Top 5 Cybersecurity Trends to Watch in 2023
There’s an oft-quoted ancient Chinese proverb that says: “May you live in interesting times.” It seems to resonate with our current situation: geopolitical upheaval, a pandemic recovery, a recessionary climate, and intensifying, ever-more sophisticated acts of cybercrime.
If cybercrime were measured as a country, it would be the world’s third-largest economy after the U.S. and China
As a new year approaches, there’s no better time for businesses to review their information security strategies in the context of evolving threats.
In this blog post, we’ll review some of the most impactful cybersecurity dynamics currently in play and consider some tools and approaches you can adopt to increase your organization’s cyber-resilience in the year ahead.
Cybercrime: The Numbers
Cyberattacks have grown in number, sophistication, and impact. The global cost of cybercrime is predicted to exceed $7 trillion in 2022 according to Cybersecurity Ventures. These costs take the form of damage and destruction of data; fraud and embezzlement; theft of intellectual property and personal and financial data; lost productivity; post-attack disruption to business continuity; the cost of fines, forensic investigation; and system restoration; and damage to organization’s brand reputation.
If cybercrime were measured as a country, it would be the world’s third-largest economy after the U.S. and China. It’s therefore not surprising that 66% of CIOs plan to increase their investments in cybersecurity in the year ahead and that worldwide information security and risk-management spending will exceed $188 billion in 2023, up 11.3% from 2021. In addition, data from Gartner indicates that security and risk management will top the list of technology priorities for medium-sized enterprises in 2023.
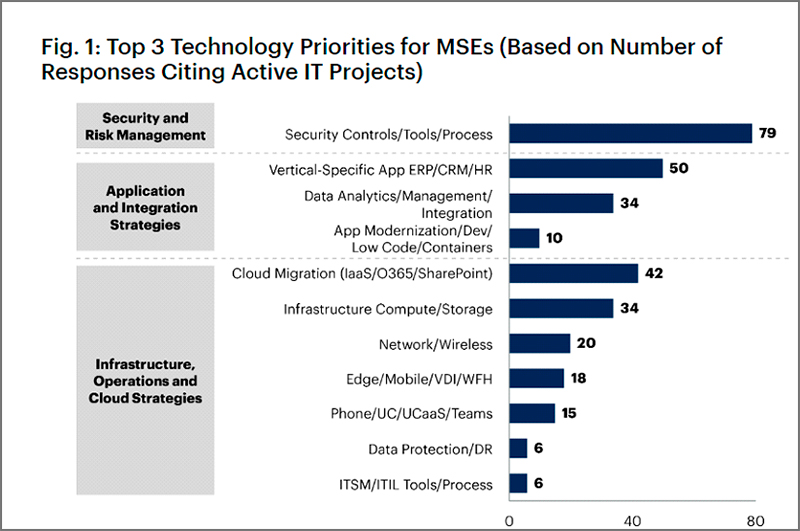
Figure 1: Source: Gartner (September 2022)
So, into which areas should this investment be channeled in the year ahead and why? Let’s consider the
trends:
Trend 1: Threat Actors Are Preying on People’s Emotional State
In 2023, we can expect the stress of the economic downturn to take both a financial and emotional toll on employees and their families (think job losses, higher interest rates, and lower living standards). More employees will become distracted, making it much easier for cybercriminals to exploit human weaknesses.
Specifically, we expect multi-factor authentication (MFA) bypass attacks to grow as threat actors explore new avenues to exploit human behavior. While MFA has been a recommended security best practice for some years, attackers are increasingly pivoting to exploit MFA’s limitations and what’s been termed “MFA fatigue” among users.
The recent high-profile data breach at Cisco is evidence of this worrying evolution. In this attack, to bypass MFA, the attacker sent a high volume of push requests to the target employee’s mobile device in the hope that they would accept the request either by accident or in an effort to silence the notifications. The threat actor also called the victim repeatedly over a period of several days, claiming to be from IT support to try to trick them into handing over information. As it turns out, they succeeded. The attacker managed to enroll new devices for MFA, authenticated to the Cisco VPN, and then moved on to using remote access and post-exploitation tools.
