The 5 Elements to Effectively Managing HIPAA Compliance
Managing Patient Data (PHI) Sprawl
In 1996, the Health Insurance Portability and Accountability Act (HIPAA) created an electronic data interchange that health-care providers and other related organizations are required to use for electronic transactions. The HIPAA Privacy regulations require health care organizations and their business associates (BAA) including cloud providers like AWS and Azure to create and follow procedures that ensure the confidentiality and security of protected health information (PHI). The law further mandates that PHI must be protected even when it is transferred, received, handled, or shared. Finally, the legislation applies to all forms of PHI, including paper, oral, and electronic, etc. HIPAA applies to any organization that holds Protected Health Information (PHI) on any citizen in the USA.
Over the past decade, mobility and IoT devices used in healthcare have increased the depth of data and insights available to improve the quality of care, patient outcomes, and patient experience. However, with all the positives that have come from the increase in patient information and the accessibility to that data, healthcare providers are required to manage and govern the complexity and sprawl of the data, but most importantly, protect that data.
Healthcare organizations have the unenviable task of balancing the protection of massive amounts of personal and medical data with the requirement for quick access and easy movement by the care providers, insurers, and partners.
Eliminating the Fines are Costing Healthcare Organizations Out of Compliance in OCR Audits
The federal fines for HIPAA noncompliance are based on the level of perceived negligence found in an organization at the time of the HIPAA violation. These fines and consequences can range from $100 to $50,000 per violation or patient record, with a maximum penalty of $1.5 million per year for each violation.
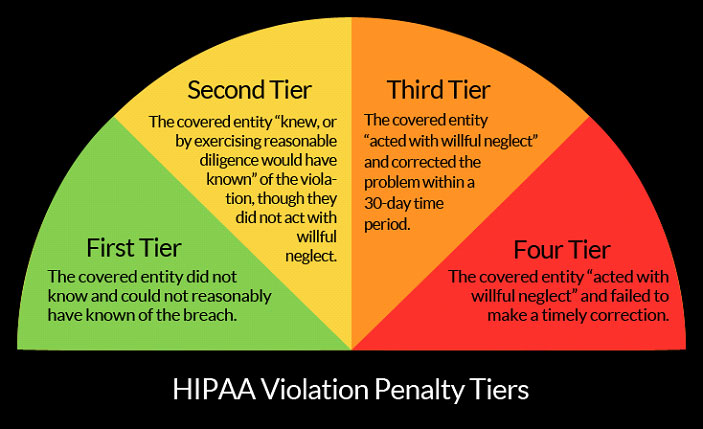
For healthcare providers, managing HIPAA compliance requires protection of sensitive data not only “at rest” in databases, systems, or devices, but also as we suggested earlier when it is being transmitted between providers. HIPAA lists 18 identifiers that are considered personally identifiable information, high-value data targets including social security numbers, medical IDs, and financial information.

HIPAA established important national standards for the privacy and security of protected health information and the Health Information Technology for Economic and Clinical Health Act (HITECH) established breach notification requirements to provide greater transparency for individuals whose information may be at risk. HITECH requires the HHS Office for Civil Rights (OCR) to conduct periodic audits of the covered entity and business associate compliance with the HIPAA Privacy, Security, and Breach Notification Rules.
The audit program is an important part of OCR’s overall health information privacy, security, and breach notification compliance activities. The audits present an opportunity to examine mechanisms for compliance, identify best practices, discover risks and vulnerabilities before they result in breaches. These audits strike terror in healthcare organizations as fines for non-compliance increase and the public’s increased scrutiny of providers who are deemed poor at protect their data suffer brand damage.
GDPR, CCPA, and other Privacy Legislation are Complicating Data Management
The implementation of GDPR, CCPA, and other privacy regulations reflect a major change in attitude toward personal privacy. This new public consciousness, that one’s personal information must be rigorously protected by organizations that collect it, is increasing the focus concerning how organizations view privacy compliance. In a commercial environment where the customer is empowered to assert their rights over their personal information, companies that are most attentive and responsive to those rights will stand out as privacy champions.
