5 Cybersecurity Trends that will Impact the Industry in 2023
Let’s start this blog post with a look at the evolution and impact of cybercrime over the last year.
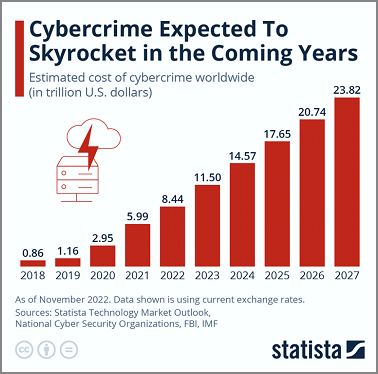
According to estimates from Statista’s Cybersecurity Outlook, the global cost of cybercrime is expected to increase over the next five years, rising from $8.44 trillion in 2022 to $23.84 trillion by 2027. We all know that the impact of a successful cybersecurity attack – damage to brand reputation, customer trust, and profitability – can take years to recover from.
It’s not surprising that the fightback against cybercrime is gathering momentum and attracting board-level interest. The latest figures from Gartner indicate that security and risk management will rise to the top of the list of technology priorities for medium-sized enterprises in 2023.
In a recent Wall Street Journal article titled, “Corporate Tech Leaders Untangle Their Cybersecurity Roles,” they suggested, “across organizations worldwide, CIOs and CISOs are redefining their relationships. “It is cybersecurity. …that is the highest priority,” Chris Howard, chief of research at technology research and consulting firm Gartner Inc., told The Wall Street Journal earlier this year.
If cybercrime were measured as a country, it would be the world’s third-largest economy after the U.S. and China
In this blog post, we’ll review some of the most impactful cybersecurity trends that are emerging and need to be considered by IT security teams as they adjust their people, processes, and technology to defend their organizations against the growing number of attacks they will be facing in 2023.
Trend #1 – Ransomware and Business Email Compromise (BEC) Account for 70% of Breaches
Ransomware and business email compromises (BEC) were far and away the the leading attack vector and type of attack on organizations in the past year, making up 70% of the total number, according to the 2022 Unit 42 Incident Response Report, a cybersecurity consultancy. The firm compiled its report findings based on approximately 600 incident responses between May 2021 and April 2022.
While these two attack types are the primary ways threat actors can monetize illicit access to networks, attackers have and use nearly countless other strategies for financial gain or simply to harm the organization. Cybercriminals have increasingly paired extortion with encryption (sometimes including added threats of informing customers or the press or conducting a distributed denial-of-service attack). As Ransomware-as-a-Service (RaaS) continues to emerge and even script kiddies (laymen or non-technical folks) can buy malware on the dark web to make a few dollars, the number of attacks is likely to increase.
A summary of Unit 42’s Incident Response Findings
- The seven most targeted industries accounted for over 60% of the cases; they included finance, professional and legal services, manufacturing, healthcare, high-tech, wholesale and retail.
- 50% of the compromised organizations lacked multifactor authentication (MFA) on key internet-facing systems such as corporate webmail, virtual private network (VPN), and other remote access solutions.
- 77% of intrusions are suspected to be caused by three initial access vectors – phishing, exploitation of known software vulnerabilities, and brute-force credential attacks focused primarily on remote desktop protocol.
- The report also found that more than 87% of positively identified vulnerabilities fell into one of six major categories – the ProxyShell and ProxyLogon flaws in Exchange Server, the Apache Log4j vulnerability, and vulnerabilities in Zoho ManageEngine ADSelfService Plus, Fortinet, and SonicWall.
Ransomware-as-a-Service is on the Rise (RaaS)
RaaS, which was developed by organized crime has exploded as a business in 2022. It follows the SaaS business model as developers often sell RaaS “kits” that include tech support, bundled products and complementary technologies. These criminal organizations often provide user reviews and forums, and other benefits. Payment for services is typically paid in cryptocurrency in order to avoid detection by law enforcement.
The model allows anyone, even those with little or no programming experience, to pay for and use already-developed malware. With a litany of RaaS options having made their way into the marketplace, all that is required from a would-be perpetrator is malicious intent and access to the dark web.