What Can IT Security Teams and Users do to Protect Themselves?
Review Your Authentication Methodology: MFA fatigue attacks will become less of a threat if you simply limit the number of attempts users have to verify their identity before their account is locked. Another tactic is to replace a universal confirmation signal (such as a static PIN) with notifications specific to each login attempt in question. In early 2023, Microsoft will be switching to a number-matching method for MFA using the Authenticator app.
Practice Good Identify Access Management Hygiene: While user account provisioning is generally well-administered in most organizations, the process of removing accounts that are no longer required is often less rigorous. Over time, this can lead to a plethora of orphaned accounts whose owners have left the company but whose tokens, MFA apps, and devices were never disabled.
Trend 2: Exponential Ransomware: The Rise of Double and Triple Extortion Schemes
Ransomware was rife in 2022, and very few businesses were immune. Today, some 68% of organizations globally have experienced at least one ransomware infection. Even more concerning is evidence that threat actors are growing bolder, and their monetization strategies are becoming more aggressive. Specifically, we’re seeing an evolution from straightforward data encryption to double and triple extortion schemes.
Double extortion ransomware attacks both encrypt and exfiltrate a company’s data. Only one gang used the double-extortion tactic back in 2019, and by early 2021, 77% of attacks involved threats to leaked data. With the latest trend, triple extortion, attackers demand payments not only from their primary target organization but also from any entities that a data leak may affect. These victims might include clients, partners, suppliers, and even patients if the target is a healthcare provider.
What Can IT Security Teams and Users do to Protect Themselves?
Prevent Initial Access: Double and triple extortion ransomware schemes initially utilize the same methods to gain access to their targets’ networks as any traditional ransomware attack. You can reduce the chances of a successful network breach through awareness training for employees, MFA and password policies, and regular patching of all known vulnerabilities.
Prioritize Backups and Data Encryption: If your network is breached, having a recent offline backup can protect against the first level of a ransomware attack, allowing you to recover your data. Add another layer of protection against double extortion attacks by encrypting your data so that if it’s stolen for use in an attempted data leak, it won’t be readable by your attackers.
Trend 3: Cyber Insurance Is Coming of Age
In the wake of increasing numbers of ransomware attacks and other flavors of cybercrime, more organizations are purchasing, or at least considering taking out, cyber insurance. Essentially, cyber insurance is designed to offset the recovery costs that a business would incur if it were to fall victim to a cyberattack. These might include non-IT costs flowing from the incident, such as PR fees to help repair reputational damage and legal fees.
Another reason that cyber insurance is growing in popularity is that it grants companies access to a pool of experts contracted to their underwriter or broker. These might include incident response or forensics service providers, or even law enforcement contacts who can help the organization respond and recover.
However, cyber insurance is still an evolving risk management tool and it’s important to be aware that the nuances of these agreements can be complex and filled with exceptions. Specifically, it’s vital to understand the exclusion clauses associated with any given policy. A recent example of an exclusion clause impacting insured organizations is the NotPetya attacks against Mondelēz International and Merck. As NotPetya was allegedly the brainchild of a nation-state-backed entity, cyber insurance companies deemed that the ransomware attacks triggered the “act of war” clause in the insurance policy. This led to protracted legal battles between the victims and their insurers.
What Can IT Security Teams and Users do to Protect Themselves?
Understand the Fine Print: Before signing on the dotted line, ask a series of questions to understand the precise limitations of your coverage. It is also important to not over-insure or have overlaps in your coverage. For example, a ransomware attack may be deemed a criminal act which can muddy the waters if you also have separate criminal insurance coverage.
Continue to Invest in Your Security Program: Cyber insurance isn’t cheap. As of the second quarter of 2022, U.S. cyber insurance prices had already increased 79% over the prior year. Most insurers will evaluate your existing cyber controls to gauge your premiums. It follows that the better your controls, the lower your premiums are likely to be.
