INTERPOL – Cybercrime Increasing at “Alarming Pace”
The State of Cybersecurity in 2020
This blog post is geared to provide a clear picture of the State of Cybersecurity in 2020 according to leading research groups and cybersecurity authorities. The post may be a bit disjointed as we’ve pulled data and insights from a variety of sources and tried to paint a clear picture of what is actually going on from an IT security perspective.
In addition, our goal in these posts is never to create fear or provide our MSSP perspective but to simply report the facts in a straightforward, educational manner and hopefully provide helpful advice from the SecureOps team.
Cybercrime is Growing at an “Alarming Pace”
We are really not trying to fear monger – this is the statement that was delivered by Jürgen Stock, INTERPOL Secretary General as a result of their recently released assessment and report on the State of Cybersecurity attacks globally over the past 4 months.
Cybercrime is growing at an “alarming pace” as a result of the ongoing COVID-19 crisis and is expected to accelerate even further, a new report from INTERPOL has found.
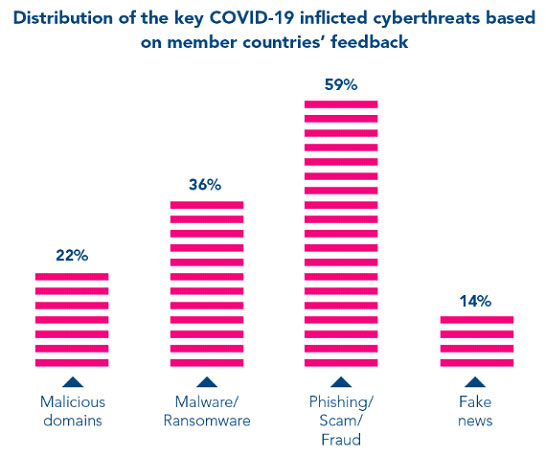
Based on feedback from member countries, INTERPOL said that during the COVID-19 period, there has been a particularly large increase in malicious domains (22%), malware/ransomware (36%), phishing scams/fraud (59%) and fake news (14%).
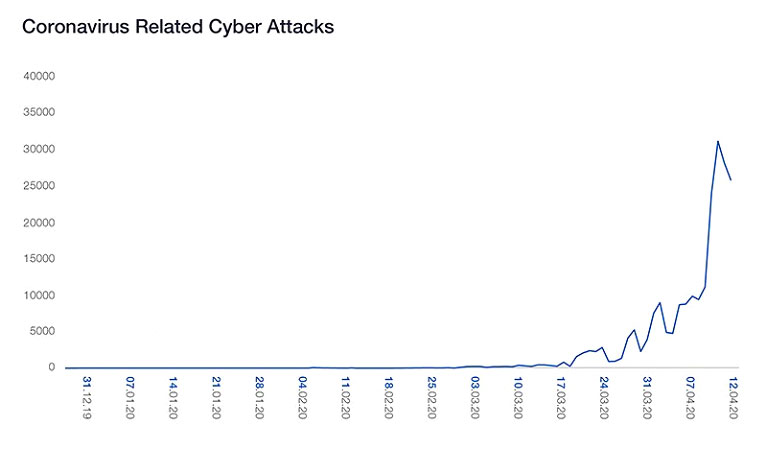
The INTERPOL assessment provides an interesting insight into the increase in COVID-19 Phishing scams, Ransomware attacks which we discussed in detail in a previous blog post, RAT’s or Remote Access Trojans and misinformation or SPAM that offers free benefits, cures to the Coronavirus or other goodies that are of course fictitious. However, what I found most interesting was the increase in the number of domains containing keywords such as “coronavirus” or “COVID” by cybercriminals. These fraudulent websites support all kinds of criminal activities including C2 (Command & Control) servers, malware distribution, and phishing schemes. From February to March 2020, a 569 percent growth in malicious registrations, including malware and phishing and a 788 percent growth in high-risk registrations were detected and reported to INTERPOL by a private sector partner. That number is staggering!!