Trend 2 – Cybersecurity Professionals are in High Demand
Cybersecurity experts have been in high demand for years; however, the war for this security talent will increase into 2023 and beyond. The global cybersecurity workforce grew to over 4.7 million people, reaching its highest-ever levels.
However, currently, there is still a need for more than 3.4 million security professionals, an increase of over 26% from 2021’s numbers. Working in-house as a cybersecurity professional isn’t easy. Analysts are expected to be available 24/7 when organizations experience major incidents. A recent study by Tines found that 66% of security team members experience high levels of work stress, and 64% have had work stress affect their mental health.
Interestingly, it appears that more cybersecurity employees are experiencing overwork and burnout due to these teams being chronically understaffed. This isn’t a new issue in cybersecrutiy; over the past several years, there have been reports of over work causing the hospitalization and even deaths of tech employees in Australia and China.
What Can IT Security Teams do to Alleviate Some of the Security Burden?
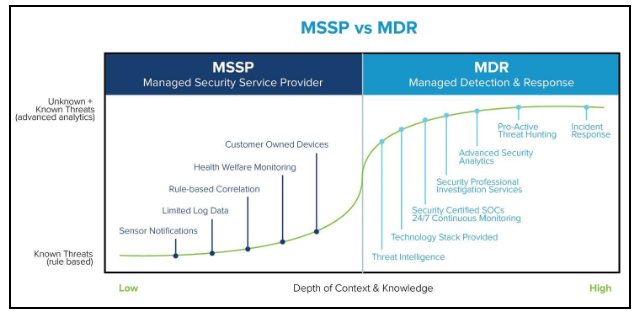
Ease the Burden on Internal IT Teams with Partners: Outsourcing is a sensible strategy for organizations struggling to attract scarce cybersecurity talent and wanting to avoid overworking their internal teams. Small and medium-sized businesses are increasingly gravitating towards these arrangements: A recent survey revealed that 90% of small security teams are outsourcing security mitigation to a Managed Detection and Response (MDR) service while also using Managed Security Service Provider (MSSP) services (21%) and Virtual Chief Information Officer (vCISO) services (15%).
Security Employees are in High Demand: Despite a what some are saying is a recessionary climate (yes, even this is subjective,) cybersecurity professionals have quite a bit of liberty concerning where they work, and increasingly, they’re coming forward to demand accountability for unfair and unethical work practices.
The SEC stated this year that it has issued “whistleblower rewards” of over $1.3 billion in total to 278 individuals over the last decade. All this means that leadership teams need to place ethics and trust high on the boardroom agenda.
Trend #3 – Managed Detection & Response (MDR) is Improving Cyber-Defense
Let’s start with a brief definition of MDR; Managed detection and response (MDR) is a cybersecurity service that joins technology and human expertise to perform threat hunting, monitoring, and response. One of the primary benefits of MDR is to reduce the time to detection of a breach considerably. MDR will quickly identify and limit the damage of threats without the need for additional headcount.
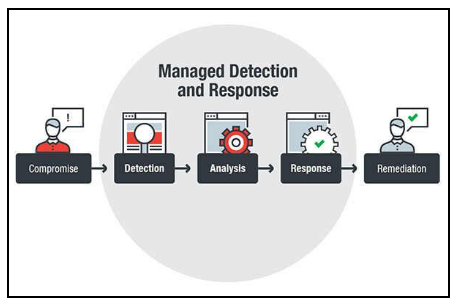
MDR is intended to detect intrusions, malware, and malicious activity in your network and assists in rapid response to eliminate and mitigate those threats. Quality MDR services have a very light footprint on your network and use a combination of human analysts and technology to eliminate false positives, identify real security threats, and develop incident response actions in real time.
MDR is a suite of services that provide insight into network traffic, allowing organizations to identify, monitor, respond to, and limit the impact of malicious threats on their network. Organizations can add MDR services without having to expand their IT security team.
MDR solutions provide relevant threat intelligence, advanced analytics, and forensic data which are provided to security analysts, who perform an investigation on alerts. The MDR data and insights that are provided the analysts allow them to determine the appropriate response to reduce the impact and risk of potential security incidents.
