Building a Next-Generation Security Operations Center
Building an enterprise Security Operations Center (SOC) calls for careful planning and the precise coordination of people, processes, and technologies, as we covered in our previous post, 7 Steps to Building a Security Operations Center.
However, once you’ve established a solid foundation, that’s just the start. You need to iteratively improve and modernize your SOC as the cyber threats it’s designed to fend off evolve.
In this post, we’ll consider several strategies you can adopt to take your SOC from good to great, focusing specifically on industry frameworks, technologies, and personnel.
SOC Industry Frameworks Come of Age
Every SOC needs formal security policies and procedures to be written, enforced, and regularly reviewed. The good news is that creating these isn’t something you need to do from the ground up. They’re readily available from the likes of the NIST Security Operations Center Framework (CSF) and MITRE ATT&CK knowledge base.
These standards are continually being extended and refined and new use cases are being explored by your peers in the industry.
Let’s consider some recent developments in these areas.
Coming Soon: NIST’s CSF 2.0.
The CSF offers extensive, actionable guidance for SOC operations. It covers all aspects of cyber threat handling, including identification, protection, detection, response, and recovery. Periodically revisiting the CSF and refining your SOC processes will allow you to ensure your SOC is comprehensively aligned with NIST best practices.
Also, don’t forget that the CSF is a living document that evolves over time. NIST initially produced the framework in 2014 and updated it in April 2018 with CSF 1.1. After considering industry and stakeholder feedback, NIST is currently planning another, even more significant, update to the framework: CSF 2.0. These updates are designed to help the framework:
- Keep pace with both technological and threat-related trends
- Integrate lessons learned
- Move best practice to common practice
According to NIST, CSF 2.0. will “reflect the ever-evolving cybersecurity landscape and help organizations more easily and effectively manage cybersecurity risk.”
NIST relies on and is currently actively seeking stakeholder feedback as they finalize their latest CSF release – so why not get involved by attending their public webinars and workshops and reviewing initial drafts of CSF 2.0?
More than a Reference Architecture: New Use Cases for the MITRE ATT&CK Framework
Since its creation in 2013, security operations professionals have relied on the MITRE ATT&CK framework as a reference architecture. This knowledge base is a powerful tool for anyone seeking to better understand adversary tactics and techniques based on real-world observations.
According to recent research, 48% of organizations use the MITRE ATT&CK framework “extensively” for their security operations, while 41% use it on a limited basis. When asked how important MITRE ATT&CK is for their future security operations strategy, 19% claim that it’s critical, and 62% say it’s very important.
Like NIST’s CSF, MITRE ATT&CK is a living and breathing framework. Today’s security teams are building on this foundation by experimenting with new use cases to derive even greater benefits. A new report outlines some of these novel applications and use cases:
- 38% of organizations now use MITRE ATT&CK to help them integrate threat intelligence into their alert triage and investigations processes.
- 37 % use it as a guideline for security engineering.
- 35% rely on the framework to gain a better understanding of adversaries’ tactics, techniques, and procedures, and 34% use it to understand the full extent of cyberattacks.
- 33% turn to it to supplement the threat intelligence provided by their security technology vendors.
Looking ahead, experts foresee MITRE ATT&CK driving more continuous security testing. According to one commentator:
“MITRE ATT&CK already raised the value of threat intelligence by helping companies map atomic indicators and alerts to extended kill chains. Similarly, I believe MITRE ATT&CK will also drive the mainstreaming of continuous security testing.”
Next, let’s look at the technology aspect of the next-generation SOC.
Technologies to Future-proof Your SOC in 2023
The three key technologies within a typical SOC are associated with:
- Data Sources
Common data sources include:
- Network activity/security events such as firewalls, IDS/IPS, and vulnerability scanners
- Threat intelligence gathered from internal and external feeds
- Endpoint activity logs
- Authorization elements such as those gathered from Active directory, VPN, and SSO
- Security Intelligence Platform (including SIEM)
A security intelligence platform gathers data from all the sources listed above but also correlates it. Should a threat be detected, it will immediately send an alert to a SOC engineer.
