7 Steps to Building a Security Operations Center
Reviewing cybercrime statistics for the year is always a sobering exercise, and 2022 is no exception. Threat actors continue to up the ante, and data breaches grew significantly in Q3 2022, surging by 70% quarter-over-quarter.
Looking ahead to 2023, experts predict that pressures associated with economic uncertainty and inflation will create the perfect environment for cybercriminals.
Cybercrime is predicted to cost the world $8 Trillion USD in 2023 according to Cybersecurity Ventures.
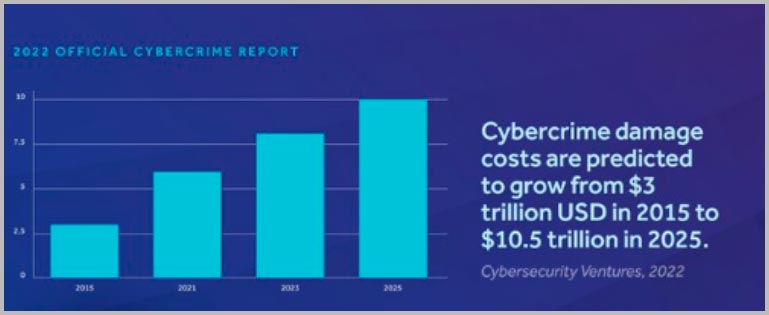
Figure 1: The Global Cost of Cybercrime
With a recession looming, security leaders face the twin challenges of cutting costs and optimizing their current security approaches in the year ahead.
In this climate, the importance of having a well-designed and responsive Security Operations Center (SOC) in place to improve threat detection and decrease the likelihood of security breaches becomes amplified.
In this post, we’ll consider the evolving role of SOCs in modern corporate cyber defense strategies and outline the steps for building one to protect your business.
What Is a Security Operations Center?
A security operations center is a physical or virtual facility designed to protect an organization from cybersecurity threats. Most SOCs are manned by security professionals and analysts who work closely with other technical experts in IT operations and development roles.
How Does a SOC Work?
The SOC team sets rules and continually monitors networks, servers, devices, operating systems, applications, and databases for signs of security anomalies and exceptions or new vulnerabilities. Threat data is collected from firewalls, intrusion detection and prevention systems, and security information and event management (SIEM) systems.
When suspicious activity or breaches are detected, these systems trigger an alert to the SOC team, which investigates and responds to them as they occur.
SOC teams typically function 24/7 in shifts to guarantee a rapid response to any incidents or emerging threats.
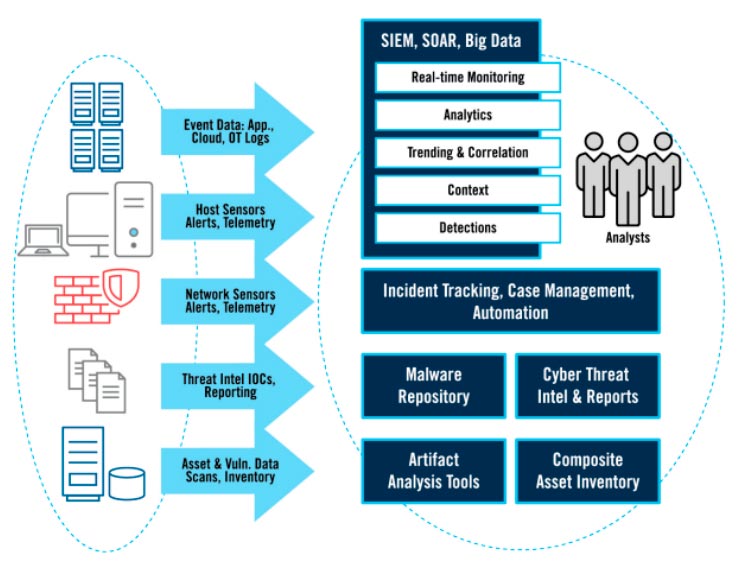
Figure 2: Typical SOC Data and Tools
What Are the Different SOC models?
Gartner identifies the six most common SOC models as follows:
Virtual SOC
- No dedicated facility
- Part-time team members
- Reactive and activated when a critical alert or incident occurs
Dedicated SOC
- Dedicated facility
- Dedicated team
- Fully in-house
Distributed/Co-managed SOC
- Dedicated and semi-dedicated team members
- Typically, 5×8 operations
- When used with an MSSP, it is co-managed
Command SOC
- Coordinates other SOCs
- Provides threat intelligence, situational awareness, and additional expertise
- Rarely directly involved in day-to-day operations
Multifunction SOC/network operations center (NOC)
Dedicated facility with a dedicated team performing not just security but other critical 24/7 IT operations from the same facility to reduce costs
Fusion SOC
Traditional SOC functions and new ones, such as threat intelligence, computer incident response team (CIRT), and operational technology (OT) functions, are integrated into one SOC facility.
In addition to these in-house models, there’s another fully outsourced model in which a service provider builds and operates the SOC with minimal involvement from the client organization (more on that later.)
How to Build a SOC in 7 Steps
Here are 7 practical steps to building a SOC for your business:
Step 1: Develop Your Strategy
The first step is to clarify your business objectives for building the SOC. Part of this exercise involves determining which systems and data are most critical to sustaining the company’s operations. Simply creating a SOC to improve your security posture without factoring in the overarching business goals could result in misalignment and even result in the SOC missing a key threat that culminates in a devastating cyber incident.
