How to Stop Insider Threats in their Tracks
Cybercrime is a disruptive force that costs businesses trillions of dollars every year. These damages take the form of lost and stolen data — including intellectual property — and disruption to business systems and productivity. Globally, cyberattacks increased by 125% between 2021 and 2022, and this upward trend will likely continue through 2023.
A growing share of these attacks involves company employees. These malicious insiders, termed insider threats, are current or former employees or contractors who have or once had authorized access to an organization’s network, systems, or data. They intentionally misuse this access to conduct sabotage, theft, espionage, or fraud by abusing their access or stealing materials or physical devices.
Insiders pose a serious threat to businesses because they have the knowledge and access to proprietary systems and can thus bypass traditional security measures. The nature of these insider threats is unique from other security challenges, requiring a different strategy for preventing and addressing them. Organizations must understand normal employee behavior to recognize when a trusted insider is acting unusually in a way that may be harmful to the organization.
At some point, most organizations will find themselves on the radar of hackers who have the incentive to compromise their systems. These actors are getting savvier about the tools and methods they use to avoid detection, bypass security systems, and execute attacks.
To fight back, security teams must be alert to new and emerging threats, the latest cybercrime tactics, and the defensive tools at their disposal.
In this post, we’ll review one of the lesser-talked about types of threat — those introduced by malicious or negligent insiders.
Hiding in Plain Sight
Recent research from the Verizon DBIR reveals that employees contribute to around 20% of organizations’ cybersecurity incidents.
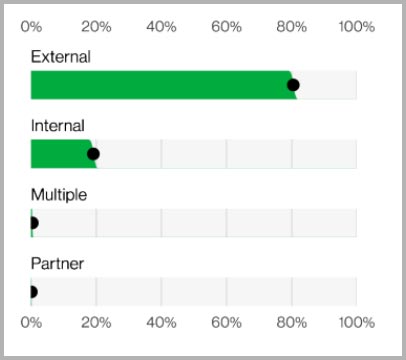
Figure 1: Actors in Breaches
Source: https://www.verizon.com/business/resources/T271/reports/dbir/2022-data-breach-investigations-report-dbir.pdf
However, on average, the scale and impact of attacks that insiders are involved in are ten times greater than those conducted by external actors. Insider security incidents are becoming increasingly common – and costly.
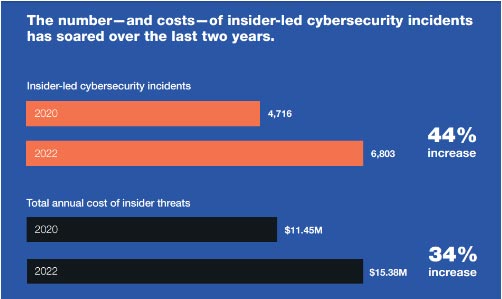
Figure 2: The Rising Number and Cost of Insider Attacks
Source: https://www.proofpoint.com/sites/default/files/infographics/pfpt-us-ig-insider-threat-infographic.pdf
Understanding the Types of Insider Threat
The first order of business in raising your defenses against insider attackers is to understand precisely whom you’re dealing with. Broadly, the culprits fall into two groups:
Desperate or Disgruntled Employees
Given the current inflationary climate and potential economic downturn that could lead to significant layoffs, it will be easier for cybercriminal groups to lure cash-strapped employees or those with feelings of job insecurity into participating in malicious activity. Ransomware gang, Lapsus$ recently made the headlines by posting a brazen recruitment call to employees of leading telecommunication, software, call center, and gaming companies, promising compensation in exchange for sensitive or privileged information.
Let’s consider some real-life examples of what can happen:
- Following perceived unfair treatment, an employee stole their supervisor’s personal information (email, phone number, etc.) and used these details to sign up for various spam sites. As a result, the supervisor and their family were subject to ongoing harassment and were subsequently forced to change all their personal information.
- A disgruntled employee socially engineered another employee to steal hundreds of thousands of customer records. They bypassed the corporate Identity and Access Management solution. Once the culprit gained access to the records, they archived the records and saved them to the drafts folder of their personal webmail account for easy access and exfiltration. After leaving their employer and finding a position at a new company, they sold the stolen information on the Dark Web.
- In October 2022, the New York Post confirmed that it had been hacked and that the attackers had used its website and Twitter account to publish offensive messages targeting prominent US politicians. The company launched an investigation into the security breach and discovered that the culprit was an employee that had been fired.
