A Guide to Successfully Handling a Data Breach
We’ve written several blog posts about incident response and how organizations respond to data breaches. Each was significantly different from the others in terms of how they dealt with the topic. For example, our article, “Why Incident Response Technology has become Critical to Limiting Damage,” deals with Security Orchestration, Automation, and Response (SOAR) technologies, providing one of the best ways to automate the incident response process. By leveraging SOAR, security teams can effectively triage alerts, respond quickly to critical cybersecurity events, and deploy an efficient incident response program.
The “Incident Response Planning Best Practices” article started with a Zogby Analytics survey of 403 senior IT executives. The survey revealed that 51% of the executives thought their IT security staff “lacked a plan” to deal with the breach, 41% lacked the knowledge to handle the breach adequately, and 38% lacked the resources. Thus, we provided a plan that addressed all of the aspects of the incident response process, including legal and forensic teams, removing sensitive data, and communication plans, to name a few.
The article “Analyzing Security Incidents for a Better Future Response” discussed lessons learned from recovering from incidents and provided a guide to improving security posture. Analyzing the incident response process can strengthen the risk assessment process and future incident handling approaches to improve overall security posture.
We also quoted a recent article by American Family Insurance, an underwriter for cybersecurity insurance which discussed why organizations need to have a well-planned procedure for post-incident activity. The article further recommends, “after a cyber-attack has been suppressed, continuous caution is essential. Multiple offenders might attempt to make another entryway into networks they formerly breached. Even after attempts to eliminate an intruder and mend recognized gaps in their cyber defense.”
- Why Incident Response Technology has become Critical to Limiting Damage
- Incident Response Planning Best Practices
- Analyzing Security Incidents for a Better Future Response
Defining Incident Response’s Critical Role in Cybersecurity
Data breaches can have a devastating impact. According to the Identity Theft Research Center, 1,802 different data breach incidents were reported last year, compromising the personal data of over 422 million people. Organizations need to be prepared for such events and respond quickly and efficiently when they occur. An effective incident response plan should include measures to detect, contain, investigate, and mitigate potential risks to avoid or minimize further damage.
Furthermore, having response plans in place before an incident occurs will reduce the time it takes to respond effectively. Organizations should prioritize investing in security solutions as well as developing comprehensive incident response plans that are regularly updated to help protect their networks from data breaches and other cyber threats. By understanding the latest threats and taking proactive steps, businesses can prevent or minimize the impact of data breaches.
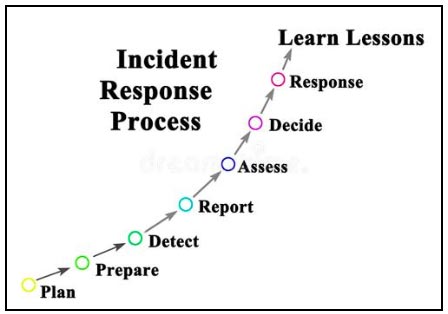
Cybersecurity leaders, including CISOs, are responsible for preventing and appropriately responding to data breaches. Mishandling these situations can lead to severe consequences, such as losing public trust and enduring irreparable reputational damage. It is crucial to avoid attempts at concealing critical cyberattacks, engaging in the blame game, providing misleading information, or attempting to downplay the severity of the situation.
Best Practices After a Data Breach
By adhering to a standard set of best practices, Chief Information Security Officers (CISOs) can effectively restore consumer, employee, and investor confidence in the wake of a breach caused by threat actors.
Vigilant and comprehensive reporting: Data breach reporting standards vary across states in the US. For example, in New York, organizations are legally obliged to promptly inform state residents about any unauthorized distribution of their personal data. Moreover, they must report the incident to the attorney general and other state government entities. Consumer reporting agencies should also be notified when the breach affects more than 5,000 individuals. Conversely, some states, like Mississippi, do not necessitate the notification of any state government entity in case of a breach. In fact, if an investigation concludes that affected individuals are unlikely to suffer any harm, organizations may choose not to inform them.
Irrespective of the company’s location and the legally mandated procedures, it is crucial for its leaders to go beyond the minimum requirements and report any data breach incident. This entails informing relevant government agencies and individuals impacted, regardless of their likelihood of being affected. While some cybersecurity leaders may be inclined towards minimal reporting to protect the company’s reputation, maintaining complete transparency is indispensable during incident response. Failure to do so may create suspicions and erode the trust that the company has built with its customers.
Providing stakeholders with transparent and honest communication: Effective communication plays a significant role when disclosing a cybersecurity incident to stakeholders. It is imperative to ensure that all stakeholders, including affected individuals, business partners, and internal employees, understand the breach, investigation, and ongoing remediation efforts.
The comprehensive post-mortem communications should include the following:
- Disclosing the scope, methods, and timeline of data access
- Describing the response measures undertaken by security teams following the breach
- Informing the number of affected individuals
- Outlining the tools and protocols to be implemented to prevent similar incidents in the future
- Advising affected individuals on protective actions for their personal interests, such as changing passwords, closing accounts, or utilizing free credit monitoring services
- Who affected individuals can reach out to for more information
When an individual discovers the unauthorized release of their personal data, it is understandable that they will feel frustrated. This frustration can be compounded when they receive an incomplete notification from the organization involved. The responsible parties must provide a direct, transparent, and comprehensive message for effective communication. By doing so, victims can feel empowered with information and gain peace of mind knowing that the company is diligently working on their behalf. A robust business continuity plan should be in place, which outlines the necessary steps for CISOs to coordinate legal, customer success, public relations, and sales support for a cross-functional response.
Considering the LastPass data breach that occurred in August 2022, it is evident that the company’s initial approach lacked transparency. LastPass initially claimed the breach was “contained,” but later, an attacker gained access to their cloud environments and password vaults, using information acquired in the initial breach. This raises concerns about whether downplaying the severity of the attack in the early stages compromised the valuable time that LastPass’s security teams could have used to change the compromised login information.
An Effective Data Breach Response Can Have an Impact
Data breaches have become more common, accompanied by unsatisfactory corporate reactions. Organizations should have a response protocol founded on transparency, accountability, and humility. Business leaders can protect their reputations and regain consumer confidence by openly addressing the issue.
The Pokémon Detection Center will log around 17,000 malware notifications during a regular week. This statistic amounts to 100 indicators a day for the company’s 24/7 SecOps personnel. And that is just a notification of malware. These alerts might cause security teams to spend over 211,000 hours a month looking for and tracking false positives immediately.
It’ll require 2,625 regular work shifts eight days a week to distinguish between disagreeable and excellent warnings.
Questions from this data emerge including:
- What do organizations learn from these attacks?
- Do they have the resources, time, and executive sponsorship to adjust their incident response and post-attack strategies?
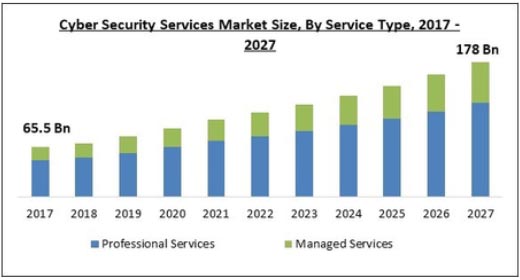
Managed security service providers (MSSP) bring the experience and resources to help augment an organization’s SecOps and SIRT teams. Maintaining cybersecurity incident response with internal resources continues to be a challenge for organizations. Partnering with an MSSP brings tailored solutions, including best-in-class playbooks, digital forensic specialists, analysts, and more, to help manage incident response and digital investigative responsibilities.
To Learn More About How to Secure Your Organization, Please Call Us – as Always; We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/







