Ransomware is Targeting Industrial Control Systems
Industrial Control System (ICS) Ransomware is Evolving…Quickly
Several months ago we wrote a blog post called The Evolution of Malware which tracked the development of how cyber-attacks and malicious code have evolved from simple viruses and worms to highly-sophisticated and targeted code like Stuxnet. We touched on Ransomware in the blog post, however with the uncovering of EKANS or “Snake” ransomware which targets Industrial Control Systems (ICS), the evolution of ransomware has progressed significantly.
EKANS Malware Targets Industrial Control Systems Specifically
EKANS or “Snake” spelled backward was used in a ransomware attack recently and has subsequently earned the attention of the researchers at Dragos, an ICS-focused security organization. Dragos researchers noted that while previous ransomware attacks against ICS targets would disrupt the systems, EKANS had the ability to force computers to stop specific activities, or processes.
The ransomware targets processes started as part of GE’s Proficy data historian, which records events and the status of devices on the network. It also has the ability to target GE Fanuc licensing server services, and Honeywell’s HMIWeb application according to the Dragos report. The targeting of ICS processes puts EKANS in the same category as its parent and much larger threat, MegaCortex ransomware, which has successfully infected companies’ systems and demanded ransoms from the victim organizations ranging from $20,000 to $5.8 million.
“The specificity of processes listed in a static ‘kill list’ shows a level of intentionality previously absent from ransomware targeting the industrial space,” the Dragos report stated. Meaning, EKANS, and MegaCortex target stopping or “killing” certain applications that are used exclusively in an ICS environment.
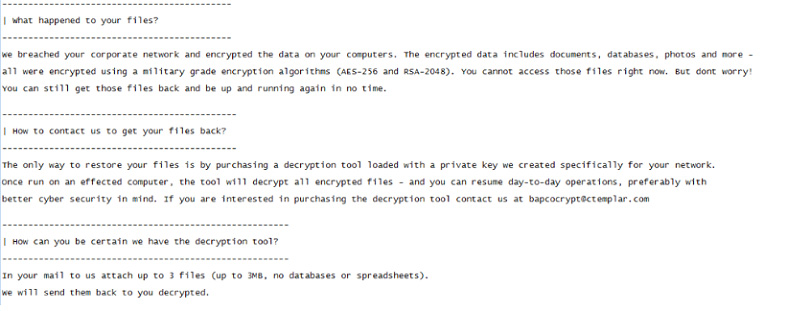
Once the processes are stopped and the encryption actions are taken, EKANS delivers the above ransom note to the root of the system drive (typically C:) and the active user’s desktop.
EKANS and MegaCortex Stop Processes and Encrypt Data to Generate Ransom Payments
EKANS and MegaCortex are different types of malware than most industrial infosec professionals have dealt with in the past because the code targets ICS-specific applications. In addition, the malware continues to evolve adding encryption features, new applications to “kill”, and new obfuscation techniques that are making it more difficult to identify and uncover an attack. Prior to EKANS and MegaCortex malware, targeting ICS systems wasn’t specifically designed to disrupt operations for financial gain – it is clear that this malware is.
Stuxnet killed nuclear enrichment centrifuges in Iran and Crash Override turned out the lights in Ukraine but EKANS and MegaCortex are not designed to simply disrupt or destroy but rather to take systems offline and create visibility issues for oil refineries, manufacturing facilities and the like. By stopping processes and encrypting the data on the systems, cybercriminals can request a ransom to stop the attack.
MegaCortex, EKANS, and Ransomware, in General, Are Evolving Quickly
The original version of MegaCortex had its main payload protected by a password that was available only during the live infection. Thus, the feature of the malware made the malware difficult for security vendors to investigate and analyze. However, the password requirement of the malware also prevented the malware from being widely distributed worldwide and required the attackers to install the ransomware mostly through a sequence of manual steps on each targeted network.
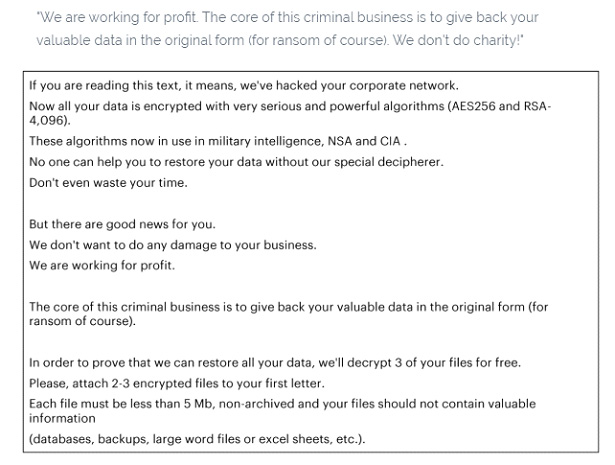
The MegaCortex v2 authors have designed the second version of the malware to self-execute and removed the password requirement for installation. Further, MegaCortex v2 incorporates some anti-analysis features within the main malware module, and the functionality to stop and kill a wide range of security products and services.
What this means from a distribution standpoint is that MegaCortex v2 can be delivered via e-mail because all of the manual requirements of the malware have been automated. This is what concerns researchers about MegaCortex v2 and now EKANS. In addition, as you can see from the ransom note – cybercriminals clearly mean to target corporations in order to increase their profits.
Conclusion
In terms of protecting yourself and your organization from a ransomware attack, the advice hasn’t changed significantly in light of these two new types of malware. That said, the first thing industrial organizations must do is adjust their threat profiles to include attacks that include MegaCortex and EKANS. There is no question that many industrial organizations have not included malware like this in their threat profile.
Second, organizations should also ensure that systems are regularly backed up and stored offline; and for ICS operations, in particular, backups should include the last known good configuration data to ensure the fastest system recovery possible.
Finally, organizations reduce their attack surface through network segmentation, improved access, and authentication systems and technology, while increasing visibility into their networks to identify suspicious activity or anomalies before they become a full-blown attack.
To Learn More About How to Protect Yourself from Ransomware Attacks Please Call Us – as Always We Are Happy to Help – 1 (888) 982-0678







