The Difference Between a Penetration Test and Vulnerability Assessment (2 of 2)
What is the Difference Between a Penetration Test and Vulnerability Assessment?
Part 2 of 2
Comparing Penetration Tests and Vulnerability Assessments
In part 1 of this post, we focused on the Vulnerability Scans, Vulnerability Assessments, and Vulnerability Management in order to differentiate the 3 prior to digging into Penetration Tests. Now, let’s introduce and define Penetration Tests, explain the test itself and goals, then go through the different types of Penetration Tests.
What is a Penetration Test?
A Penetration test, or pen test, is the process an ethical hacker conducts on a target and the IT environment to uncover vulnerabilities by exploiting them. The goal is to gain unauthorized access through exploitation which can be used to emulate the intent of a malicious hacker. Penetration test reports may also assess potential impacts on the organization and suggest countermeasures to reduce risk.
In layman terms, a pen tester or ethical hacker is trying to do what a hacker would try to do to breach a system, machine, server or break security controls in order to steal sensitive information or somehow damage the organization.
The National Cyber Security Center describes penetration testing as the following: “A method for gaining assurance in the security of an IT system by attempting to breach some or all of that system’s security, using the same tools and techniques as an adversary might.”
Phases of a Penetration Test
A Penetration Test is often broken down into the following phases:
- Reconnaissance
- Threat Modeling and Vulnerability Identification
- Exploitation (gaining access)
- Post-exploitation (maintaining access)
- Covering tracks
- Reporting
- Resolution & Re-Testing
A pen test is often initiated by a variety of changes in an IT environment including application launches, major network/application changes or updates, compliance regulations or a breach/leak from a targeted attack. Again, the end goal of an ethical hacker is to gain unauthorized access to a system by means of exploiting vulnerabilities or gaps in security processes.
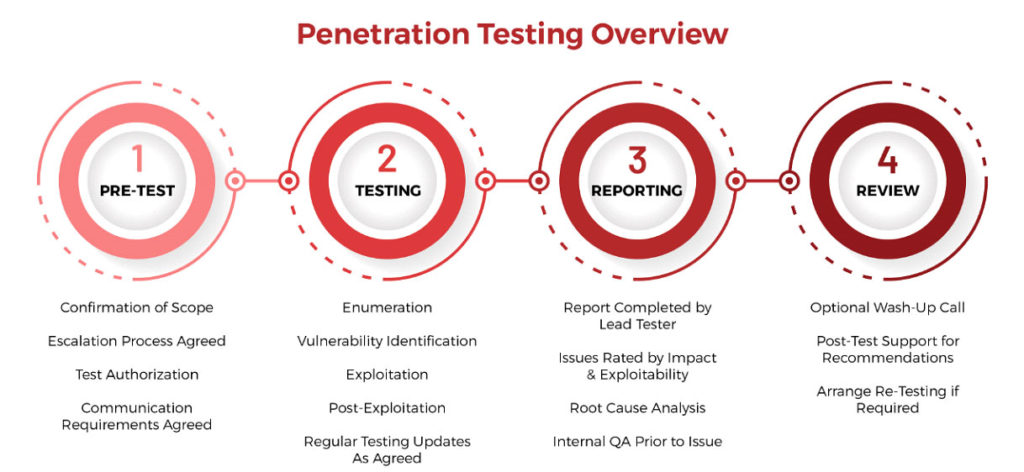
Penetration Test Reporting
The ultimate value of a pen test is the comprehensive report that is delivered by the ethical hacker. Pen test reports often follow a similar structure if they are of high quality and delivered by a reputable ethical hacker or organization.
- Executive summary: This is a high-level summary of the report contents that uses non-technical language so that everyone from the CEO to the IT Security staff can understand. The process of the test, findings, and recommendations will be addressed to provide a clear understanding of the organization’s overall security status.
- Summary findings and recommendations: This can be broken down into two sections – an overview of the findings and a review of the recommendations. The findings may include some of the higher risk vulnerabilities as well as a discussion of positive security controls practiced. The recommendations typically include the higher risk fixes including software vulnerabilities, poorly secured PII, or risky 3rd party access to name a few. Frankly, this section should list anything that that needs to be addressed to enhance overall security.
