation (WHO) or the US Centre for Disease Control and Prevention (CDC) with COVID-19 information, encouraging the recipient to click on a malware attachment
- ‘Urgent’ orders or ‘late’ payment notifications for purchases from vendors or suppliers containing a malware attachment, posing as a ‘purchase order’ or ‘receipt’
A new malware campaign doing the rounds is the ‘Costco’ scam. Individuals are messaged about a box from Costco as part of the “stimulus package.”
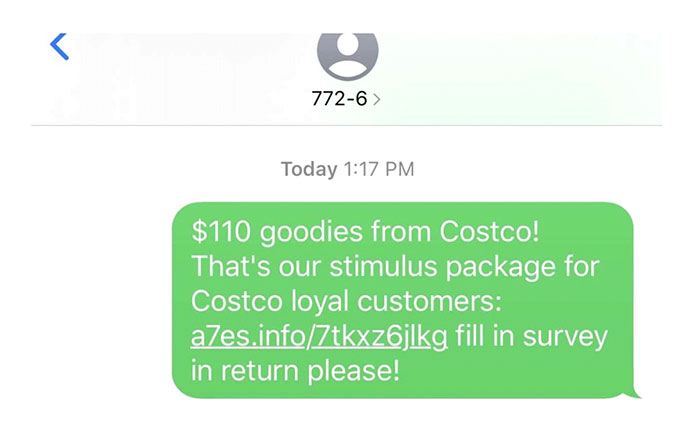
Once clicked on, the link uses malware, ransomware or other methods to steal information from that individual’s computer.
How to Protect Remote Workers from Phishing and Malware Campaigns
Protecting your remote workforce means doing two things: Training staff and setting up a secure remote work infrastructure.
Employee policies and training need to include:
- Identifying spelling and grammar mistakes. These are ‘tells’ for scammers
- Carefully scanning email addresses and URLs to ensure domains are correct
- Noticing fuzzy images (this can indicate copying and magnification)
- A procedure for confirmation phone calls before making any large payments (i.e. check that it really is the CEO before wiring her that $20,000)
- Advice to question any request for login credentials by email
- Advice on how to use password managers
- Advice on securing wi-fi connections and routers in the home
You should make certain that the remote work infrastructure provides for:
- VPNs allowing only limited access to business assets
- Secure remote desktop services
- Anti-virus and up-to-date software patches
- Multi-factor identity verification
Remote Employees and Prank Calls – ‘Zoom-bombing’
This one isn’t really a scam, but it is a new cyber-attack that all businesses need to protect remote employees from: ‘Zoom-bombing’. The FBI observes that “as large numbers of people turn to video-teleconferencing (VTC) platforms to stay connected in the wake of the COVID-19 crisis, reports of VTC hi-jacking (also called “Zoom-bombing”) are emerging nationwide.”
‘Zoom-bombing’ occurs when a conference call is hi-jacked by ‘trolls’ who share offensive images, post hate speech or otherwise behave offensively in the conference call.
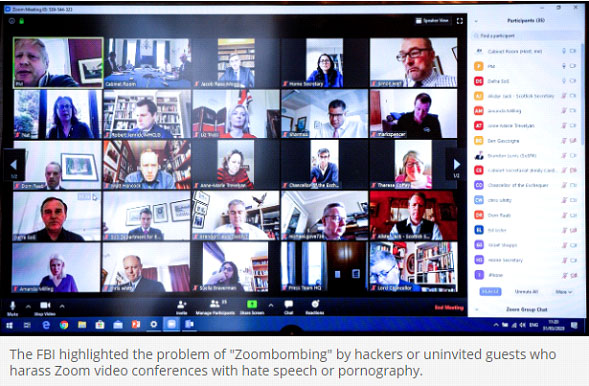
This can occur wherever a Zoom meeting is set to public, which means anyone can access it if they have the correct link. The culprits find these links by searching for Zoom URLs, or through Facebook, where links to public meetings are often posted. It appears also that dedicated threads listing these publicly accessible Zoom calls have been posted on Reddit.
“reports of VTC hi-jacking (also called “Zoom-bombing”) are emerging nationwide”
Here are some simple steps you can take to protect your remote employees from ‘zoom-bombing’:
- Here is a two-minute YouTube video by Zoom that will help you set up your meetings securely – https://www.youtube.com/watch?v=t6W3XZ2KAqo&feature=youtu.be
- Never share Zoom links in a public forum. Send them securely to participants or allow the public to request the business for a link
- Set meetings to private so that only those specifically invited can join
- Have the host automatically put participants in the ‘waiting room’ of the call. That way, the host can accept into the meeting only those who should be there
- Require the call ‘host’ to enable screen-sharing. That way, call participants cannot share offensive images with the rest of the call
While this cyber-harassment is happening on Zoom, you should guard against it occurring on any video-conferencing platform.
Fake Coronavirus Personal Protective Equipment (PPE) Advertisements
You may need to order medical and hygiene supplies such as hand sanitizer and masks for your business. Unfortunately, there have been dozens of fake websites and advertisements set up to secure your order, and then never deliver the goods.
A related cyber-scam is the sale of counterfeit personal protective equipment (also known as ‘PPE’). Scammers have been producing poor imitations of the popular 3M N95 mask without the CDC seal of approval. The CDC observed that these counterfeit masks “can compromise the safety of anyone who uses them, including healthcare providers.”
Some things you should look out for include:
- Does the seller have an established online history and reviews? Check whether the site address and payment details, exactly match the publicly reviewed company. This should help ensure that a real supplier’s site is not being ‘spoofed’ by a fraudster
- Are they only offering supplies related to the pandemic? Authentic suppliers should provide a substantial range of PPE
- Are the discounts being offered suspicious? It is unusual to see large discounts on PPE currently
Conclusion and Key Takeaways
As we previously pointed out, fraudsters are buying up domains for COVID-19 related sites, so all businesses need to be vigilant. Please use the advice we have offered here from our team, as well as the authorities, to ensure you keep your remote workforce safe:
- Educate remote employees on identifying spelling and grammar mistakes, checking URLs, images, using passwords and double-checking any request for credentials or payment. This is your best defense against phishing and malware cyberattacks
- Set up a secure work-from-home infrastructure (software updates, anti-viruses, VPNs and virtual desktops are essential)
- Ensure Zoom and other video calls are kept private to avoid ‘zoom-bombers’
- Make sure procurement due diligence is carried out to ensure that fake or counterfeit protective equipment is not purchased
We hope you find this information on Corona Virus related cyber-scams helpful and wish you the best at this difficult time.







