How to Improve Your SOCs Effectiveness – Part 2
Four Recommendations to Improve the Effectiveness of your SOC
The ultimate goal of this blog post is to provide 4 or so understandable, actionable recommendations for improving SOC effectiveness. To get there from here let’s discuss the mission of an SOC and the most critical elements that SOC personnel should understand in order to achieve that mission.
Recommendation 1 – Align SOC Responsibilities with the Mission of the Business
First, a significant element of a SOC’s job is to maintain and provide an understanding of the organization’s defensive posture and communicate it to the business or management. IT assets and challenges in most organizations are constantly in flux with the challenges we discussed in part 1 of this blog post; cloud migration, mobile, BYOD, threats, vulnerabilities, new technology, mergers… you see what I mean I’m sure.
SOCs must constantly evaluate their security risk posture as the organization’s technology evolves, threats change, vulnerabilities surface and a variety of other variables. The bottom line is whether they use CIS 20, ISO, NIST or another risk-based control framework, they need to understand where their weaknesses are and how to prioritize fixing them.
The SOC is tasked with gathering and assembling the following three components in order to help the business understand the organization’s overall security posture so that the business can manage the risk:
- Information – Sensor data, contextual data, cyber intel, news events, vendor product vulnerabilities, threats, and taskings
- Analytics – Interpreting and processing the information
- Visualization or Scoring – Depicting the security posture information either in visual form or a scoring system that the management team can understand
Recommendation 2 – Understand Your Security Posture and Manage Tasks from a Risk Management Perspective
Second, now that we understand the business risk, our security posture, our weaknesses and the priority of fixing those weaknesses we have a foundation to build on. We can now stop patching every two weeks or month and patch by system value, application criticality and seriousness of vulnerability – essentially by risk. SOC personnel will become for more effective, efficient operators because they consistently have a prioritized list of what they need to do to make the organization more secure and reduce overall risk.
Risk management and understanding security posture is more that asset inventory, vulnerability assessment and patch prioritization so let’s simply lay out the three areas of the business that could be considered in the risk control and security posture assessments:
- Network – Number, type, location, and network connectivity of IT assets, including desktops, servers, network devices, mobile devices, and outsourced “cloud” systems
- Mission – The lines of business and mission the constituency engages in, including their value, which may be expressed in revenue, expenditures, or lives
- Geographic/physical location where different parts of the mission occur
- The business relationship between the constituency and external parties
- Threat and adversaries
- Capability, including skill level and resources
- Intent and motivation
- Probability of attack
After Gathering the Information for the Risk Control and Security Posture Assessments Start with the Following Questions:
- What is the patch status of the enterprise? Which patches do we really need to care about, and which are less important?
- Is my constituency facing the serious threat of a targeted external attack such as a spear-phishing campaign?
- What is a real-time picture of possible intrusions or, at the very least, known malware?
- To which systems should I apply different security controls that will provide the greatest overall help in preventing a given set of attacks?
- What is changing about the threats faced by the constituency? How are their TTPs changing, and what do I have or need to detect and defend against those new threats?
- Who is acting outside their typical lines of behavior, and is this cause for concern?
- What is the relevance of the attacks I’m investigating within the context of the constituency mission?
Recommendation 3 – Leverage Technology to Improve Efficiency and Effectiveness of Your Analysts – The SIEM (Security Information and Event Management)
Now, let’s discuss technology. As we suggested in part 1, we have AV’s, Firewalls, IDS/IPS, EDR, Sandboxes and so many other types of IT security technology. We know that much of this technology is not leveraged correctly in the SOC and that SOC analysts are overwhelmed by the inaccuracy and noise that much of this technology creates.
The technology’s value proposition was to make the SOC analysts more productive by collecting, normalizing, assessing and reporting in an automated way so that Tier 1 analysts could deal with only important events. It hasn’t worked out that way, unfortunately.
To Read More About SIEM’s and their Capabilities Read this Blog Post – What is a SIEM? https://secureops.com/security/blog-what-is-a-siem/
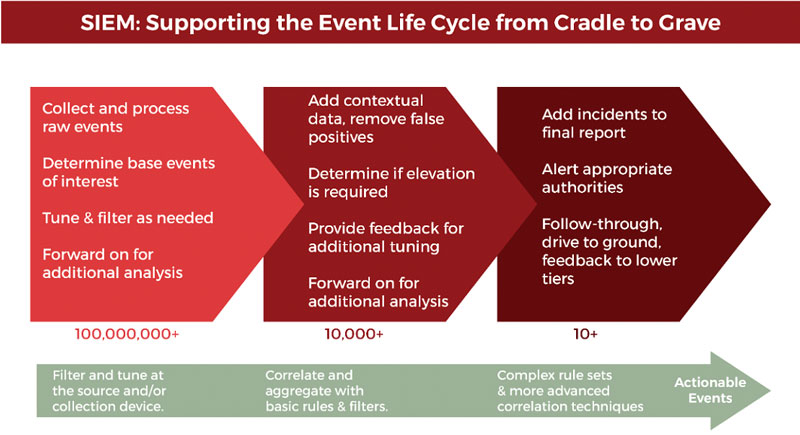
We want to be clear about the next point while keeping it simple – your first line of network defense is your firewall. The firewall allows or denies traffic in or out, while a SIEM analyzes log files. Within your IT infrastructure, you may have lots of different devices that are generating a massive number of log files.