The next step is to assess your company’s existing SOC capabilities in terms of people, processes, and technology. If you’re starting from scratch, your SOC’s initial scope should be limited to core functions, i.e., monitoring, detection, response, and recovery. While fully fledged SOCs support more advanced functions such as vulnerability management, it’s a good idea to delay these until your core functions have matured sufficiently.
Step 2: Design the Solution
When designing your solution, start by selecting a few business-critical use cases and define your initial SOC solution based on these, bearing in mind that it will need to scale to meet additional future needs. Keeping your initial solution’s design conservatively scoped in the early stages will reduce the time it takes you to implement it and see results.
Follow these steps to complete the design process:
- Define the functional requirements: These should include identifying your sources of log and event data that will be monitored, identifying your sources of threat intelligence, and determining performance requirements, for example, response times.
- Choose your SOC model: This decision will be informed by your strategy and functional requirements. Here, you’ll need to make decisions about operating hours and shifts and which roles to fill internally versus outsourcing.
- Design your technical architecture: This includes specifying the composition and configuration of your solution’s components, including the SIEM platform. You’ll also need to clarify which business and information systems need to be integrated with your SIEM platform. Other actions include defining workflows for events and incidents so that they align with the processes your organization already has in place. Finally, you’ll need to decide to what extent to embed automation into your solution to gain optimum visibility of the threat landscape and thwart attacks as early in the attack lifecycle as possible.
Step 3: Develop Processes, Procedures, and Training
If you’re building a partially outsourced solution, it’s vital to work with your service provider to ensure that processes, procedures, and training are mutually agreed upon and enforced.
Step 4: Prepare Your Environment
Before you deploy your SOC, you need to check that all components are fit-for-purpose and guarantee a secure environment. This should include ensuring that your SOC staff’s devices are protected, and that robust access management and authentication mechanisms are in place.
Step 5: Implement Your Solution
Follow these steps for your initial SOC deployment:
- Bring up the log management infrastructure.
- Onboard the minimum collection of critical data sources.
- Activate security analytics and security automation and orchestration capabilities.
- Start deploying a few use cases that focus on end-to-end threat detection and response.
- Integrate threat intelligence feeds and other intelligence sources as automated inputs to enhance detection accuracy.
Step 6: Deploy End-to-End Use Cases
Now that you’ve deployed your solution’s core capabilities, you can start implementing use cases across the analytics, security automation, and orchestration tiers. This might include detecting compromised credentials or successful spear phishing campaigns.
Step 7: Maintain and Enhance Your Solution
Once your SOC is in production, it will need ongoing maintenance, such as updates to configuration settings and adjustments to improve detection accuracy. In time, you can consider adding other systems, either as inputs or outputs to the solution.
When Does it Make Sense to Outsource Your SOC?
The members of your SOC team play a crucial role on the security frontline, managing and responding to threat alerts to protect your business from potentially catastrophic breaches. However, research shows that this constant pressure can come at an enormous personal cost:
- Some 70% of SOC team members report feeling emotionally overwhelmed by the volume of alerts they receive.
- 55% admit that they aren’t entirely confident in their ability to prioritize and respond to alerts.
- High volumes of alerts leave many SOC managers unable to switch off or relax outside of work or feeling irritable with friends and family.
- While at work, 43% of SOC personnel turn off alerts occasionally or frequently, 43% walk away from their computer, 50% hope another team member will step in, and 40% ignore incoming alerts entirely.
To avoid losing their best people to burnout (and allowing preventable threats from being missed), forward-looking organizations are outsourcing their SOC to providers with sophisticated threat detection and response platforms that can intelligently correlate and prioritize alerts.
This staffing strategy improves overall enterprise protection levels and enhances in-house SOC teams’ productivity and job satisfaction.
The truth is that effective enterprise cybersecurity requires deep technical, business, and strategy expertise, and not all IT departments excel in all three areas. In fact, Gartner predicts that by 2025, a single, centralized cybersecurity function won’t be agile enough to meet the needs of digital organizations.
To quote the wise words of a Gartner VP analyst: “The most effective CISOs don’t try to do it all. Play to your strengths as a leader, and then augment your teams with those who complement your weaknesses.”
Conclusion
Let’s conclude this post with 3 critical processes one should evaluate when building their security operations center. The most crucial and first process one must consider in building a SOC is threat modeling. Threat modeling entails answering the following questions:
- What threats does my organization care about?
- What does a threat look like?
- How does the SOC block/detect the threat?
Another aspect of building a SOC is the most commonly discussed topic; technology. Cyber defense technology can be broken down into three parts. The first is to identify the data sources to use. Usually, these are driven by the playbooks on the detection portion. Common data sources are network activity/security events (firewalls, IDS/IPS, netflow, vulnerability scanners), threat intelligence (internal and external feeds), Endpoint activity (ETDR, DNS, DHCP, AV, OS logs), and finally authorization (LDAP, Active directory, VPN, SSO).
The second part is a security intelligence platform (includes a SIEM). A Security Intelligence platform is not only responsible for bringing in the data from all the data sources listed above but also correlates, identifies and alerts a SOC engineer when a threat is detected.
The third and final part is a case management or ticketing system which is used to track events throughout its history as well as a communication point between the affected part and the SOC.
A key element for managing a SOC is to ensure that the technology and platforms used sync well with the information systems of other countries and are easily serviceable abroad. There have been occasions where integrated access control and video systems that were deployed globally were overly engineered and had narrow parameters for compatibility with other systems. If a malfunction happened, let’s say in Turkey, the only tech available to fix it would have to fly in from Texas.
There are many moving parts to building a Security Operations Center but thinking of them in sections and tackling each through a threat model exercise makes the challenge achievable.