Trend 4: Cybersecurity Professionals Are Burning Out … and Speaking Out
For years, cybersecurity experts have been in high demand, and the war for this type of talent will certainly continue to rage into 2023. Interestingly, it appears that more cybersecurity employees are experiencing overwork and burnout due to these teams being chronically understaffed. This isn’t a new phenomenon in the ICT sector. Earlier this year, we read reports of burnout causing the hospitalization and even deaths of tech employees in Australia and China. Overburdened cybersecurity professionals are not immune.
Working in-house as a cybersecurity professional isn’t easy. Teams are expected to be available 24/7 when major incidents strike, deliver results in tight timeframes, and continually monitor every new threat and risk. A recent study found that 66% of security team members experience high levels of work stress, and 64% have had work stress affect their mental health.
We’re also seeing more cybersecurity employees coming forward as whistleblowers, speaking out about toxic and unethical work environments. In some cases, individuals had tried to alert leadership about serious security issues in the organization and subsequently were either pressured to conform, or they were ignored, or sidelined. One example is Twitter’s former head of security, who recently filed a whistleblower complaint against his former employer. He cited “extreme, egregious deficiencies” in the company’s cybersecurity program and that Twitter misled its board of directors and regulators regarding its security vulnerabilities and protocols.
What Can IT Security Teams and Users do to Protect Themselves?
Understand the Balance of Power: Despite a recessionary climate, cybersecurity professionals can pick and choose where they work, and increasingly, they’re coming forward to demand accountability for unfair and unethical work practices. The SEC stated this year that it has issued “whistleblower rewards” of over $1.3 billion in total to 278 individuals over the last decade. All this means that leadership teams need to place ethics and trust high on the boardroom agenda.
Engage an Outsourcing Partner to Ease the Burden on Internal IT Teams: Outsourcing is a sensible strategy for organizations struggling to attract scarce cybersecurity talent and wanting to avoid overworking their internal teams. Small and medium-sized businesses are increasingly gravitating towards these arrangements: A recent survey revealed that 90% of small security teams are outsourcing security mitigation to a Managed Detection and Response (MDR) service while also using Managed Security Service Provider (MSSP) services (21%) and Virtual Chief Information Officer (vCISO) services (15%).
Trend 5: Risk Management is Getting Personal
Cybersecurity is becoming recognized as more of a business risk rather than just a problem for the IT department. In the year ahead, we’ll continue to see a shift in formal accountability for the handling of cyber risks from security leaders to the C-suite. According to Gartner:
- 75% of CEOs will be held personally liable for cyber security incidents by 2024.
- 50% of C-level executives will have performance requirements related to risk built into their employment contracts by 2026.
In addition, the proposed U.S. Securities and Exchange Commission reporting requirements for more transparency will force companies to improve oversight and increase cybersecurity expertise at the Board level. However, it will be interesting to see how willing non-IT executives will be to accept greater accountability for cyber-related matters. The recent Uber breach verdict in a U.S. federal court set a precedent that effectively encourages Boards to shift liability directly to their CISOs. It’s not surprising that, right now, only half of CISOs report seeing eye-to-eye with their boards.
What Can IT Security Teams and Users do to Protect Themselves?
Invest in the Board-CISO Relationship: You can have the best CISO and security team in the world, but if your Board doesn’t pay them enough attention, empower them, share accountability, and invest appropriately, you’re opening the door to cyber risk and conflict.
For CISOs, effective communication is key to bridging the gap. They should avoid jargon and technical terms when speaking with Board members. They’ll get the most attention if they communicate risks in monetary value, for example, by referencing real-world numbers regarding actual losses suffered by organizations of similar sizes in their industry following successful cyberattacks.
Conclusion – The Time to Strengthen Your Cybersecurity Defenses is Now
In an uncertain socio-economic climate, it’s not easy to make failsafe predictions about the year ahead. However, one thing we do know is that cybercriminals are looking forward to a lucrative 2023. Right now, they’re hard at work coming up with new, nefarious schemes to attack businesses of all sizes and from every industry.
Understanding the evolving dynamics within the cybersecurity world can help us better confront emerging dangers and advance our roles.
To Learn More About How to Secure Your Organization Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/