While the average time across industries to detect a compromised asset is close to 198 days, MDR typically reduces that to hours, and therefore minimizes the impact of a security event. Some MDR providers also offer remediation solutions, to manage all aspects of incident response when a security incident occurs.
Trend #4 – The Metaverse is Web 3.0 and it has Serious Privacy Implications
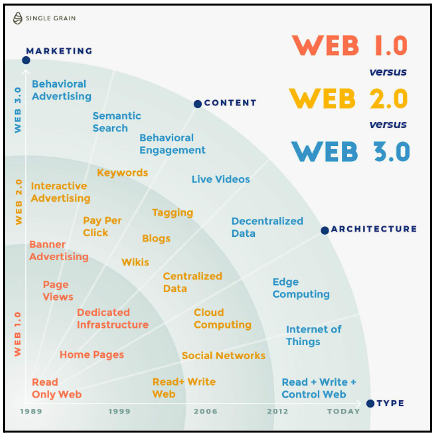
Web 2.0 and Web 3.0 refer to the past two iterations of the internet; Web 1.0 which was introduced in the mid-to-late 1990s and early 2000s and only allowed users to consume information unlike Web 2.0 which is a far more interactive iteration of the Web. Our current version of the Web is Web 2.0 which supports social connectivity, user-generated content and allows users to interact with websites. Further, web 2.0 makes it possible for user-generated content to be viewed by millions of people around the world virtually in real-time.
Web 3.0 or Web3 is the third generation of the World Wide Web. Currently a work in progress, it is a vision of a decentralized and open Web with greater utility for its users.
To get us started on our discussion of Web 3.0 in this post, here is a high level description of the three iterations of the Internet:
- Web 1.0 is read-only – users can only read and consume information on websites.
- Web 2.0 is read-write – user can not only read, but also write and add content to websites and applications.
- Web 3.0 is read-write-interact – users will be able to leverage artificial intelligence to read, write, and interact with content on websites and apps.
Web 3.0 is built on the basic concepts of decentralization, openness, and greater user utility. Users will have the ability to retain control over their data and content, and they can sell or trade their data without losing ownership or risking privacy as they do with Web 2.0 when they provide their personal information to organizations to do business.
In this business model, users can log into a website without having their internet identity tracked. Our current web 2.0 systems and content processes will be replaced because of improved searchability, interconnected data which will deliver a faster and more personalized user experience. It is built using artificial intelligence (AI), machine learning (ML), and the semantic web, and uses the blockchain security system to better safeguard user’s personal information.
The term ‘metaverse,’ which has been leveraged by Facebook to describe a tightly interconnected set of digital spaces that lets users escape into a virtual world and the rules of technology are the only limit. Facebook’s vision is that Web 3.0 will empower users to be right in the moment with friends, family and colleagues, in a world free from the constraints of the physical world.
Plainly, metaverse combines the worlds of ‘meta’ and ‘universe.’ This evolution of the internet will mark the rise of online 3D or virtually integrated environments that provide users access to virtual reality and augmented reality experiences.
Web 3.0 decentralizes the internet and the metaverse is a fully immersive successor to the internet. It’s a combination of virtual reality (VR), augmented reality (AR), mixed reality (MR), gaming, cryptocurrencies, and social media. While this model undoubtedly benefits the user in terms of an overall experience, the lack of central data access expands the attack surface of organizations significantly and will likely make cyber-attacks more difficult to uncover and stop.
There are two main forms of the metaverse:
- Virtual Reality provides an artificial reality through a virtual reality device, which will provide an immersive experience.
- Augmented reality while less immersive than virtual reality adds virtual overlays on top of the real world via a lens of some type. Users still have a normal view of their surroundings. For example, IKEA has an app that allows users design their living space and furniture to get the feel of the finished product before it is done. Frankly, at this point, some of the best augmented reality examples are in home remodeling or trying home products and furniture virtually before buying. Users can actually see what their homes would look like through their phone or desktop device prior to making a purchase
It is important to note that, in virtual reality experiences there should be no current expectation of privacy rights. In augmented reality environments, where the user experience is limited to a monitor or screen privacy rights to data should be expected.