- Case Management System
This is a ticketing system that tracks events throughout their lifecycle. It also serves as a communication point between affected infrastructure and SOC teams and users. Investing in, maintaining, and updating these infrastructure elements can be expensive, which is why many organizations rely on managed solutions from third parties to defer or offset their upfront costs.
Where Do Current SOC Technology Gaps Lie?
Forbes recently asked SOC professionals what technologies they believe they need to succeed with their plans for the coming year. Their responses were interesting:
- More Advanced Insider Threat Detection Capabilities: According to the recent SANS Institute white paper, 35% of survey respondents consider misuse by organizational insiders to be a major visibility gap in their infrastructure. It’s not surprising, therefore, that over a third say they’d like to add behavior analytics technology to their SOC to help them root out malicious insider activity based on an understanding of what “normal” user and entity activity looks like.
- SIEM-related Shortcomings: Some 18% of respondents said a better SIEM would improve their SOC’s performance. SIEM tools ingest data from disparate sources, normalize and correlate it, assign risk scores, and issue alerts and associated context to the SOC analysts tasked with handling investigations. SIEM tool deficiencies commonly cited by SOC professionals include:
- The inability to query all data to the desired depth and breadth
- Data collection or storage limitations that lead to an incomplete context of incidents
- Excessive numbers of alerts due to a lack of prioritization
- The complexity of setting up and maintaining the SIEM tool
While the importance of the correct SOC technology can’t be understated, ensuring your SOC is manned by top-notch human expertise is equally, if not more important.
This brings us to our third element of a future-ready SOC – people.
Next-generation SOC Staffing Strategies
According to the SANS 2022 SOC Survey, the greatest barrier facing security teams seeking to optimize their utilization of their SOCs is high staffing requirements. However, SOC specialists are expensive and in short supply.
To understand the problem and consider potential workarounds, first, let’s look at the key roles in a SOC team and what they do:
- Tier 1 – These are analysts who focus on fielding phone calls and catching real-time alerts and warnings in the SIEM or other sensor consoles.
- Tier 2 – SOC Tier 2 analysts’ responsibilities include investigating events and incidents to resolution, regardless of whether it takes hours or months.
- Tier 3 – These analysts are responsible for collecting trending cyber intel and analyzing network activity and adversary TTPs over months and years. This position is often the most ambiguous because analysts are asked to handle imminent threats as well as position the SOC to handle emerging threats.
- SOC Manager: This individual manages SOC operations and communications with technology leadership, such as the CISO and CTO.
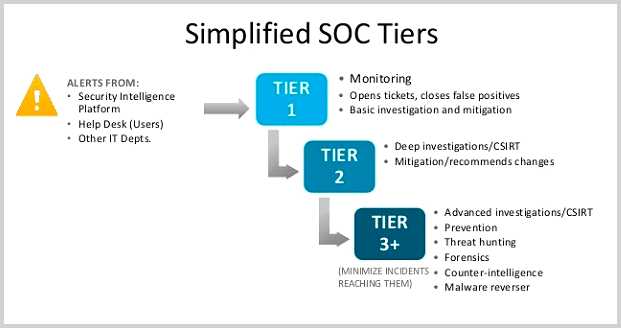
Figure 1:Typical SOC Staffing Tiers 1-3
Enterprise SOCs are well-known for high staff turnover rates – the average employee spends an average of just 26 months with an organization. This short employment average often prevents SOC teams from acquiring the organizational-specific knowledge they need to manage discovered incidents without dedicated third-party support and/or guidance from more senior colleagues.
Gartner predicts that by 2024, more than 90% of buyers looking to outsource to security services providers will focus on threat detection and response services.
