The SolarWinds Sunburst Attack: How to Protect Yourself from 5th Generation Cyberattacks
Last week US government offices were targeted by one of the most sophisticated and severe attacks seen in history both because of the sophistication and scope. A series of mega cyber-attacks were launched and thus far it appears were conducted by state-sponsored cybercrime organizations; the attacks targeted government and technology organizations worldwide.
This series of attacks were initiated by what is now thought to be Russian hackers who were able to embed a backdoor into SolarWinds software updates. Over 18,000 companies and government organizations updated their SolarWinds networking software, downloading what seemed to users to be a regular software update on their computers, unfortunately, it was actually a malicious Trojan Horse.
By taking advantage of the common IT practice of software updates, the attackers utilized the backdoor to compromise the organization’s assets, both cloud and on-premise. This enabled them to spy on the 18,000 organizations and access their data.
Since the attack last week, we have all been reading about the fallout from the SolarWinds supply chain attack now named Sunburst. Many of them are sales pitches riding on the popularity of buzzwords since those companies haven’t had close enough involvement to share things like the Indicators of Compromise (IOCs) or the attack techniques used. We’d like to take some time to bring up some points about incident response readiness with this to understand how organizations can better protect themselves.
How The Orion Tool Gave Attackers Access to Sensitive Data
A popular network management software company called SolarWinds was targeted and attackers were able to gain enough access to insert unauthorized code and malicious code into multiple distribution software builds of their Orion product over many months. The unauthorized code was then deployed to customer networks providing the attackers with a command and control mechanism into tens of thousands of new networks. Because this software is used in network administration, it is highly likely that customer networks gave the Orion tool very high administrative privileges, which were then extended to the attackers through the compromise.
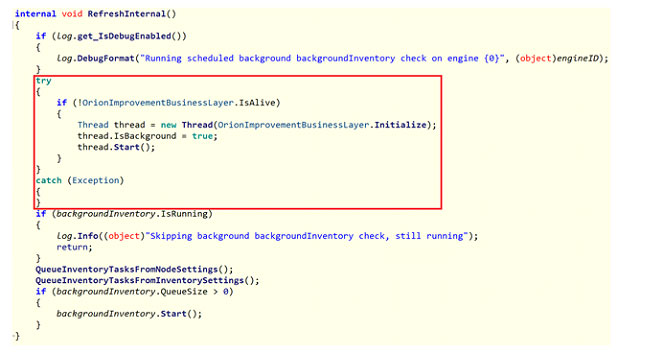
Specifically, the results of the investigation Microsoft conducted suggested, “the attackers inserted malicious code into SolarWinds.Orion.Core.BusinessLayer.dll, a code library belonging to the SolarWinds Orion Platform. The attackers had to find a suitable place in this DLL component to insert their code. Ideally, they would choose a place in a method that gets invoked periodically, ensuring both execution and persistence, so that the malicious code is guaranteed to be always up and running. Such a suitable location turns out to be a method named RefreshInternal.”
What is a Supply Chain Attack?
We call this a supply chain attack because the ultimate victims were not directly attacked. These types of attacks are extremely hard to protect against. We have to put a lot of trust in the cybersecurity programs of companies that we purchase products or services from. Most of those companies don’t want to share any details about how their internal cybersecurity programs function. Some of them will obtain a SOC2 report, but even those are shared cautiously due to the detail contained.
Incidentally, for clarification purposes, SOC 1 reports handle the financial transactions a company makes, SOC 2 reports on the security behind those financial transactions, making it more critical as attacks and data breaches have increased nearly exponentially over the past 5 years.
How is the Sunburst Attack Different from NotPetya
This isn’t the first time a supply chain attack has caused widespread panic. Remember the NotPetya attack on Ukraine in June 2017? The attackers gained access to the M.E.Doc software used by many businesses in Ukraine to calculate and submit taxes and provided high privilege access inside those customer networks. The attackers went a little further than Sunburst and placed phony ransomware on the networks that caused major outages with major global companies like FedEx, Maersk, Mondelez International, and even many hospitals.
Protecting Yourself from the Sunburst Trojan Horse
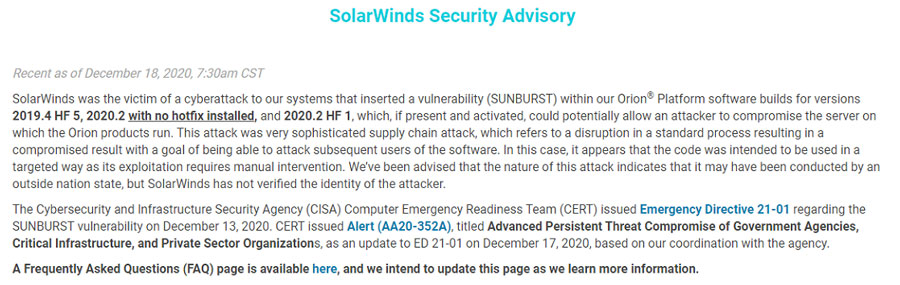
On Friday SolarWinds posted the following message on its website; “SolarWinds was the victim of a cyberattack to our systems that inserted a vulnerability (SUNBURST) within our Orion® Platform software builds for versions 2019.4 HF 5, 2020.2 with no hotfix installed, and 2020.2 HF 1, which, if present and activated, could potentially allow an attacker to compromise the server on which the Orion products run. This attack was a very sophisticated supply chain attack, which refers to a disruption in a standard process resulting in a compromised result with the goal of being able to attack subsequent users of the software. In this case, it appears that the code was intended to be used in a targeted way as its exploitation requires manual intervention. We’ve been advised that the nature of this attack indicates that it may have been conducted by an outside nation-state, but SolarWinds has not verified the identity of the attacker.”