User data in the metaverse includes sensor, location, physiological and social data. It is important that users and security understand the PII data is being collected by the platform provider. There are several other security concerns with the Metaverse as legislation like CCPA, GRDP and Law 25 have not been introduced to protect personal data in virtual reality worlds. Virtual reality and augmented reality headsets are machines with a quite a bit of software and memory. Thus, they will likely be high value targets for malicious hacks.
In addition, the lack of centralized data will be problematic when it comes to online harassment, hate speech, and inappropriate or criminal images. In a decentralized web, who will enforce worldwide hosted content? That is one of the critical questions that is being asked as Web 3.0 is now emerging.
Trend #5 – Extended Detection and Response (XDR) is Changing SecOps
XDR emerged as a market category in response to the complexity of collecting, aggregating, analyzing, and investigating the thousands of alerts thrown off by dozens of security technologies. According to analyst firm Gartner, Extended Detection and Response (XDR) is “a SaaS-based, vendor-specific, security threat detection and incident response tool that natively integrates multiple security products into a cohesive security operations system that unifies all licensed components.” We understand that is a fairly broad and nebulous description of XDR so we’ll take a shot at breaking down exactly what XDR means.
The basic premise of the solution is simple: XDR is a category of threat detection, investigation, and response solutions. Further, it is a logical evolution of endpoint detection and response (EDR) solutions into a primary incident response tool or solution. As we all know, an organization’s IT infrastructure likely now includes the network, endpoint, and cloud, among other parts of the environment. By increasing integration of security tools, XDR tools increase visibility and insight for both the machine-learning models powering them and the security analysts using them.
As we all likely know too well, detection and prevention technologies like SIEMs, EDR, IDS generate hundreds or thousands of alerts per day, far exceeding the amount security teams are staffed to handle. Alerts come from many disconnected sources, leaving analysts to try and piece the puzzle together of an event or incident. Analysis of a potential threat generally requires a number of steps:
- Review available log data to find any potential malicious or suspicious connections, traffic and dozens of other types of user activity.
- Manually compare against log data to threat intelligence to find out if any activity in the log data is consistent with indicators of compromise in their threat intel data.
- Find anomalous activity that may point to an exfiltration of data, suspicious user behavior, or connections with a command-and-control system that may be suspicious. .
- Evaluate whether the alert needs to be escalated to a higher priority in the SOC or discarded, or perhaps remediated.
These activities have traditionally taken quite a bit of time for analysts to put the pieces of an incident together. The reality is that analysts typically only have time to address the highest priority alerts that they received on a daily basis. This means that often a significant number of lower priority alerts aren’t analyzed but should be.
In addition, security analysts who are responsible for alert investigation often have little or no context as to what the alert means and how to categorize it in terms of importance. Thus, often the alert is escalated to a higher-level analyst for further investigation, requiring additional time, labor, and resources.
What most organizations need is a set of technologies to reduce the total number of alerts while allowing a tier 1 analyst to assess threats more efficiently without having to escalate the threat to a tier 2 or 3 analyst. Thus, with more visibility and context, events that would have been pushed aside as a low priority threat can now be investigated, allowing security teams to eliminate any an attack, or at a minimum, mitigate the threat more quickly, therefore reducing damage.
Conclusion
We could have chosen from a dozen different trends that are impacting the Cybersecurity industry. However, the 5 we chose will undoubtedly be top of mind for almost every head of security in the coming year. In the coming blog posts, we will continue to monitor and address changes and our perspectives of the the top 5 trends we chose for this post.
Trend #1 – Ransomware and Business Email Compromise (BEC) Account for 70% of Breaches
Trend #2 – Cybersecurity Professionals are in High Demand
Trend #3 – Managed Detection & Response (MDR) is Improving Cyber-Defense
Trend #4 – The Metaverse is Web 3.0 and it has Serious Privacy Implications
Trend #5 – Extended Detection and Response (XDR) is Changing SecOps
In the meantime, we hope you enjoyed the post and will look for our next blog post.
To Learn More About How to Defend Against Malware Attacks or If You Have Been Attacked Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/







