Why Incident Response Technology has become Critical to Limiting Damage
Businesses and organizations operating in today’s connected world face a variety of dangerous new threats from cyber criminals. To keep pace with the Digital Transformation, organizations have to provide convenience for their customers, thus taking payments online, storing customer data and records in information systems, and adopting connected technologies. In doing so, organizations create security gaps and ultimately expose themselves to the threat of cyberattack.
Over 80% of small and midsized organizations reported suffering at least one cyber-attack in the last 12 months, with an average cost of nearly $1 million to restore servers, databases, other systems, and data to return to normal business operation after a successful attack. With such high costs associated with significant attacks, organizations must be prepared to detect and respond to attackers if they are to limit damage and subsequently reduce costs to maintain their business.
Minimize the Dwell Time
Overall, in 2021, the IC3 received 3,729 complaints of ransomware attacks, with adjusted losses in excess of $49.2 million. However, these represent only a fraction of the estimated losses of more than $6.9 billion caused by the reported cybercrime last year.
The IC3 received close to 850,000 complaints related to internet cybercrime in 2021, up roughly 50,000 from 2020 (when estimated losses topped $4.2 billion) and nearly double compared to 2019 (when estimated losses reached $3.5 billion).
Therefore, with the volume of attacks as well as the sophistication of the malware, it is a near certainty that all businesses will succumb to an advanced attack at some point. However, most organizations are woefully unprepared. Only 38% of organizations surveyed for ISACA’s recent “Global Cybersecurity Status Report” believed they were prepared for a sophisticated cyberattack and according to the Ponemon Institute, only 25% of all IT security personnel polled believe their organizations have the ability to thwart the attack.
The current landscape poses enormous hazards for businesses – attackers are often able to spend months inside an organization’s systems before their activities are detected. During this “dwell time,” attackers are able to escalate privileges, spread throughout networks and systems, and exfiltrate sensitive data like trade secrets or sensitive customer and employee information. The ability to detect and respond to such an attack is critical to limiting the damage that successful attackers cause. Ponemon attributes much of the damage suffered in attacks to the time the malware spent on the network or in corporate systems.
Organizations that stop attacks in under 100 days were far less likely to suffer extensive loss than those that allowed the malware to sit on their systems for over 100 days. A simple deficiency of adequate people, processes, and technologies to respond effectively to attacks allows attackers to spend much longer on an organization’s systems and thus increases the impact and cost of the incident exponentially.
Reinforce Security by Investing in the Right Incident Response Team
Many organizations today do not invest in the right people, processes, and technology to respond appropriately to cyberattacks. In the same way, only a few organizations have dedicated or assigned incident response people (a team or an individual) with sufficient technical skills or have the proper training to enable effective decision-making and take action quickly during an attack. The technical skillset for incident response is unique, blending forensic investigation with a technical understanding of networks, systems, and, most importantly, processes that would protect high-value assets in the organization.
Be Organized with the Right Processes
Hiring and maintaining a dedicated team of responders is both difficult and expensive. In addition, maintaining an effective response capability requires training, practice, and extensive preparation in order for everything to operate correctly during an attack. Employing the right processes is a critical element necessary to respond to an attack. Organizations need to have a proven, best-practice plan in place so that they know what to do, how to do it, and when to do it during an attack.
Invest in Incident Response Technology
Technology plays an increasingly important role in enabling effective response. Responders need to know their data and network topology, know where their Internet connections are and have ready access to the appropriate logs. In addition, an effective response tool enables responders to investigate details about where and when events are happening in order to analyze and understand an attack.
An automated incident response tool generates actionable threat intelligence, performs regular vulnerability scans, and raises alerts about at-risk systems – all of which enable the organization to build a proactive, protective shield against attacks.
This has often been done in the past with human elements monitoring traffic, investigating suspicious activity, drafting procedures when new threats arrive, etc. However, as the name suggests, automated incident response eliminates the human element from the process. It automates repetitive tasks, expedites threat detection and response, and provides ‘round-the-clock defense, allowing your SOC team the time and space to further develop and strengthen your security posture in other ways.
