A Look at 2023’s Top 5 Cyber Risks – and Strategies for Defending Against Them
Last month we wrote a blog post titled “Top 5 Cybersecurity Trends to Watch in 2023,” which discussed the following five trends:
- Trend 1: Threat Actors Are Preying on People’s Emotional State
- Trend 2: Exponential Ransomware: The Rise of Double and Triple Extortion Schemes
- Trend 3: Cyber Insurance Is Coming of Age
- Trend 4: Cybersecurity Professionals Are Burning Out … and Speaking Out
- Trend 5: Risk Management is Getting Personal
In this blog post we are going to discuss NOT the “Top 5 Trends” but the “Top 5 Risks” for 2023 which include:
- Strategy 1: Build Your Resistance to RaaS
- Strategy 2: Don’t Blame Your Employees — Give Them Better Training
- Strategy 3: The AI Arms Race – Prepare for Battle
- Strategy 4: Look After Your Cyber-Talent
- Strategy 5: Review the Merits of Cyber insurance
Cybersecurity insurance and managing IT security talent populate both lists but we’ll provide more details we derived straight from the data for these topics and we’ll provide recommendations for each of the 5 strategies.
So, with that, it is the time of the year when organizations are evaluating 2022 and preparing for 2023 so we created these blog posts to help organizations think about the most relevant issues in cybersecurity. The 2022 cyber landscape was crammed jam-packed with ubiquitous threats and devastating breaches. While it’s impossible to predict the future, we can be sure that the trend of increasing volume and variety of cyber threats will keep security teams on their toes in 2023.
So again, let’s evaluate some of the most forceful cybersecurity dynamics currently in play and the strategies you can adopt to ensure you tackle them from a position of strength in 2023.
Cybercrime in 2022 – the Year in Review
First, let’s take a moment to look at the evolution and impact of cybercrime over the last year.
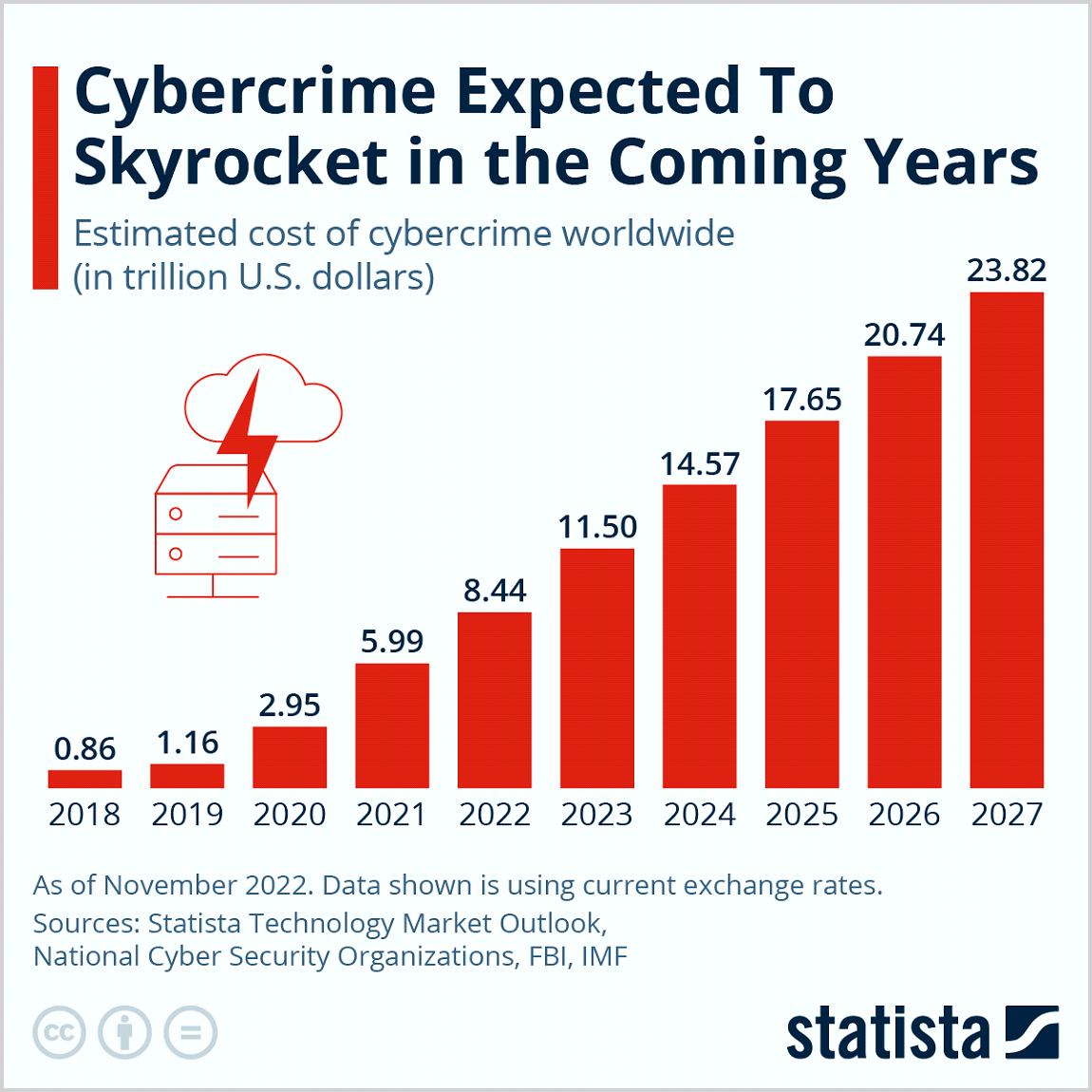
A report published by Cybersecurity Ventures asserts that the global cost of cybercrime exceeded $7 trillion in 2022. We all know that the impact of a successful cybersecurity attack – damage to brand reputation, trust, and profitability of the business – can take years to recover from.
It’s not surprising that the fightback against cybercrime is gathering momentum and attracting board-level interest. The latest figures from Gartner indicate that security and risk management will rise to the top of the list of technology priorities for medium-sized enterprises in 2023.
In a recent Wall Street Journal articles titled, “Corporate Tech Leaders Untangle Their Cybersecurity Roles,” they suggested, “across organizations worldwide, CIOs and CISOs are redefining their relationships, a shift reflecting both a surge in high-profile cyberattacks, and cybersecurity’s steady rise to the top of CIOs’ priorities—the result of continuing IT modernization, analysts say. In the most common corporate structure, CISOs report to CIOs”.
