Analyzing Security Incidents for a Better Future Response
We wrote about Incident Response in blog post titled “Incident Response Technology has become Critical to Limiting Damage.” We discussed the dramatic increase in the number of attacks including the fact that IC3 or Internet Crime Complaint Center received close to 850,000 complaints related to internet cybercrime in 2021, up roughly 50,000 from 2020 (when estimated losses topped $4.2 billion) and nearly double compared to 2019 (when estimated losses reached $3.5 billion). We discussed SOAR and response automation as part of a solution to minimize damage.
In another Incident Response blog post titled “Incident Response Planning Best Practices,” we discussed the fundamental steps organizations needed to take to build and equip a team to handle cyber attacks and minimize their damage.
In this blog post we are going to look at Incident Response from a broad perspective to clearly define what it is, why it is so critical in the wake of the massive number of attacks last year, and what organizations can learn in attack and incident post-mortems and digital forensic investigations.
Defining Incident Response’s Critical Role in Cybersecurity
Incident response is a term used in our cybersecurity industry to describe the process by which a company responds to a data breach or cyberattack. This includes the steps or procedures the organization attempts to manage the damage or consequences of the attack or incident.
Quality incident response capabilities will effectively manage the incident so that the damage is limited, recovery time and cost are minimized and collateral damage such as brand reputation are preserved.
Cybersecurity incidents are not just tech-related issues but also business-related, so it is essential to mitigate them quickly to limit the damage caused. In this blog post we want to share with you how organizations learn from their past incident response while making critical adjustments to their incident response capabilities to be better prepared
Further, this post will discuss the various stages of the incident response and try to discuss best-in-class IR capabilities that organizations are leveraging to develop procedures and tactics to handling future cyber-attacks.
What is Incident Response?
Incident response (IR) is the process behind an organization’s strategy for a cybersecurity attack, including enabling adaptive controls to stop the attack’s propagation and to activate the external and internal communications plan to notify the executive leadership, legal, customers, and the public if required. The IR tactics should contain details of various steps to declare the beginning and the ending of the cyber-attack and the procedures to hand off the post-activity activities.
Having an incident response plan allows companies to exhibit that they responded promptly and appropriately when faced with a security attack, proving thorough documented records when questioned by stakeholders, including investors, customers, auditors, judges, and media representatives.
How Important is an Incident Response Plan in Containing a Cyber Attack?
In 2022, Los Angeles Unified School announced in the press the school district fell victim to a massive Ransomware attack. This recent attack’s silver lining came about by mobilizing local, state, and federal law enforcement resources as part of the IR plan. The FBI, Department of Homeland Security, Los Angeles County District Attorney’s office, and other agencies mobilized to assist the school in capturing vital digital forensics data, using the findings to eliminate the threat and restore the critical systems at the school. .
A critical component of their IR plan included external communications to notify the public of the suspected breach. The plan also had a pre-coordinated process to engage the various law enforcement agencies and a procedure to ensure all necessary artifacts were collected and not tampered with. The school also carried a cybersecurity insurance policy to help cover the cyber-attacks.
The point here is that 89 Colleges and School Districts, 25 Healthcare Organizations Impacted by Ransomware in 2022. The new report found almost twice the number of K-12 schools were impacted by ransomware in 2022 compared to 2021. Broken down, hackers demanded ransoms from 44 universities and colleges, and 45 school districts that operate 1,981 schools. Comparatively, in 2021, 58 districts running 1,043 schools were impacted, as were 26 colleges and universities.
Many of these hospitals and schools had to close their doors due to poor or at least inadequate incident response capabilities.
Post-Incident Activity
The post-incident cyber attack procedures provide valuable insight into the attack sequence allowing the organization to adjust its cyber defenses and response capabilities. The result from the incident response process can strengthen the risk assessment process and future incident handling approaches to order to improve overall security posture.
In a recent article discussing why organizations need to have a well-planned procedure for post-incident activity, American Family Insurance, an underwriting for cybersecurity insurance, recommends, “after a cyber-attack has been suppressed, continuous caution is essential. Multiple offenders might attempt to make another entryway into networks they formerly breached. Even after attempts to eliminate an intruder and mend recognized gaps in their cyber defense, the malefactors have not been deprived of all routes by which they accomplished unapproved access to the system. Stay mindful of analomous traffic, data and even strange activities within your structure.”