Based on what we know now the most appropriate response is to first, determine if your organization uses the SolarWinds Orion software. If it does, isolate that software from external access. The software will still contain the unauthorized code, but the attackers cannot cause damage without a conduit for the attackers to connect and provide instructions.
Next, determine if your organization has any connection to any suppliers that use the Orion software. This connection could be through a VPN or some other temporary or permanent network level connection. It could also be through a privileged account able to access web applications such as Microsoft 365, Salesforce, Workday, and more. It could also be through a remote desktop connection such as Citrix, TeamViewer, and many others.
Limiting Privileges will Limit Lateral Movement
One of the factors that made the NotPetya so wide-spread was the victims giving the M.E.Doc software unrestricted administrator privileges. That software needed a couple of elevated privileges to operate, but it didn’t need full access. Giving it full access is what allowed the attackers to create a large amount of damage that was caused. This SolarWinds attack should be looked at with a similar lens. The software focuses on the management of the network and data collection. That doesn’t require full keys to the kingdom, but many organizations grant the keys because it makes it is typically easier. At this point, however, an organization should limit their exposure by limiting the privileges that your vendors and partners are given. This is the type of protection that is needed for supply chain attacks where you are giving away your trust.
Have an Incident Response Plan
Were you able to pull up a handful of documents to identify all these potential exposures? If not, fix that! The biggest contributor to delays during our incident response engagements are due to lack of documentation. Someone has to ask someone else, who thinks they know another person, but then finds out that person left a couple of years ago. We’ve seen it all, to be honest. Documentation aids a quick incident response, and a quick incident response results in better brand preservation and customer retention during a disclosed data breach.
Key Steps in Protect Your Organization in the Wake of Sunburst
Here are some things to do in the wake of this news. There are plenty of other blogs that share IOCs to search for, so these are things to consider when the dust has settled from the direct incident response activities if you were a victim of this attack. If you weren’t a victim, do these regardless, it will reduce your risk during a future exposure similar to Sunburst.
- Review Your Logging
The Solar Winds attack has so far been claimed to have started in June 2020. Sitting here right now, that is about 7 months ago. Do you have 7 months’ worth of logs in your infrastructure? Many of the current recommendations say to search your logs for x IOC to identify if you have been compromised by this attack. This recommendation is about making sure you can actually do this. If you don’t have logs, then you can’t search them. - Review Vendor Contracts
We sign big ugly legal contracts with vendors all the time, but we need to start considering the cybersecurity aspect of these partnerships. What happens if this vendor gets compromised by a cyber-attack? We recommend that your contracts draw out specific terms on how quickly a cybersecurity event needs to be disclosed and what information that vendor will supply if questioned by you. Contracts pave the road, so a vendor is not likely to disclose any sort of cybersecurity incident unless legally required. - Catalog Your Secrets
Sometimes these vendor relationships require high privileged access to your network, and that’s not a bad thing on its own. You need to document these high privilege accounts, so you have a quick reference of things to address when something like Sunburst happens again. Anything that requires what we call a service account – that’s a user account that no one logs into directly and has a static password for an application or service to use. - Reduce Authority
Take an assessment of the high privilege accounts across your infrastructure. Identify accounts that can be reduced in authority. Most users don’t need administrative privileges on their laptops. Most software does not need administrative access to your network to function.
Conclusion
When we connect vendors to our networks, we bring a lot of risk along with it. Some of that risk can be reduced through careful construction. As we were posting this blog, we found that Cisco Systems Inc. was compromised as part of Sunburst, which the government has confirmed was launched by a suspected Russian attack campaign. Network management and monitoring are key parts of Cisco’s equipment and software that monitor data traffic moving through a network. Access to that flow could provide a malicious actor with multiple avenues to cause harm.
The number of victims compromised by Sunburst has continued to rise over the past week since the attack was initially uncovered and details concerning how to stop and prevent these attacks and other similar attacks are still emerging. We will keep you updated concerning how you can keep yourself, your customers, and your organization safe.
To Learn More About How to Defend Against Malware Attacks or If You Have Been Attacked Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/