A SIEM brings together the log data from disparate devices into a management layer, which provides visibility and the ability to detect and respond effectively to security breaches. A SIEM triages the logs for you by analyzing all the log data, and through correlation rules, behavioral analysis, and machine learning, filters down and extracts events of interest.
A SIEM will typically alarm in the case of brute force login attempts, traffic going and coming from suspicious sources, policy violations, and so many other issues.
These false positives fall into three buckets:
- Indicators of operational issues
- Policy concerns
- Nonactionable information
We could spend pages going through the different types of alerts in the categories above, however, I would suggest researching which alerts should be handled and which should be suppressed in your specific organization.
The bottom line is If there are more alerts in one day than your security personnel can review, then some level of suppression must be implemented that will bring the most important items to their attention the fastest. Reducing the number of alarms that are emanating from your SIEM allows your security team to be more efficient in the use of their time and more effective in focusing on and resolving important issues quickly when they arise.
Recommendation 3 – Leverage Technology to Improve Efficiency and Effectiveness of Your Analysts – IDS/IPS (Intrusion Detection and Intrusion Prevention)
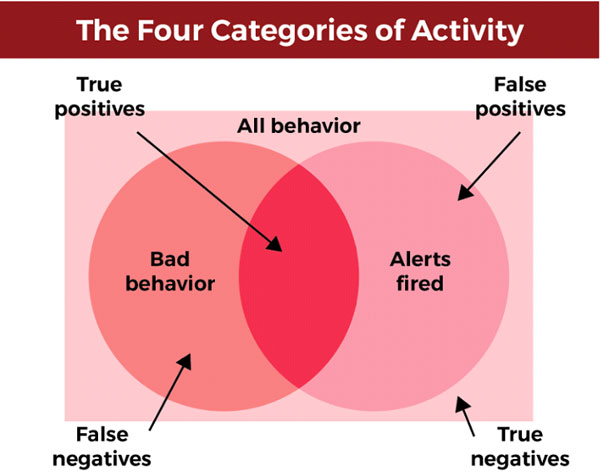
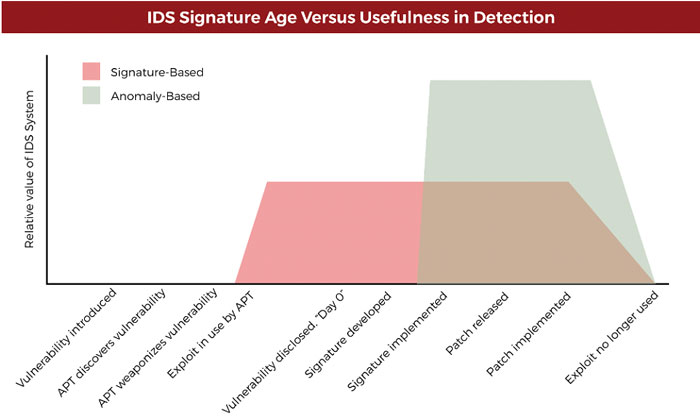
An intrusion detection system (IDS) will analyze and monitor network traffic for signs that indicate attackers are using a known cyberthreat to infiltrate or steal data from your network. IDS systems compare the current network activity to a known threat database to detect several kinds of behaviors like security policy violations, malware, and port scanners. NOTE: This is a passive technology that can only identify an attack, not stop one like a SIEM.
An intrusion prevention system (IPS) lives in the same area of the network as a firewall, between the outside world and the internal network. IPS proactively deny network traffic based on a security profile if that packet represents a known security threat. NOTE: This technology can block traffic that could be malicious.
IDS/IPS technology behind your firewall can uncover thousands of threats daily that get past the firewall; they can also identify threats that are trying to leave the network. The challenge is that an analyst must proactively update the IDS/IPS with threats and policies and monitor it 24x7x365.
Depending upon how often an organization is targeted, IDS/IPS devices that are not tuned properly like the problem we discussed with a SIEM, can generate thousands or millions of false-positive alerts each day and can generate false-negative responses to true threats. Obviously, like the alerts with the SIEM, the analyst cannot efficiently do their job and identify real threats and take immediate action.
The reality is that if your security devices continually send false alerts, analysts will likely ignore them as well as those that are true-positive alerts. Many companies have been breached because their security teams ignored an alert that should not have been.
You want alarms to be triggered in the event of malware, web attacks, and data compromise but not traffic-type or equipment-related or non-malware alarms. The Defense in Depth model which includes layers of security technology including SIEM’s and IDS/IPS hasn’t been bulletproof because each technology throws off an alarm and analysts simply ignore it – exactly what happened in the target breach.
Conclusion – Empowering the Analyst to Improve SOC Effectiveness
I realize I didn’t go into how to tune your SIEM or IDS/IPS technologies properly in this blog post; frankly to provide that information would take dozens of pages. In this post, as I said at the outset, I simply wanted to choose 4 activities that an SOC could take to improve effectiveness.
Aligning the business needs with the SOC responsibilities, taking a risk management approach to SOC responsibilities and tuning your SIEM and IDS/IPS technologies are consistently at the root of many issues that stop an SOC from being effective and efficient.
To Learn More About How to Empower Your Security Analysts and Managed Your Security Technology including SIEMs, IDS/IPS and Firewalls please call us – as Always We Are Happy to Help 1 (888) 982-0678







