Resources
Our cybersecurity insights and facts, comprehensive reports, and whitepapers are geared
to provide unique information on trends and events in the IT security industry.
Industry Reports

Anatomy of a Hack
The Sony Breach Investigation Provides Unprecedented Detail
Incident response planning is crucial; however, organizations have learned that many are still not prepared to handle a cyber-attack.

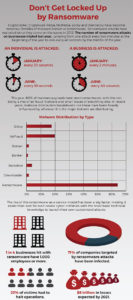
The Growing Threat of Ransomware Report
Why Organizations Need to Prepare for a Ransomware Attack
Ransomware has become the most serious threat to IT security teams over the past two years. Our 33-page report illustrates how the Ransomware threat has exploded and what may be coming next.

75+ Cybersecurity Statistics and Facts
Critical Cybersecurity Statistics You Must Know
We have compiled dozens of critical cybersecurity statistics from leading research organizations like Verizon, Ponemon, and Cybersecurity Ventures that paint a comprehensive, yet alarming picture of the state of IT security. Cybercrime costs, ransomware trends, and victim data are all part of the list of statistics that illustrate why cybersecurity attacks will dominate the news headlines.

Everything You Need to Know About Pen Testing
The Only Penetration Testing Resource You’ll Ever Need
Pen Testing has evolved and now includes different flavors including Black Box, White Box, Red Teaming, Ethical Hacking, and more. This report not only describes all the different penetration tests we could find, but also discusses the goals, benefits, and other details about the test. Network, Web App, Wireless, Client-side, and other Pen Tests are discussed in detail including the target of the test and the benefits.

The Critical Elements of Improving SOC Effectiveness
Understanding the Roles of People and Technology in a SOC
In this report, we discuss the structure of a SOC, its missions and goals, the technology SOC’s leverage to defend against attacks, and how to manage the SIEMs and IDS/IPS technology more effectively. Further, the report digs into the people, processes, and technology that analysts depend on to improve their efficiency and performance. Finally, we provide 4 simple, straightforward recommendations that nearly every SOC has identified as issues they would like to address in 2021.
SecureOps Videos
Millennium Live on The Fundamental Elements of Cyber Hygiene with Bill Boni
We feature Bill Boni, retired former Senior Vice President, Information Security at T-Mobile USA and Corporate Security Officer at Motorola in this interview with Millennium Live. Bill discusses how organizations can find the right partner MSSPs who provide top value in delivering effective risk management within dynamic security environments.
How The California Consumer Privacy Act will Impact Business
Ahmad Alomari is a Principal Cyber Security Engineer at SecureOps. Ahmad has spent the last several years of his 9-year career with SecureOps helping organizations meet their ever-increasing compliance requirements. Ahmad discusses The CCPA legislation, which organizations will be affected, the penalties they will face for non-compliance, and where they should focus their efforts to become compliant prior to January 1, 2020, and beyond.
Leveraging a Zero Trust Security Model and Micro-Segmentation to Improve Defense
Javier Hernandez is a Network Security Architect at SecureOps. Javier designs IT Security infrastructures for Fortune 500 organizations and has expertise in cloud computing and networking. Javier discusses the Zero Trust network architecture and Micro-segmentation and how the two improve security visibility and limit an attacker's ability to move within a network to steal PII, IP, and other valued organizational assets.
Roles, Responsibilities and Challenges of the Modern SOC
Eric Duval is a Senior Security Manager or Senior SOC Manager at SecureOps and has handled a variety of roles in the SOC in his 8-year tenure. His veteran perspective on the roles, responsibilities and challenges of various security operation center positions provides useful knowledge for folks entering the industry as well as experienced security staff. From managing security technology to dealing with Ransomware and DDoS attacks, Eric covers wide-ranging topics with clear insight and answers.
Why Log Monitoring is Critical to Maintaining Security & Compliance
Erik Montcalm the Vice-President, Services & Technologies at SecureOps discusses the critical aspects of log monitoring including dealing with encrypted traffic that may be hiding malware, analyzing logs to uncover malicious activity, maintaining compliance, and managing SIEM’s for clients.
Understanding Bug Bounty and Pen Testing Programs
Jasmin Landry a Senior Cyber Security Engineer at SecureOps certified in CEH, GWAPT, and has a OSCP from Offensive Security discusses the value of Pen Testing and Bug Bounty programs. Jasmin is ranked in the top 50 in Bugcrowd’s global ranking and thus has a unique perspective on improving security by uncovering vulnerabilities with Pen Testing and Bug Bounty programs.
Get In Touch With Us
Who Are We?
Headquartered in downtown Montreal, Canada SecureOps was founded in 1999 specifically to protect organizations and their critical assets from Cyber Threats. Our certified experts build and deliver tailored security services to monitor and protect our client’s most critical IT assets 24/7.
CANADA
Address: 600 de Maisonneuve Boulevard West Suite 2400 Montreal, Quebec H3A 3J2
Tel: 1.888.982.0678
Fax: 1.514.982.0362
CZECH REPUBLIC
Address: Meteor Office Park,
Sokolovská 100/94, 186 00 Praha 8,
Czech Republic
Tel: 1.888.982.0678
Fax: 1.514.982.0362
PHILIPPINES
Address: 837 A. Arnaiz Avenue 4F-B,
Makati City, Philippines 1226
Tel: 1.888.982.0678
Fax: 1.514.982.0362