“It is cybersecurity. …That is the highest priority,” Chris Howard, chief of research at technology research and consulting firm Gartner Inc., told The Wall Street Journal earlier this year.
In a separate Wall Street Journal article titled “Cybersecurity Chiefs Are in High Demand as Companies Face Rising Hacking Threats,” data from a executive search firm suggests, “CISOs in the U.S. earned a median salary of $509,000 this year, compared with $473,000 in 2020, according to a new survey of 354 CISOs, published Thursday by Heidrick & Struggles International Inc. Total compensation, including equity grants and bonuses, rose to $936,000 from $784,000 in 2020. Last year’s survey included responses from 372 CISOs.”
In the article, Omar Khawaja, CISO at Pittsburgh-based Highmark Health, “there’s a lot more demand and the supply hasn’t exactly increased.” Mr. Khawaja further suggested that he had seen several community colleges, local banks and other companies create a CISO position in recent years because of the damaging number of ransomware attacks and the trend to “work from home” that has remained despite the decrease in Covid-related illnesses.
A Look at 2023’s Top 5 Cyber Risks – and Strategies for Defending Against Them
Let’s consider what will drive the focus of CIO’s, CISO’s and heads of IT Security globally over the next year and likely beyond:
Strategy 1: Build Your Resistance to RaaS
In just the first half of 2022, the number of new ransomware variants identified increased by nearly 100%. This explosion can be explained in part by the growing popularity of ransomware-as-as-service (RaaS) on the dark web.
Here’s how it works: We’re all familiar with food and clothing delivery apps and being able to stream our favorite media and entertainment on demand. Similarly, cybercriminal organizations are using a subscription-based services model to offer their “customers” plug-and-play ransomware strains.
RaaS kits are deemed by users as a relatively easy path to a quick payday. If victims resist their ransom demands, attackers up the ante by threatening to leak stolen data on the dark web. As a result, ransomware payments are rising. According to a report by the U.S. Treasury’s Financial Crimes Enforcement Network, organizations paid out almost $600 million in ransomware in the first half of 2021, which puts the U.S. on the path to surpassing the combined payouts of the preceding decade in just a single year.
We expect the RaaS market to boom through 2023 and beyond, with new exploits, services, and structured programs being offered to budding threat actors through convenient, low-cost subscription models.