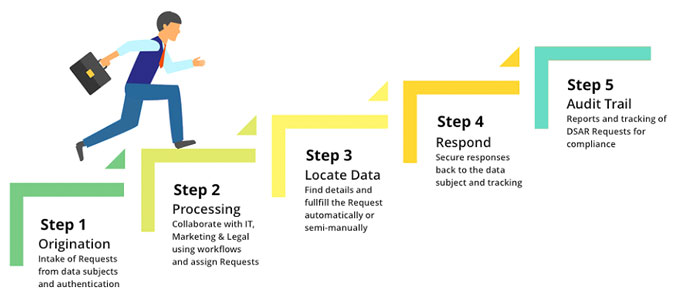
Emerging compliance legislation like GDPR and CCPA allows consumers to request access or even demand the deletion of their data. Each request from a consumer can translate into large numbers of often complex tasks that you must perform inside your company.
SSR’s or DSR’s are formal requests for information that empower customers through GDPR and CCPA to ask companies for a record of their personal information. Organizations without the infrastructure or technologies to respond in an automated fashion will spend countless hours tracking down a patient’s PHI across systems, devices, e-mail records, and more.
#4 – Cloud Providers and other BAA’s Must Comply with HIPAA
Under the 2015 HIPAA Omnibus rules, business associates are directly responsible for HIPAA compliance. This means that while most business associates or vendors have done business with healthcare providers since HIPAA’s passage, they now must meet a number of provisions of HIPAA. Business Associates, who are not in compliance, are subject to fines that can range up to $1.5 million per HIPAA compliance violation.
Business associates are individuals that work with a covered entity in a non-healthcare capacity and are just as responsible for maintaining HIPAA compliance as covered entities. Business associates are the lawyers, accountants, administrators, and IT personnel that work in the healthcare industry and have access to PHI.
Critically, the definition of “business associate” also applies to your cloud service provider. That means that, in working with Azure, you will need to enter into an agreement with Microsoft to ensure compliance with HIPAA.
#5 – Data Security is Paramount to Patient Trust and Brand Equity
As we suggested, healthcare organizations are rich repositories of sensitive information, such as credit card data, email addresses, Social Security Numbers, employment information, and medical history records. This makes them high-value and vulnerable targets for cybercriminals. IDC’s Health Insights group predicts that 1 in 3 healthcare recipients will be the victim of a medical data breach next year. In the last two years, 89 percent of healthcare organizations have reported at least one data breach, with 79 percent reporting two or more breaches according to IDC.
According to HIPAA Journal, between 2009 and 2019 there have been 3,054 healthcare data breaches involving more than 500 records. Those breaches have resulted in the loss, theft, exposure, or impermissible disclosure of 230,954,151 healthcare records.
According to Cybersecurity Industry-Leading Research Reports including the Ponemon Institute and Verizon Data Breach Investigations Report, the health industry experiences more data breaches than any other sector.
Breaches are widely observed in the healthcare sector and can be caused by many different types of incidents, including credential-stealing malware, an insider who either purposefully or accidentally discloses patient data, or lost laptops or other devices. PHI is more valuable on the black market than credit card credentials or regular Personally Identifiable Information PII.
Conclusion – Where Do I Start?
- Risk Assessment – Review your workplace and electronic devices to assess the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic Protected Health Information. The assessment will include a listing of all computing and mobile devices, where paper files are stored, and how you will secure your data as a foundation. This is not a one-time event and will change over time as technology and risks change. You will want to revisit your Risk Assessment anytime you have a breach, theft, or significant changes in your IT environment.
- Privacy and Security Policies and Procedures – Upon completion of your Risk Assessment, you should create a plan for achieving HIPAA Compliance. The plan should include your basic Policies and Procedures – ensuring the Privacy of Protected Health Information and the Security of such information. Policies and Procedures need to be updated regularly and any changes need to be clearly documented and communicated to your staff.
- Adoption of potential breach protocols – A protocol for investigating potential breaches of protected health information is essential. The Risk of Harm Standard and the risk assessment test can be used to determine if a breach has occurred. If a breach has occurred, it is essential that the healthcare organization document the results of the investigation and notify the appropriate authorities.
To Learn More About How to Become Compliant with HIPAA or Conduct a Risk Assessment Call Us – as Always We Are Happy to Help – 1 (888) 982-0678