Negligent Insiders
According to additional research in the Verizon DBIR, employees are more than twice as likely to make honest mistakes and click unsafe links than they are to misuse their access maliciously. Unfortunately, the damage they can cause to the company by doing so can be devastating. Here are some of the ways workers can unintentionally expose or compromise company information:
- Employees might install unapproved tools to help them streamline their work or simplify data exfiltration. For example, a project manager could decide to sign up for an unauthorized, open-source application and use it to track the progress of an internal project, utterly unaware that this violates the company’s security policies.
- Weak passwords are the cause of many preventable compromises of corporate systems. Millions still haven’t broken the habit of using easy-to-remember but easy-to-hack passwords. A study by the Identity Defined Security Alliance (IDSA) reveals that credential-based data breaches are both ubiquitous (94% of company respondents said they had fallen victim to an identity-related attack) and highly preventable (99%). Once they’ve breached an organization’s network, threat actors can move laterally, seeking out privileged accounts and credentials to access the company’s most critical infrastructure and sensitive data.
Behavioral Red Flags to Look Out For
We recommended adopting a “defense-in-depth” approach to protect your data and reputation from being lost/damaged by a malicious or negligent insider. First, let’s look at some behavioral analysis tactics to consider:
Online Chatter
It’s vital to monitor online marketplaces, forums, and social media platforms for chatter about your organization so you can identify any warning signs of an imminent attack. Things to look out for include hackers soliciting insider knowledge or data or former employees making offensive comments. Importantly, your monitoring needs to extend to the Dark Web, where much cybercriminal reconnaissance on businesses takes place.
It’s a good idea to intensify your monitoring of online chatter leading up to, during, and immediately after what’s known as “trigger events” that could increase the likelihood of you being targeted for an attack. Such events might include a large-scale layoff or the announcement of your annual revenue figures. If you anticipate adverse reactions, you should consider implementing extra security defenses and assigning additional threat intelligence resources.
Unusual Data Downloads and Movement
Your IT team should be alerted if anyone suddenly starts downloading enormous amounts of data from corporate systems and/or sending large amounts of data outside the organization (for example, by using Airdrop to transfer files.)
Some businesses elect to use data labeling policies and tools to spot any suspicious data movements. Here, only specific data is tagged as sensitive or business critical. However, to avoid intellectual property slipping through the cracks, treating all your data as potentially sensitive is a good idea, as keeping track of all file movements to unknown devices and locations.
Requests for Escalated Privileges
Employees (and even vendors or contractors) sometimes need permission to access and view sensitive information. However, you should be concerned if such requests increase significantly for no apparent reason, mainly if the data involved is sensitive. Another potential red flag is someone requesting to view data that’s not pertinent to their role. For example, it would be suspicious if a call center employee attempted to access their supervisor’s social security number since they don’t need this information to do their job.
Ultimately, the more employees you grant access to company confidential information, the more potential insider threats you’re introducing.
Renamed Files and Extensions
Malicious insiders sometimes attempt to cover their data exfiltration activities by renaming sensitive files to make them look less sensitive. For instance, somebody who renames a PowerPoint file of an R&D roadmap to “Team Birthday Calendar” is trying to obscure its actual contents.
Another example of potentially suspicious activity is converting zip files to a JPEG extension.
Conclusion — Be Prepared, Shield Your Borders, and Educate Your Employees
Trusted insiders have the network access and insider knowledge necessary to cause significant cybersecurity incidents should they turn malicious. Many insiders seek revenge, financial benefit, or perhaps to right a perceived wrong when they turn against their current or former employer. Fundamentally, as we suggested, log management, correlation, and analysis are primary detective techniques to identify and alert insiders taking abnormal actions that may indicate a cybersecurity threat.
However, alongside behavioral and primary security observations, you should implement additional strategies and tools to ensure you can quickly detect insider threat indicators and reduce your chances of a devastating insider attack or breach:
- Create a baseline. It’s far easier to distinguish suspicious behavior from normal behavior when you have a benchmark. Fortunately, cybersecurity software is available to help you establish which devices and destinations you trust and identify suspicious data movements to locations you don’t.
- Implement a zero-trust strategy. A zero-trust approach limits employees’ permissions to those absolutely required for their role. It will reduce the potential damage insiders can do and make any requests to upgrade their privileges more apparent.
- Don’t neglect security training. Be sure to reinforce certain work habits and educate employees regularly throughout the year, especially in the event that they make an honest mistake.
Even if you’re on a limited IT budget, the long-term benefit of creating a robust insider threat intelligence program will be well worth the resources and hassle you’ll save by proactively addressing the actual risk posed by such threats.