- Detailed findings in order: This is the bulk of the report. Each finding will be written with a summary, technical details, reproduction steps, and detailed recommendations in order of significance.
- Methodology: High-level pen testers will include a methodology section in the report to outline the process taken in their approach. The methodology can help your organization have a better understanding of how technical and deep the testing methodology was.
- References: This section can include a list of used tools and applications for the assessment and any other relevant material.
- Appendices: The last section is reserved for any material which required additional information relevant to the report but isn’t essential to the main body of the report.
When to Conduct a Penetration Test
- Vulnerability Management Program: A good, mature vulnerability management program should include periodic penetration testing. Think about it this way, a vulnerability scan uncovers an unwieldy list of software vulnerabilities, a vulnerability assessment places the vulnerabilities in a prioritized list, a vulnerability management program handles fixing those vulnerabilities by priority and a penetration test will ultimately test those fixes.
- Application Launches: A pen test is often conducted as part of the software development life cycle (SDLC) process to uncover existing vulnerabilities in the application. Software developers are notoriously poor at thinking about security in the development process so testing the applications is critical prior to launch.
- Compliance regulations: A pen test is either required or recommended with certain compliance regulations including some of the most significant legislation including PCI-DSS, HIPAA, Sarbanes-Oxley, and others. Essentially penetration tests are a component of a full security audit. For example, the Payment Card Industry Data Security Standard (PCI-DSS) requires penetration testing annually or “upon significant changes.” The link above contains a PDF document.
- Network or Application Changes: Pen tests are often scheduled in conjunction with any major changes in the network or application updates. Changes in the IT infrastructure often create security gaps. Think about simply adding a new system to an environment; that system requires security solutions like firewalls, content filtering, log monitoring, and depending on the data it contains, perhaps much more.
- After a breach: This is the worst reason to conduct a pen test, but it has become fairly common. After having been breached and having confidential data exposed to the public, a company may immediately conduct a pen test to try and stop the bleeding so to speak. The objective here is to uncover any additionally existing vulnerabilities and holes an organization may have.
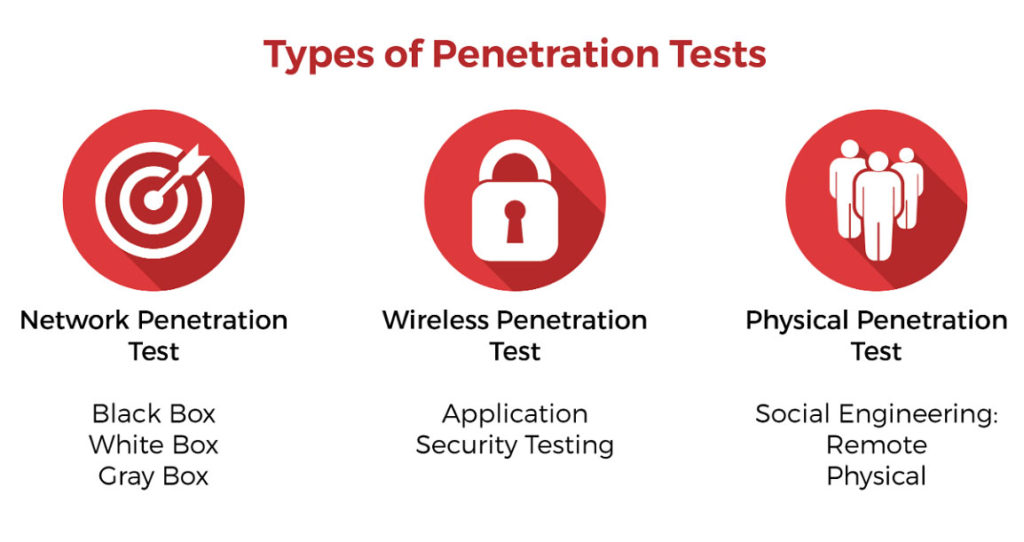
What are the Different Types of Penetration Testing?
Pen testing is often based on the level of knowledge and access given to the pen tester for very specific reasons. The range runs from black-box testing, where the tester is given minimal knowledge of the target system(s), to white-box testing, where the tester is granted a high level of knowledge and access. There are benefits to each type of testing which we will address.
