Phishing and Wire Transfer Scams are Victimizing Corporate Executives
“CEO Fraud” or “CEO Fraud Phishing” Doubled Over the Past Year
CEO Fraud is a scam in which cyber criminals either spoof or literally take over company email accounts to impersonate executives in order to try and trick an employee in accounting or human resources into executing fraudulent wire transfers.
The FBI has termed this criminal activity “Business Email Compromise” and defines BEC as “a sophisticated scam targeting businesses working with foreign suppliers and/or businesses that regularly perform wire transfer payments. The scam is carried out by compromising legitimate business email accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.”
According to FBI statistics, CEO fraud is now a $26 billion scam. Last year, BEC crimes increased by over 100% in victim losses. This version of phishing cybercrime has been reported in all 50 states and in 150 countries. Victim complaints filed suggest that these fraudulent wire transfers have been sent to banks from over 130 countries.
This is How CEO Fraud Works – A Real Life Example
According to an article in the Wall Street Journal, Frank Krasovec took on a $1 million personal line of credit from PlainsCapital Bank near Dallas, Texas. A few months later, he went on a business trip. When he returned, $450,000 was missing. Mr. Krasovec, the chairman of Dash Brands Ltd., which owns Domino’s Pizza Inc. franchises in China, said he soon learned that someone had hijacked his email and asked his assistant to wire the money to a Hong Kong account.
The largest banks are most likely to be conduits for the wire-transfer scams, according to the American Bankers Association. But community banks, with less sophisticated e-mail filtering technology or security controls are vulnerable.
China-based Cybercriminals are Responsible for a Significant Percentage of CEO-Fraud
The FBI received reports of nearly $1.8 billion in losses from this type of scam in 2019, up from about $1.3 billion the prior year. However, the FBI estimates total global losses at $26 billion over the past 3 years which include those victim losses not reported. The funds primarily go to banks in Hong Kong and mainland China, where chances of recovering the money are slim, the FBI said.
The funds primarily go to banks in Hong Kong and mainland China, where chances of recovering the money are slim
Victims of wire transfer fraud often include “the elderly, college students, nonprofits, religious organizations, celebrities, CEOs of companies,” FBI Supervisory Special Agent Zacharia Baldwin said in an interview. “It could be anybody.” However, “CEO Fraud” has become very lucrative over the past several years because of the sophistication of spoofing e-mail addresses or compromising an executive’s e-mail account.
Increasingly, cybercriminals are compromising an executive’s email account by using passwords made public on the dark web from previous data breaches. The hackers then take over the e-mail account and impersonate the victim, asking assistants or colleagues to make a wire transfer on the executive’s behalf.
In Mr. Krasovec’s case, the e-mail from the hacker was sent to his assistant saying “Carol…please wire $150,000.” An e-mail attachment with transfer instructions showed an intimate knowledge of his accounts, Krasovec said.
The assistant asked Krasovec’s community bank, PlainsCapital to wire the money. PlainsCapital called Carol to confirm the request, then made the transfer. Three days after the initial transfer, the cybercriminals took the bold step of asking Mr. Krasovec’s assistant to wire another $300,000. In the meantime, the hackers had changed Krasovec’s email settings so that the e-mail to Carol was deleted, according to Kyle Camp who performed the forensic investigation on the victim’s systems.
When Krasovec returned Carol suggested that she took care of the wires; Krasovec responded, “what wires?”
Like so many other cybercrimes we discuss in this blog, social engineering is a critical piece to making this crime successful. Thus, no matter how much security technology an organization employs, the sophistication of the criminals to circumvent technology by collecting e-mail passwords on the dark web, searching for executives who may be traveling or out of reach, learning their assistant’s name, their banking institution and account numbers and other personal information is very difficult to defend against.
Krasovec called PlainsCapital Bank, who suggested there was nothing the bank could do and according to Krasovec, stopped returning his calls. Krasovec is now suing PlainsCapital according to the Wall Street Journal, saying he shouldn’t have to repay the stolen money because the bank failed to put proper anti-fraud controls in place.
On the other side, PlainsCapital Bank said in a court filing that the loss was “undoubtedly the fault of Mr. Krasovec’s own to implement appropriate internal controls to prevent his company and its employees from falling victim to a third-party scam.” The bank said in filings that Mr. Krasovec must repay the money with interest.