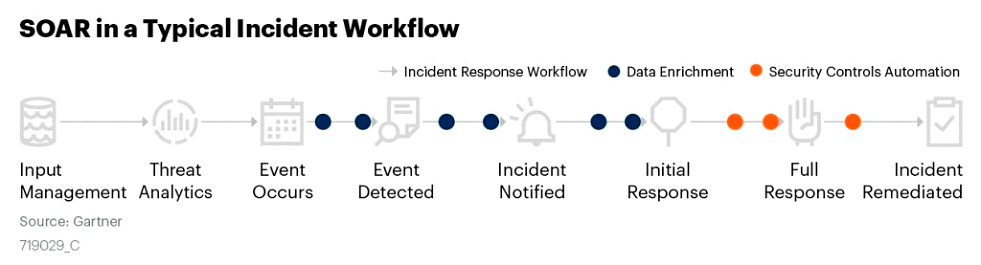
For example, a Security Orchestration, Automation and Response (SOAR) tool provides one of the best ways to automate the incident response process. By leveraging SOAR (defined here by Gartner), security teams can effectively triage alerts, respond quickly to critical cybersecurity events, and deploy an efficient incident response program.
Automation brings advanced proactivity, consistency, and speed to incident detection, response, and mitigation. Instead of manually copying and pasting evidence of a threat, analysts can focus on stopping attacks before they cause irreparable harm. Security operations also become more efficient as they improve mean-time-to-resolution (MTTR).
Prevention, Defense, and Response
The vast majority of organizations do not invest in the right mix of people, processes, and technology necessary to respond to a cyberattack. Too many of them focus on perimeter defense including SIEMs, firewalls, and anti-virus technology rather than response due to the improvement of IR technology of the past several years. The problem with technology focused on preventing malware from entering the network is that most hackers can easily find a way around these innovative technologies through phishing and other social engineering types of attacks that essentially circumvent any defensive technology. With limited budgets, finding the right balance between defensive and responsive capabilities is critical to managing cyber risk effectively. Maintaining response capabilities (including cyber resilience and active cyber defense) is the only way to limit the damage caused when an attacker succeeds. To do so, organizations can start by improving training, planning, and technical capabilities.
Steps to Improve Your Response Capabilities
Thus, fundamentally, how can organizations improve their response capabilities? Several simple steps can make a big difference. Most cyber incidents occur because of phishing or drive-bys and can be traced to employees doing something that they aren’t supposed to do, such as opening a malicious e-mail attachment from unknown senders.
Social Engineering and Training
As the first line of defense, social engineering and fundamental IT security training can not only help prevent a majority of incidents but also aid response capability. Employees trained to report suspicious activity can alert responders to an attack in-progress, activating response procedures and reducing the dwell time of the attacker on the organization’s systems.
Tabletop Exercise
Another effective training element is an incident response exercise or “tabletop” exercise. A simulated attack can be used to test and rehearse an organization’s response procedures, involving not only incident responders and security personnel, but also IT and business organization participants to document and simulate communications and “swim lanes” between departments.
Create an Incident Response Plan
Another way to immediately improve response capability is to create an incident response (IR) plan. An IR plan is geared to document and outline the actions and procedures necessary to take once an attack is detected. Organizations are well-served to have a plan prepared and approved by executive management in advance, as they do not need to determine who to contact, what to do, and what actions are authorized when under attack. Having agreed-upon actions makes response times faster and eliminates uncertainty concerning responsibility and next steps.
Notably, in Ponemon’s survey of 2,400 security and IT professionals, 75% of the respondents said they did not have a formal Cyber Security Incident Response Plan (CSIRP) that could be applied consistently across their organization. What about your organization?
Writing and then communicating and drilling on such a plan is an effective first step toward building a strong incident response program.
Conclusion
With attacks occurring constantly and new attack techniques and advanced malware being generated daily, it is more important than ever for organizations to be prepared to respond to cyberattacks. With the right investments in people, processes, and technology, organizations can effectively respond to intrusions and minimize the financial losses that come with an attack.
Collecting information like logs that security teams need is time-consuming; analysts must go into each system to review its events to try to understand how the breach took place and what was compromised which greatly reduces response efficiency. Having an automated incident response solution with log management capabilities allows you to search for relevant alarms rather than combing through hundreds, if not thousands of logs manually. Increasing time efficiency and streamlining mundane tasks helps SOC teams meet other KPIs such as reducing mean time to detect (MTTD) and mean time to respond (MTTR).