Black-Box Testing
In a black-box scenario, the penetration tester is placed in the role of a true hacker, with no internal knowledge of the target system. Testers are not provided with any architecture diagrams or source code that is not publicly available. A black-box penetration test determines the vulnerabilities in a system that are exploitable from outside the network.
Black-box penetration testing relies on the skill of the ethical hacker and their analysis of currently running programs and systems within the target network. Black-box penetration testers are typically highly skilled must be familiar with automated scanning tools such as nmap and Metasploit and methodologies for manual penetration testing.
Gray-Box Testing
If a black-box tester is examining a system from an outsider’s perspective, a gray-box tester has the access and knowledge level of a high-level employee, often with elevated privileges on priority systems. Gray-box pen testers typically have some knowledge of a network’s internals, potentially including design and architecture documentation and an account internal to the network.
The purpose of Gray-box pen testing is to provide a more focused and efficient assessment of a network’s security than a black-box assessment. Leveraging the design document for the network a Gray-box pen tester can focus their attention on the systems with the greatest risk and value from the start, rather than spending time determining this information on their own. In addition, with legitimate access to systems testing of security inside the hardened perimeter simulates an attacker with longer-term access to the network.
White-Box Testing
White-box testing falls on the opposite end of the range from black-box testing; penetration testers are given full access to source code, architecture documentation and other information about the environment and systems. The main challenge with white-box testing is sifting through the massive amount of data available to identify potential points of weakness, making it the most time-consuming type of penetration testing.
Unlike black-box and gray-box testing, white-box penetration testers are able to perform static code analysis, making familiarity with source code analyzers, debuggers, and similar tools important for this type of testing.
White-box penetration testing provides a comprehensive assessment of both internal and external vulnerabilities, making it the best choice for calculation testing. One of the key benefits of this type of testing is to find coding errors in the early stages of software development.
Ethical Hacking, Red Teaming and Capture the Flag
We wrote a comprehensive blog post on Ethical Hacking, Red Teaming and Capture the Flag about a year ago which I encourage you to read for more information on the 3 exercises.
Read Our Blog Post – Penetration Testing – Ethical Hacking, Red Teaming and Capture the Flag here: https://secureops.com/penetration-testing/penetration-testing-tactics-and-goals/
In this post, we’ll try and provide more concise information so we don’t simply repeat what was provided in the previous post or go too far in length with details about each.
Ethical Hacking
Ethical hacking is quite similar to penetration testing and often used interchangeably, however, there are several key differences. The term ethical hacking is a broader term for hacking techniques specifically used by ethical hackers. While a penetration tester might discover flaws and vulnerabilities and deliver a report, an ethical hacker will likely conduct a longer-term assessment, using a greater variety of attack types and more fully testing and exploring the environment.
While a penetration tester is usually focused on identifying vulnerabilities, an ethical hacker will usually pursue a full scope of hacking techniques in an attempt to find as many security flaws as possible. In most cases, it is less of a point-in-time assessment and more of a holistic security evaluation of a target environment. Ethical hackers also may provide more remediation assistance, commonly working with the organization to ensure the security of the target system.
Red Team Exercises
A red team assessment is another type of security testing tactic or exercise that is more defined and focused than penetration testing. The goal of a red team assessment is to test the target organization’s detection and response capabilities. The main difference is the comprehensive methods taken by the red team to simulate an actual attack.
Organizations are typically not informed of the test, and the red team proceeds to attempt to access critical and sensitive data leveraging a variety of attack methods; essentially simulating the tactics of an actual attacker. The assessments are usually a longer process and a more thorough investigation into security vulnerabilities and their corresponding impact. Methods may also be more extensive than a typical pen testing and include social engineering, wireless testing, and physical security testing.
Capture the Flag Penetration Test Exercises
Another penetration test-related exercise is a capture the flag (CTF) exercise. Testers are assigned a specific goal (capturing the flag), which might be exfiltrating a specific data file or accessing a specific system. CTF exercises are often set-up in a competition environment with teams competing to accomplish the goal first.
Contests with prizes and open competition are often used to recruit new employees, build security skills, and test systems. CTF exercises are different from a traditional penetration test in that they often use test environments or third-party environments, like the Michigan Cyber Range, as the event is more of an evaluation of the testers’ skills than production systems.