A 569 percent growth in malicious “COVID-19-related” registrations, including malware and phishing and a 788 percent growth in high-risk registrations were detected and reported to INTERPOL by a private sector partner
As we wrote about in two previous blog posts about the Coronavirus scams, many cybercriminals have revised their usual online trickery and phishing schemes so that they are COVID-themed, playing on their victims’ fear, generosity and poor understanding of cyber risk.
Stopping Corona Virus Cyber-Scams Before They Start – https://secureops.com/security/corona-virus-scams/
Stopping Coronavirus Cyber-Scams Before They Start – Part 2 – https://secureops.com/blog/corona-virus-scams-part-2/
The report also found that cyber-criminals have significantly shifted their targets away from individuals and small businesses to major corporations and governments, although many small businesses and healthcare organizations have been devastated by ransomware this year.
Many large organizations have been quickly shifting to a remote work model and the shortage of technical security staff, the rapid migration to cloud computing, regulatory compliance requirements like GDPR and CCPA are creating significant security gaps. In addition, as we have seen with the evolution of ransomware and other malicious code, the number and diversity of threats continue to be the most significant ongoing major security challenges.
We did receive positive news from the Ponemon Institute and Deep Instinct study however; the study suggests Cyber attack prevention initiatives can have a significant payoff for organizations. Their study indicates that you could save up to 82% of the costs associated with the cybersecurity lifecycle (prevention, detection, containment, recovery, and remediation). So, if you are able to prevent a cyber-attack that would have cost your business $1 million, for example, that would be a savings of $820,000 ($1,000,000-180,000 in prevention costs = $820,000 in savings).
Breaches Have Increased 273% Year over Year
INTERPOL didn’t provide great data concerning why they felt attacks were increasing at an “alarming pace” so we wanted to dig in a bit further to uncover the real data. According to a new study from cloud computing company Iomart, large-scale breaches are growing in intensity and frequency in 2020, with the number of breaches increasing 273% in the first quarter, compared to the same time last year.
Early in the pandemic, there was an uptick in targeted campaigns about understanding Covid-19 and COVID statistics which we discussed in a previous blog post. Now criminals are shifting to focus on stimulus payments, unemployment, PPP loans, and benefits. On the day PPP loans first hit bank accounts, the websites of several large banks went down because of the surge in traffic.
Gartner added further insight, “The pandemic, and its resulting changes to the business world, accelerated digitalization of business processes, endpoint mobility and the expansion of cloud computing in most organizations, revealing legacy thinking and technologies,” says Peter Firstbrook, VP Analyst, Gartner.
The Gartner analyst further suggested that “COVID-19 refocused security teams on the value of cloud-delivered security and operational tools that don’t require a LAN connection to function, reviewing remote access policies and tools, migration to cloud data centers and SaaS applications, and securing new digitization efforts to minimize person-to-person interactions.”
Jürgen Stock, the INTERPOL secretary general provided detail to his earlier statement saying, “Cyber-criminals are developing and boosting their attacks at an alarming pace, exploiting the fear and uncertainty caused by the unstable social and economic situation created by COVID-19.
“The increased online dependency for people around the world is also creating new opportunities, with many businesses and individuals not ensuring their cyber-defenses are up-to-date.”
The INTERPOL study further added that “a further increase in cybercrime is highly likely in the future.” This is primarily due to vulnerabilities related to remote working, a continued focus on COVID-themed online scams, and, if and when a vaccination becomes available, another spike in phishing related to medical products.
The INTERPOL assessment revealed the extent to which cyber-criminals are taking advantage of the increasing reliance on digital technology over recent months. The almost instant shift to remote work underway in many organizations has involved the deployment of remote systems and networks, often insecurely.
Beware of Remote Access Solutions Including VPN’s and RDP
Many organizations may be at increased risk of ransomware attacks due to having opened up remote access solutions, such as VPNs or leveraging RDP or Remote Desktop Protocol to support remote working.
These remote access points may not be properly configured and secured or, due to IT teams operating remotely, may not have the latest patches installed. In addition, staff may have had to use their own personal devices from home to work remotely which in turn poses challenges from a security point of view with regards to how to ensure those devices are secure.