Pre-Attack Versus Post-Attack Response
It is necessary to assess what has occurred to realize what works well, where updates might be required, and how to avert similar missteps afterward. Writing a competent postmortem allows organizations to quickly learn from network security and cyber defense strategies to refine systems and processes. A suitably formed, exonerated postmortem makes it possible for SecOps and SIRT teams to learn how to upgrade the organization’s architecture and adjust the future course of action.
Why Is Incident Response Important?
Organizations use an incident response process to respond quickly and efficiently to cyberattacks, which involves identification, prioritization, investigation, mitigation, restoration, and future prevention. Often, organizations become challenged with a need for more awareness and visibility when they suffer a cyberattack. Several compliance and privacy regulations mandated an incident response action plan for both during and post-attack, including PCI, NIST, HIPAA, and the new Law 25 in Quebec, just to name the most significant pieces of legislation targeting exposed customer data.
Organizations with a well-constructed incident response plan can minimize a crisis’s effects on an organization’s operations and assets. These assets include understanding the organization’s cybersecurity capabilities, access to credible threat intelligence, and employing an experienced incident response team.
Cybersecurity Attack Incident Sharing by industry
If organizations choose only to review their past security incidents, they often will have a limited pool of data on which to base their future decisions. Industries, including global banks, internet providers, cloud service providers, and FinTech companies, will often share information about recent cyber-attacks with the competition.
Many of these industries also host consortiums, including the FBI infraguard, Cloud Security Alliance (CSA), and the Global Finance Executive conference are held annually to provide a forum for executives to share their cyber and threat intelligence experience. Banks often suffer similar attacks, including phishing, waterhole attacks, mobile banking, identity theft, and account takeover.
By sharing in a competitive yet collaborative approach, several industries strive to reduce and improve their mean-time-to-detect (MTTD) and mean-time-to-response (MTTR) measurements The industry metrics correlated to eliminating threats and minimizing damage.
What Score Matters the Most for Incident Response?
While leveraging an MTTD and MTTR along with the MITRE ATT&CK framework and Lochhead Kill Chain, data will be readily available to SecOps, DevSecOps, and NetSecOps teams to pull together everything from a root-cause analysis to a time to detect and time to repair/response.
Why are these statistics relevant to an organization?
Attacks will repeat themselves in many cases; phishing attacks will continue to access email, SMS, and voicemail channels if incident response is not handled correctly and fixes put in place. In addition, in terms of the cloud data, identity management often comes under attack, and many public-facing websites and hosted applications will be breached. The primary questions that come from post-attack analysis should be focused on the overall effectiveness of security controls, including:
- Did the adaptive security controls protect our enterprise work as advertised?
- Are the adaptive controls appropriately configured based on vendor standards?
- Did the security orchestration, automation, and response activate and stop the attack propagation?
- Are the adaptive controls updated?
- When was the last time the organization hired a third-party penetration testing firm to validate their security posture?
By compiling these initial scope questions, organizations can better determine their ability to detect, respond, and capture the needed forensics with minimal human interaction.
The Role of Managed Incident Response Services
Most organizations need more internal expertise, financial answers, and executive visibility to press for changes to create better incident response measurements while reducing organizational risk.
During a regular week, the Pokémon Detection Center will log around 17,000 malware notifications. This statistic amounts to 100 indicators a day for the company’s 24/7 SecOps personnel. And that is just a notification of malware. This alert might cause security teams to spend over 211,000 hours a month looking for and tracking false positives immediately.
It’ll require 2,625 regular work shifts eight days a week to distinguish between disagreeable and excellent warnings.
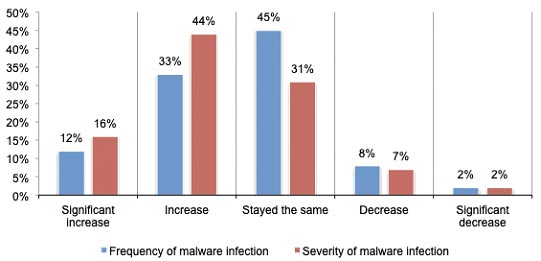
Questions from this data emerge including:
- What do organizations learn from these attacks?
- Do they have the resources, time, and executive sponsorship to adjust their incident response and post-attack strategies?
Managed security service providers (MSSP) bring the experience and resources to help augment an organization’s SecOps and SIRT teams. Maintaining cybersecurity incident response internal resources continues to be a challenge for organizations. Partnering with an MSSP brings tailored solutions including best-in-class playbooks, digital forensic specialists, analysts and more to help manage the incident response and digital investigative responsibilities.
To Learn More About How to Secure Your Organization Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/