Bug Bounty Programs
Bug Bounty Programs have taken off recently because of the number of breaches, number of software vulnerabilities and the interest of large organizations to stay out of the news with a data breach. A bug bounty program is a deal or money offered by many websites, organizations and software developers by which individuals can receive recognition and compensation, in many cases thousands of dollars for reporting software bugs, especially those pertaining to exploits and vulnerabilities.
These programs allow the developers to discover and resolve bugs before the general public is aware of them, preventing incidents of hacking. Bug bounty programs have been implemented by a large number of organizations, including Mozilla, Facebook, Yahoo!, Google, Reddit, Square, and Microsoft.
Watch Our 15 Minute Video on Penetration Testing with Jasmin Landry, a top 50 globally ranked player in BugCrowd’s Bug Bounty rankings here: https://secureops.com/resources/
- Watch a Webinar on BugCrowd featuring Jasmin Landry here: https://tinyurl.com/y6pzvtnh
- See Jasmin Landry’s Profile on HackerOne here: https://hackerone.com/jr0ch17
- Get Started Hacking with HackerOne here: https://www.hackerone.com/start-hacking
Conclusion
We discussed Vulnerability Scanning, Vulnerability Assessments, Vulnerability Management and Penetration Testing. Hopefully, we were able to convey that scanning, assessments, and pen testing are all part of a quality vulnerability management program.
(1) Start with a scan to identify software vulnerabilities
(2) conduct an assessment to prioritize systems and patches, and once the assessment is complete with all tasks identified in the assessment handled
(3) conduct a pen test to test the security of the systems and security controls in the environment. Essentially, those are the nuts and bolts of a vulnerability management program.
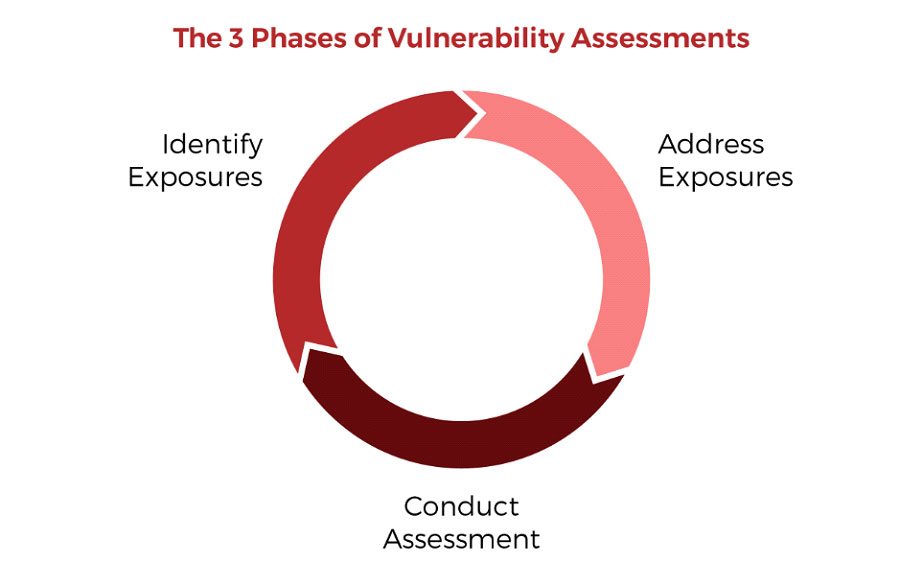
To get started on the road to security program improvement start with a vulnerability assessment. This will provide a good launch point for your IT security team to understand where the organization lies on the security maturity continuum. You’ll have a list of vulnerabilities, systems, proprietary data or sensitive information and other details that will allow you to prioritize patching and other security tasks.
I hope this blog post provided the information you needed and please know that the team here at SecureOps is here to help. If you’ve run a Vulnerability Scan or Assessment and need assistance interpreting the results or taking the next step, please call us or e-mail us; we are happy to provide assistance.
Final Notes from SecureOps Management
SecureOps offer retesting to confirm that any vulnerability found has been fixed. We also provide a certificate that shows the Penetration Test has been completed. And of course, we use only skilled security professions who have deep industry specific certifications and have proven success.
Penetration Tests are excellent for companies to understand where their vulnerabilities resides as well as their strengths and weaknesses. It can also be a excellent training for developers to learn how to do secure coding and change their SDLC to an S-SDLC.







