DDoS Attacks on Critical Infrastructure: A Look at Hydro-Québec’s Website Outage
Recently, the critical infrastructure of Canada has once again become the target of cyberattacks. Pro-Russian hacking groups have launched a series of DDoS or denial of service attacks, causing operational disruptions and website outages across various government and civilian organizations. One of the most significant attacks has been on Hydro-Québec, a state corporation that provides hydroelectricity in Quebec. The attack paralyzed its website and applications; the group responsible for the attack, NoName057, has claimed responsibility.
In this blog post, we will discuss the DDoS attack that took down Hydro-Quebec’s website and provide incident response and post-mortem steps that will dramatically improve an organization’s security posture after such an attack.
An Explanation of a DDos Attack in Simple Terms
In analyzing how the attack was perpetrated, A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming the target or its surrounding infrastructure with a flood of Internet “junk” traffic. DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices. From a high level, a DDoS attack is like an unexpected traffic jam clogging up the highway, preventing regular traffic from arriving at its destination.
A Hydro-Quebec spokesperson said no personal data was compromised. In an online post, the group NoName057 (16) announced it was behind the hack but did not specify why it reportedly targeted Hydro-Quebec. The hacker group wrote, “Continuing our visits to Canada, the website of Hydro-Québec, the company responsible for generating and transporting electricity in Quebec, was put down.”
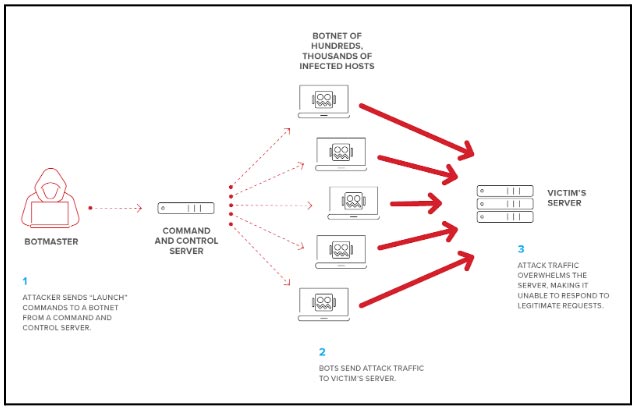
Figure 1 – Attacker Sends Commands to a Botnet, the Hundreds or Thousands of Bots Send Requests to the Targeted System, which is Brought Down by the Overwhelming Traffic
The hackers, identified as NoName057 (16), claimed responsibility for the attack. In response, Hydro-Québec said it has a dedicated team of 300 security experts to prevent and counter cyberattacks as much as possible. However, the recent attack has raised many questions about the efficacy of such measures and the preparedness of businesses to prevent such an attack.
Parts of the Quebec power utility’s site were still down around 11:00 a.m., a day after the attack; however, they were restored within 24 hours of the attack. A Hydro-Quebec spokesperson said no personal data was compromised. In an online post, the group NoName057 (16) announced it was behind the hack but did not specify why it reportedly targeted Hydro-Quebec. The hacker group wrote, “Continuing our visits to Canada, the website of Hydro-Québec, the company responsible for generating and transporting electricity in Quebec, was put down.”
Improving Incident Response Plans & Creating IR Playbooks
An important takeaway is the need for a comprehensive incident response plan. By having a plan in place, teams are better equipped to respond in a structured and efficient manner, reducing the risk of further incidents and minimizing the potential impact of the incident.
Create Incident Response Playbooks
An incident response playbook provides a standardized response process for cybersecurity incidents and describes the process and completion through the incident response phases as defined in National Institute of Standards and Technology (NIST) Special Publication (SP) 800-61 Rev. 2,5 including preparation, detection and analysis, containment, eradication, and recovery, and post-incident activities.
Here is an excellent resource for understanding how a DDoS attack IR Playbook should be created – https://www.incidentresponse.org/playbooks/ddos
Most of us in the industry know that playbooks are essential to proper incident management and cybersecurity practices. These guides structure chaotic situations, ensuring everyone on your team responds consistently and effectively to unplanned outages and security threats. With an incident management handbook, you can create a comprehensive set of processes for your team to follow, including runbooks, training exercises, and security attack simulations. This resource enables you to respond to any incident swiftly and confidently while also learning from each occurrence and continuously improving your approach.
Finally, conduct a postmortem of the attack. For postmortems to be effective, the process has to make it easy for teams to identify causes and fix them. The exact methods you use depend on your team culture; we’ve found a combination of methods that work for our postmortem teams:
- Laying out how the attack happened, understanding where it started, how it moved through the network, and other facts related to the attack.
- Create a priority list of issues that were uncovered in the postmortem discussion. You can’t fix everything at once; however, if a patch was missed or a 3rd party opened the door to an attack or a simple social engineering attack created the vulnerability a fix may be simple
- Designate priority actions with assigned Service Level Objectives (SLO) with reminders and reports to ensure they are completed.
Conclusion
Ultimately, the attack on Hydro Québec demonstrated the severity of distributed denial-of-service (DDoS) attacks and how important it is to stay vigilant against potential threats. It’s crucial for companies to have the proper security measures in place, like secure data center deployments and reliable DDoS protection solutions that can scale as needed.
Organizations must also utilize measures such as advanced monitoring systems with baseline analytics that can detect any suspicious activity, so if an attack were to occur, businesses would already have the necessary tools and resources required to effectively respond to the incident and limit business disruption while avoiding any impactful damages.
At SecureOps, we understand the importance of staying ahead of the curve when it comes to cybersecurity threats. We provide advanced cybersecurity solutions, which include both prevention and response services tailored specifically to your organization’s needs. When you need help protecting your critical data, give us a call – our experienced professionals will be more than happy to assist you in getting optimized protection from cyber threats.
To Learn More About How to Defend Against Malware Attacks or If You Have Been Attacked, Please Call Us – as Always; We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/







