SANS – The Five Most Dangerous Cyberattacks
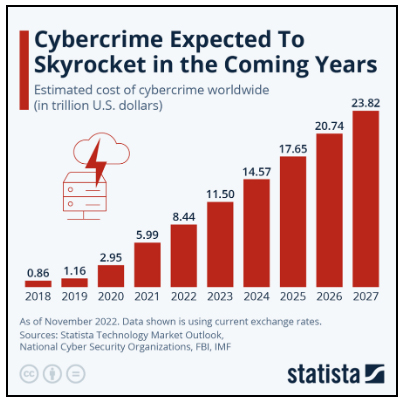
According to SANS Institute Analysts, in today’s interconnected world, cybersecurity has never been more critical. The sheer scale of cybercrime today, and the boldness of attackers, is hard for many business leaders to fathom – 450,000 new pieces of malware are detected each day, and 3.4 billion phishing emails hit inboxes. From the latest social engineering scams to zero-day vulnerabilities in software, cybersecurity threats keep evolving. To help you stay ahead of the curve, this blog post will introduce the five most dangerous cyberattacks and provide practical advice on how to defend against them.
Trend #1 – Adversarial AI
Adversarial AI is a type of machine learning that involves designing attacks against AI systems. By exploiting zero-day vulnerabilities, ransomware campaigns can become even more powerful. To defend against adversarial AI, it’s essential to identify and patch software flaws before attackers can exploit them. Invest in advanced threat detection systems and implement regular patching procedures to stay secure.
With adversarial AI attacks, threat actors are manipulating AI tools to amplify the velocity of ransomware campaigns and identify zero-day vulnerabilities within complex software, said Stephen Sims, SANS fellow, and offensive cyber operations curriculum lead.
Cyberattack #2 – ChatGPT-Powered Social Engineering
ChatGPT-Powered Social Engineering is a technique used by hackers to manipulate employees into divulging sensitive information or installing malware. This technique targets individual employees and can bypass traditional security measures such as firewalls or antivirus software. To defend against ChatGPT-Powered Social Engineering, it’s essential to educate employees on how to recognize and react to suspicious messages. Implementing multi-factor authentication and sandboxing can also help defend against these attacks.
Cyberattack #3 – Third-Party Developer Attack
The next most dangerous attack technique explored was third-party developer attacks (also known as software supply chain attacks) chiefly a rise of targeted attacks on third-party software developers to infiltrate enterprise networks through the supply chain, said Dr. Johannes Ullrich, SANS Technology Institute college dean of research.
A Third-Party Developer Attack is a sophisticated type of cyberattack that targets software developers through the supply chain of enterprise networks. One of the most dangerous aspects of this cyberattack is that it can go undetected for months, giving hackers ample time to steal sensitive data. To defend against third-party developer attacks, it’s essential to perform regular code reviews and insist on strict code-signing policies.
Cyberattack #4 – SEO and Paid Advertising Attacks
SEO and Paid Advertising Attacks use marketing strategies to gain initial access to networks. By using fake SEO pages or malvertising tactics, hackers can trick users into downloading malware or divulging sensitive information. To defend against these attacks, it’s essential to use up-to-date antivirus software and to educate users on the dangers of clicking on suspicious links.
Cyberattacks that take advantage of vulnerabilities in websites are known as SEO poisoning. They usually involve manipulating search engine rankings and adding malicious files for visitors to download.
For example, the Solar Marker campaign targeted over 2K search terms which lured visitors to click on a link that would download a pdf file that actually contained a malicious file, allowing access to their data and computers.
Cyberattack #5 – Ransomware Attacks
Ransomware is one of the most dangerous types of cyberattacks currently in circulation. It involves encrypting sensitive data and then demanding a ransom payment to decrypt it. Once ransomware enters your system, it can spread quickly and compromise all the sensitive data contained within. To defend against ransomware, it’s essential to implement a regular backup schedule and to educate employees on the importance of avoiding suspicious downloads or attachments.
There are now quite a few different types of ransomware attacks, including:
- File-encrypting ransomware: This type of ransomware encrypts the victim’s files and demands a ransom payment in exchange for the decryption key. Examples of file-encrypting ransomware include CryptoLocker, WannaCry, and Petya.
- Screen-locking ransomware: This type of ransomware locks the victim’s computer screen, preventing them from accessing their computer. The ransom demand will typically be displayed on the screen. Examples of screen-locking ransomware include FBI Moneypak and Police Ukash.
- Mobile ransomware: This type of ransomware targets mobile devices, such as smartphones and tablets. Once the device is infected, the ransomware will lock the screen and demand payment. Examples of mobile ransomware include Android Defender and Charger.
- Ransomware-as-a-service (RaaS): This is a type of ransomware attack where criminals sell ransomware to other criminals who then carry out the attack. The RaaS provider takes a cut of the ransom payment as a fee for their services. Examples of RaaS include Cerber and Satan.
- Doxware: This type of ransomware not only encrypts the victim’s files but also threatens to publish sensitive data if the ransom is not paid. This can include personal information, financial records, or confidential business data. Examples of doxware include Maze and Ragnar Locker.
Conclusion
Securing your digital assets and data is critically important in today’s interconnected world. As we’ve seen, the landscape of cybercrime is vast and varied, constantly evolving along with the technology it preys upon. The five most dangerous cyberattack tactics discussed in this blog post are just the tip of an iceberg of threats for businesses to consider when crafting their cybersecurity strategies.
Whether you’re a senior IT executive or just getting started on your cybersecurity journey, every organization needs to be vigilant about potential vulnerabilities and always have security measures in place. If you need help assessing your current state of security or developing a plan for reducing business risks from cyber threats, don’t hesitate to reach out to our experienced team SecureOps. We offer consulting services that can help protect the IT infrastructure and data assets at all levels of your organization so you can focus on driving success without fear of any malicious attacks occurring.
To Learn More About How to Defend Against Malware Attacks or If You Have Been Attacked, Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/