Defense Strategy Elements
The first order of business is to accept that the old line that we have been hearing for the past half-decade, it’s not a question of “if” but “when” you’ll fall victim to a ransomware attack. The best way to protect yourself is through a “defense in depth” strategy:
- Deploy a mix of standard and more advanced security tools such as next-generation firewalls, EDR technology, sandbox solutions augmented with MITRE ATT&CK mappings, anti-malware engines that use AI detection signatures, and advanced intrusion detection and prevention systems. Deception technologies can also be effective in detecting attackers’ activities early in the kill chain and preventing them from moving laterally across your network.
- Invest in the latest reconnaissance tools and services to keep your finger on the pulse of dark web activity, so you can stop attacks before they happen.
- Deploy these technologies at all levels and in all locations – from your data centers to your branch offices – on a single, integrated security platform that allows you to see, share, correlate, and respond to threats as they happen.
Strategy 2: Don’t Blame Your Employees — Give Them Better Training
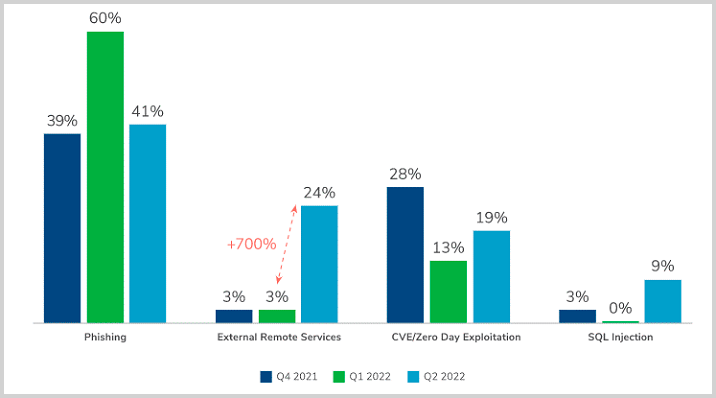
In 2022, we saw a rise in “contagious” cyberattacks that spread from one infected employee to others in an organization. Research suggests that more than 4 out of 5 organizations fell victim to such an attack over the last year. These incidents are often phishing-related and rely on social engineering methods to trick people into divulging sensitive information or installing malware on their devices.
The same study revealed that when asked to name the worst security mistakes made by their employees that would contribute to this spread:
- 83% of respondents cited poor password hygiene
- 81% called out misuse of personal email
- 76% pointed to the use of collaboration tools
Perhaps most concerning is that when asked what they expected their biggest security challenges to be in the year ahead, 40% of respondents said “employee naivete.”
Defense Strategy Elements
It’s unreasonable – and unfair – to blame or shame people who may have committed cybersecurity blunders; as you can see from the chart above, phishing is far and away the attack vector most utilized by cybercriminals. Even as external remote services earns increased attention because of the large increase of attacks using that vector due to “work from home,” phishing will likely continue to dominate as the criminal attack strategy of choice.
Organizations need to self-reflect and consider whether they can do more to better prepare employees to deal with attacks. Here are some ways to embed a culture of security awareness within your business:
- Teach basic security skills and awareness, such as the responsible use of passwords and multi-factor authentication across the board
- Mix your training sessions up and keep them fresh and fun. Include group training sessions, formal testing, email prompts, interactive videos, and one-on-one sessions with internal or external security experts
- Work with your HR team to ensure that cyber-awareness is a fundamental part of everyone’s job description in 2023
Strategy 3: The AI Arms Race – Prepare for Battle
It’s predicted that by 2030, the market for AI cybersecurity products will be worth close to $139 billion – an almost tenfold increase on the value of the 2021 market. Today, many organizations use AI defensively, for example, to detect unusual IoT behavior that could signal an impending botnet attack.
Not to be outdone, threat actors are also increasingly taking advantage of AI to enable and accelerate a host of malicious activities – a phenomenon known as the “weaponization of AI.” Their tactics range from using AI to interfere with algorithms that detect abnormal network activity to mimicking human behavior. An example of the latter is the development of deepfakes. One deepfake strategy uses the generative adversarial network (GAN) to create fake images. Another method leverages AI algorithms called encoders that can be used in face-replacement and face-swapping technology. Essentially the decoder allows one face to be superimposed onto a completely different body.
Similar AI technology has even been used to artificially “clone” the voice of senior executives to authorize transactions fraudulently!
For these reasons, the use of AI in cybersecurity is often referred to as an “arms race,” as cybercriminals hasten to ensure the newest and most sophisticated algorithms are working on their side rather than for the opposition.
Defense Strategy Elements
Consider a two-pronged approach to minimize your organization’s risk of falling victim to nefarious AI-powered cyberattacks:
- Standard mechanisms such as web filtering, antivirus software, and EDR technology can go a long way to building your organizational defenses against AI weaponization tactics.