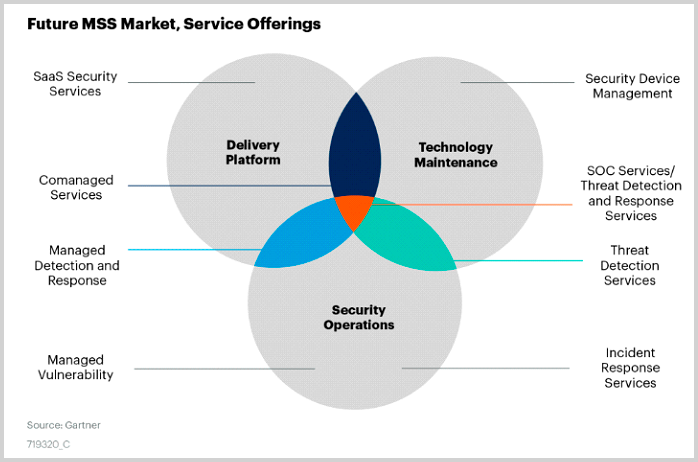
Figure 2: Future MSS Market, Service Offerings
Here are some SOC roles and tasks that are frequently outsourced:
Penetration Testing: Third-party penetration testing experts take care of performing advanced security verification using your company’s unique schedule, processes, and prioritization levels.
The best outsourcing partners will involve ethical hackers as part of the process of finding and remediating vulnerabilities in software, web applications, operating systems, networks, and more. They’ll base their penetration tests on your business and risk management requirements and focus on the areas of your IT environment deemed most critical.
24/7 Analysts: One of the most commonly outsourced SOC functions is that of the Tier 1 analyst. This employee performs 24/7/365 monitoring of security alerts and associated data feeds from systems and networks. Further, these analysts work within your processes to provide a preliminary analysis of relevant events and triage based on the criticality/severity of the event. They’ll then escalate events using your criteria and direct issues to appropriate members of incident response teams or Tier 2 analysts to eliminate threats quickly and efficiently.
Incident Handling/Response: A good outsourcing provider will partner with you to mitigate threats by leveraging their dedicated incident response experts. They’ll work within your playbooks and processes and follow key steps like generating response actions, authorizing responses, and quarantining threats. In addition, they’ll implement secure backups, leverage logs and security alerts to detect malicious activity, and monitor identity and access management.
SOC around the Clock: SOC-as-a-Service
Over the last few years, the trend toward outsourcing SOC responsibilities to specialist managed security services providers (MSSPs) has spawned what’s known as SoC-as-a-Service (SOCaaS).
In SOCaaS arrangements, the MSSP typically takes responsibility for some or all elements of the enterprise SOC. Some organizations are initially a little reticent to go this route, fearing they’ll lose control of their overall security plan. However, that’s an unlikely outcome, and most see the opposite happen – they reap the benefits of having an expert step them through the process of developing, honing, and improving their SOC strategy, ultimately feeling even more confident and in control of their operations than ever before.
When entering into a SOCaaS arrangement, you usually sign up for a fixed-price contract that comes with a monthly or annual fee. Your provider will commit to specific service level agreements (SLAs) that govern the terms of the contract, making them a more efficient and cost-effective alternative to an all-in-house SOC.
A managed service SOC can also help address any potential skills gap challenges in your security team and free up existing IT experts to focus on other business-critical issues. This ensures a reliable SOC is operational in your organization around the clock.
Conclusion
Organizations that go the outsourcing route generally report the total cost of their third-party SOC services to be significantly lower than the cost of purchasing, installing, and maintaining the same technology and services in-house. This strategy also eliminates many upfront CapEx expenditures, not to mention the cost of hiring, managing, and retaining scarce and highly sought-after SOC specialists.
SOCs play a business-critical role in protecting organizations from insider and external threats. As we move into 2023, we can expect SOCs – whether in-house, outsourced, or a hybrid models – to take their rightful place at the top of the business agenda.