PlainsCapital Bank said the loss was “undoubtedly the fault of Mr. Krasovec’s to implement appropriate internal controls to prevent his company and its employees from falling victim to a third-party scam.”
Under the years-old, pre-internet consumer-protection laws, victims are often entitled to refunds of unauthorized charges. However, refunds do not apply to wire transfers requested from a customer even if that the wires requested were from an imposter rather than a customer like Krasovec, according to the American Bankers Association.
Defending Against CEO Fraud or Spearphishing
First, let’s start with technology. E-mail filtering or e-mail content filtering is normally the first step organizations take in preventing unauthorized e-mail from coming into the organization. Security organizations provide solutions that filter out e-mail from known spammers who are on RBL’s or reputation blocklists, suspicious IP addresses or URL’s, known malware through anti-virus capabilities, and content analysis that may block e-mails if certain content, like an attachment, may pose a threat.
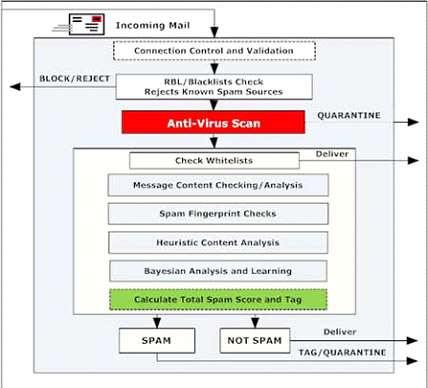
300 Billion E-mails are Sent Daily Around the Globe and Spam is 55% of All E-mails
Second, the second level of Advanced E-mail Protection that leverages AI or artificial intelligence to identify low reputation domains of the sender, URL’s that may not match the company brand associated with the e-mail (think “micro-soft.com”), identify malicious links in the content of the e-mail and other capabilities. Advanced E-mail Protection that leverages AI and machine learning to understand phishing tactics are beginning to help close the gap between e-mail filtering and the millions of phishing e-mails that make it through that first line of defense.
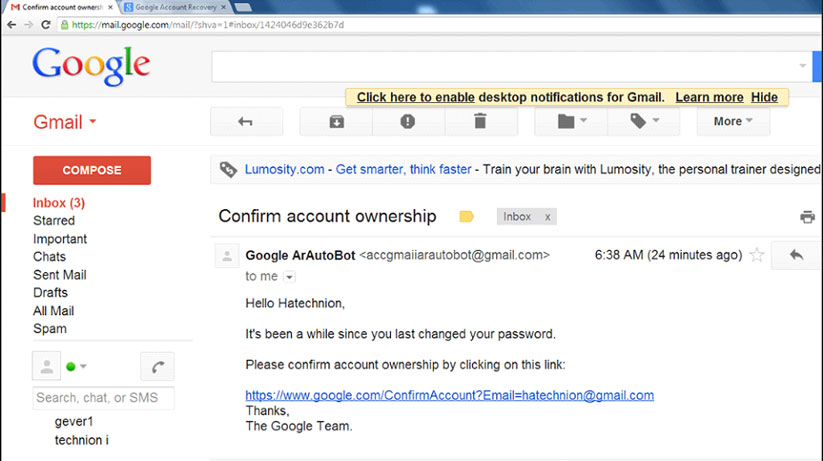
Third and most importantly, social engineering, phishing, spear-phishing and the like has become incredibly sophisticated. Domain spoofing, clone phishing, corporate account takeover, evil twin phishing, brand impersonation, and many more are too advanced to expect users to spot every malicious e-mail. That said, with the investment in technology, organizations need to train users on the very basics.
For example, company policy should stay ahead of cybercriminal tactics like CEO-fraud and instruct employees not to wire funds without authentication. Users should understand that attachments and links embedded in e-mails are never to be trusted on their faces. Look for typos, misspellings, and poor branding. Cybercriminal purposely makes these mistakes in their phishing e-mails because they are “bottom-fishing” for the uninformed or negligent users that will blindly click on links and open attachments.
To Learn More About How to Protect Yourself from CEO-Fraud Attacks Please Call Us – as Always We Are Happy to Help – 1 (888) 982-0678