- Following on from our previous point, one of the best defense methods for preventing AI-related attacks is cybersecurity awareness education. In addition to basic employee security training, consider adding new modules that help people spot AI-focused threats. For example, a training session on deepfakes could offer employees tips on how to identify possible deepfake videos, such as unnatural eye movements, a lack of blinking, or other inconsistent facial expressions.
Strategy 4: Take Care of and Engage Your Cyber-Talent
Earlier, we discussed the expansion of the “as-a-service” threat economy and the fact that underground cybercriminal marketplaces are now operating like mainstream businesses. But cybercrime vendors aren’t just advertising their services; they’re also listing job offers to recruit attackers with distinct skills. Some marketplaces even have dedicated help-wanted pages and recruiting staff, and job seekers are invited to post summaries of their skills and qualifications.
Unfortunately, it’s relatively easy for attackers with any skill level to enter the world of cybercrime. Recent research shows that:
- Rookie fraudsters with minimal skills earn at least $20,000 a year, while master criminals can take home up to $600,000.
- Fraud “employment” outpaces cybersecurity jobs, and there are an estimated 15 million fraudsters at large, exploiting any possible opportunity to lure victims into a trap.
Lockbit 3.0 is now even offering bug bounty programs for its malware and crowd-sourcing ideas to improve its operations!
Meanwhile, many hardworking, ethical cybersecurity specialists engaged in mainstream employment are being pushed to the brink and suffering from burnout. Working as an in-house security professional can be tough. Most teams are expected to be available 24/7 should an incident occur to react quickly, all the while staying on top of every new threat and risk. A recent study found that 66% of security professionals experience high levels of work stress, and 64% have had this stress affect their mental health.
Defense Strategy Elements
You can’t do much about individuals who choose to go and work for the dark side, but you can do a lot to look after the cybersecurity talent you have:
- One way to do so is to ease their stress levels and workload by engaging an outsourcing partner. Small and medium-sized businesses are increasingly gravitating towards these arrangements. A new report reveals that 90% of small security teams are outsourcing security mitigation to a Managed Detection and Response (MDR) service. Many are also using Managed Security Service Provider (MSSP) services (21%) and Virtual Chief Information Officer (vCISO) services (15%).
Strategy 5: Review the Merits of Cyber insurance
As the potential cost of acts of cybercrime increases, more businesses are considering investing in cyber insurance as part of their enterprise risk strategy. Cyber insurance helps companies offset the recovery costs they might incur if they succumb to a cyberattack.
However, cyber insurance is still in its infancy, and it’s not cheap. As at the second quarter of 2022, U.S. cyber insurance prices had already increased almost 80% over the prior year, and there’s ongoing debate regarding blind spots, reductions in coverage, and exclusion clauses.
To help move themselves along the maturity curve, Forrester expects cyber insurers to acquire more managed detection and response (MDR) providers in the year ahead, continuing the trend that Acrisure started in 2022. MDR acquisitions will give these insurers:
- Valuable data about attacker activity to refine underwriting guidelines
- Better visibility into the policyholder environment
- The ability to verify attestations
Defense Strategy Elements
- If you decide to allocate a portion of your IT security budget to cyber insurance, be sure to read the fine print before signing on the dotted line and that you’re crystal clear as to where your coverage starts and ends.
- Also, bear in mind that most insurers will look at your existing cyber controls when determining your premiums. The more robust your controls, the lower your premiums are likely to be.
Conclusion – Is Your Business Prepared to Confront Emerging Cybersecurity Dangers?
To thrive in 2023, your core business strategy must be security-conscious at every layer. Each new program or initiative must have the appropriate security measures embedded from the start so that you remain on the front foot in the face of cyber threats.
But this doesn’t mean rigidity or slowing down. In fact, security must move at the speed of your digital business. It must maintain pace with your business’, customers’, and employees’ needs while keeping up with the ever-changing threat landscape.
The Bottom Line – Recommendations on Protecting your Business
- Carry out regular vulnerability scanning – Uncover potential risks
- Concentrate on basic functions – Patching and hardening systems
- Disable nonessential and unused services – To stop the spread of malware
- Educate end users – Concerning phishing and other attacks
- Install the latest updates – They’ll have the latest patches to eliminate vulnerabilities
- Backup copies of your files – Ransomware has put countless organizations out of business, literally because they didn’t have their files backed up
Restrict user and local accounts – Least privilege access for all accounts will stop malware from moving through the network and finding the “crown jewels” in the organization