The shift to remote working as a result of the pandemic has led to a significant increase in targeting of the Remote Desktop Protocol (RDP) in recent months. Roman Kováč, chief research officer at ESET, commented: “Our telemetry showed a continued influx of COVID-19 lures in web and email attacks, as well as an increase in attacks targeting RDP, with persistent attempts to establish RDP connections more than doubling since the beginning of the year.”
Remote Desktop Protocol (RDP) is arguably the most common remote access tool used today. RDP defines how server and client components communicate in order to provide a graphical interface from one computer to another “remote” computer. Microsoft includes RDP functionality with most versions of its Windows operating system making it available to most employees and relatively easy to use.
RDP has had a variety of vulnerabilities. Several significant flaws have surfaced in recent years which resulted in virtual waves of attacks against systems. Some of these vulnerabilities even allow for the remote execution of code, software, or programs, on those systems and resulted in allowing threat actors to gain full access and control. Since 2001, a total of 40 vulnerabilities have been identified with RDP, including 4 new ones released in the first quarter of 2020.
Jonathan Miles, head of strategic intelligence and security research at Mimecast, added: “It is important that organizations migrate away from a ‘keeping the lights on’ mentality and prioritize cybersecurity, especially at a time when threats aimed at a dispersed workforce are increasing. Failing to do so can lead to issues such as organizational downtime, data loss, and a negative impact on employee productivity.”
“These remote access points may not be properly configured and secured or, due to IT teams operating remotely, may not have the latest patches installed. In addition, staff may have had to use their own personal devices from home to work remotely which in turn poses challenges from a security point of view with regards to how to ensure those devices are secure.”
More than 50% of all security incidents involving ransomware also involved RDP
According to a recent report from Coveware (ransomware negotiation specialists), RDP has been the preferred attack surface for ransomware-wielding hackers consistently since 2018. More than 50% of all security incidents involving ransomware also involved RDP, with some time periods measured at more than 80%.
We discussed 5 critical items to handle to keep your remote workforce protected in this blog post – https://secureops.com/security/remote-employee-attacks/
Most Attacks Still Start with a Phishing Lure
Google says it is stopping up to 18 million malware and phishing emails related to COVID-19 from reaching Gmail users every day. Further, 62% of businesses experienced phishing and social engineering attacks last year, the number has undoubtedly increased this year. And in last year’s Verizon DBIR report, 94% of malware was delivered by email.
One excellent resource we found to help organizations bolster their social engineering defense is from Irish cybersecurity awareness training company Cyber Risk Aware, who announced recently that it would be providing free COVID-19 phishing tests for businesses. Companies are invited to run a phishing simulation in which up to 100 staff can learn how to avoid falling for COVID-19 lures.
https://www.cyberriskaware.com/free-phishing-test/
Along with the free simulation, companies can download a checklist of Do’s and Don’ts designed to keep employees who are working remotely cyber-safe.
8 Cybersecurity Statistics Reports
Below are some helpful cybersecurity studies and articles to deepen your knowledge about the cybersecurity landscape.
- Accentures’s 2019 Cost of Crime Study
- Cisco’s Cybersecurity Reports
- Cybersecurity Venture’s Job Study
- Symantec 2019 Internet Security Threat Report
- RiskBased Mid-Year Data Breach Report
- Varnois’ 2019 Data Risk Report
- Verizon’s 2019 Data Breach Investigations Report
- World Economic Forum’s 2019 Global Risk Report
Conclusion
We told you this post would be a little disjointed but we did want to get you the data from INTERPOL as quickly as possible and dig into RDP, Phishing, and other attack tactics so that you were aware of the most prevalent cyber-attack trends.
Interestingly, although attacks are increasing and costing organizations more, the forecast for Cybersecurity defense spending is increasing at a slower rate than in previous years due to the financial impact of Covid-19. The Global Cyber Security Market Analysis by ResearchAndMarkets.com is saying the market will likely grow 6.2% per year to 2023.
Organizations need to be cost-effective with their cyber-defense measures and make certain they follow the 80/20 rule and leverage good risk management principles. Vulnerability assessments, patching, identifying critical data and systems, pen testing, and security posture assessments are key in providing a defense foundation.
To Learn More About How to Defend Against Cyber-Attacks or If You Have Been Attacked Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/