Taking a Risk-Based Approach to Patch Management
Designing and Implementing a Risk-Based Patch Management Program
In this blog post, we wanted to take an additional step into explaining the benefits of quality vulnerability management, vulnerability assessments and patch management. We have discussed the topic at your request in previous blog posts including:
- What You Need to Know About Vulnerability Assessments – https://secureops.com/effective-vulnerability-assessments/
- The Difference Between a Penetration Test and Vulnerability Assessment Part 1 of 2 – https://secureops.com/va-vs-pt/
- The Difference Between a Penetration Test and Vulnerability Assessment Part 2 of 2 – https://secureops.com/va-vs-pt2/
- Vulnerability Management – A Best Practice – https://secureops.com/effective-vulnerability-management/
Those four posts should provide a good foundation for understanding the need for vulnerability assessments and a vulnerability management program and will help answer the most frequently asked question in the history of IT Security – What is the difference between a vulnerability assessment and a penetration test. Ok, let’s get started with understanding risk-based patch management.
Every organization has software that contains exploitable vulnerabilities. The sheer number of vulnerabilities that are discovered and ranked each year by the CVE has been over 22,000 in each of the last two years. The volume of vulnerabilities has become overwhelming and the fact that most software has multiple vulnerabilities practically guarantees that most organizations will struggle with prioritizing, testing, and applying patches.
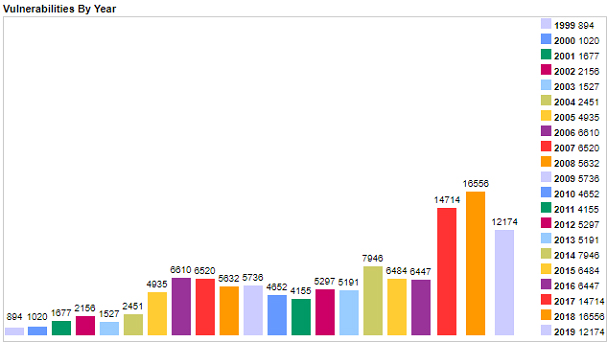
Figure 1 – Vulnerabilities by Year – CVE Website – https://www.cvedetails.com/browse-by-date.php
While not every organization is affected by every vulnerability; every company likely is likely impacted by hundreds of new vulnerabilities per year. In many cases, the updates associated with these vulnerabilities need to be collected, tested, applied and verified to provide complete protection.
This creates a significant workload for organizations’ security teams, which are often already overwhelmed by their responsibility to protect the organization against an increasing number of incidents and threats. As a result, it should come as no surprise that many organizations are behind on updates and that their backlogs of patches are steadily growing.
Prioritizing Patch Management Using Risk Assessments
For most organizations, patching every vulnerability is not feasible, and, in the few cases where it may be, it likely is not financially viable. Companies need to take an intelligent approach to identify and apply the updates that are most important to their organization’s security posture.
This is why performing risk assessments are vital to the vulnerability and patch management process. Like anything else that the security team does, the software updates that they apply should be organized based upon their positive impact on the organization’s cybersecurity posture.
Four important considerations are:
- The criticality of the affected system
- The exploitability of the vulnerability
- The potential impact of exploitation
- Are there viable alternatives to patching
System Criticality
An important first question to ask when triaging potential updates is “which system(s) do they affect?” Not every system in an organization’s network is equally important, and their relative importance impacts the relative importance of the patches that they require.
For example, systems that database an organization’s customer data, serve up web applications that take in customer form fills, or handle critical production tasks should be prioritized. Some vulnerabilities like the infamous Apache Struts 2 flaw that allows hackers into Equifax systems is critical to patch immediately, however, despite the numerous critical vulnerabilities associated with Apache’s open-source code many organizations like Equifax waited months to apply critical patches. We will talk about the Equifax example in the next section a bit further.
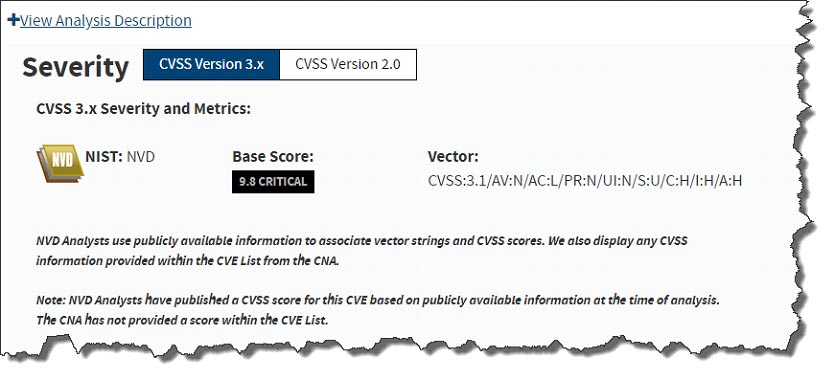
Figure 2 – Example of an Apache Struts Vulnerability with a 9.8 Score – https://nvd.nist.gov/vuln/detail/CVE-2019-0230
It is important to consider both the number and importance of the systems affected by a vulnerability. While a vulnerability that impacts the organization’s customer database is of vital importance, one that could allow ransomware to be installed on all employee workstations (systems of relatively low importance) can be equally devastating to a business.
Vulnerability Exploitability
While a number of different vulnerabilities are discovered each year, not all of them are actively weaponized and exploited by cybercriminals. In fact, only 37.3% (we say only but this is thousands of vulnerabilities) of vulnerabilities have to exploit code or a proof of concept created for them, and only a fraction of these are actually used by cybercriminals within their attacks.
Whether or not a vulnerability has been weaponized and is actively exploited should be a major factor in determining the speed at which an organization patches a vulnerability. Several major cyberattack campaigns, including those like the WannaCry ransomware outbreak and the Equifax data breach, exploited vulnerabilities that had patches available and were officially announced as being actively exploited by cybercriminals.
Impact of Exploitation
Not all vulnerabilities are created equal. This is why vulnerabilities are often ranked based upon the Common Vulnerability Scoring System (CVSS), which provides both a numerical rating of severity and a label of low, medium, high, or critical.
This severity value or CVE score should be combined with the previous two factors to determine the risk that a particular vulnerability poses to an organization. This enables vulnerabilities to be ranked and triaged so that vulnerabilities that are most likely to cause significant damage to a critical system are handled as quickly as possible.
Two common uses of CVSS (Common Vulnerability Scoring System) are calculating the severity of vulnerabilities discovered on one’s systems and as a factor in prioritization of vulnerability remediation activities. The National Vulnerability Database (NVD) provides CVSS scores for almost all known vulnerabilities allowing organizations to assess the seriousness of each vulnerability.
Alternatives to Patching
The previous three factors discuss how to prioritize the patches to be applied to a system. However, the sheer number of vulnerabilities that are discovered each year and that impact an organization’s systems means that it is unlikely that an organization will be able to fix all of the vulnerabilities on the list.
For this reason, it is important to also consider whether or not, for some systems, an alternative to patching may exist. For example, web application firewalls (WAF) and runtime application self-protection (RASP) solutions often offer virtual patching. This involves identifying and blocking attempts to exploit a vulnerable system, which, ideally, has the same impact as patching the system itself because an exploit never reaches a vulnerable component.
The use of virtual patching can help an organization to scale its patch management program by providing a quick, low-cost option to manage certain vulnerabilities, enabling an organization to focus on patching other systems that lack the same level of protection. However, virtual patching is not always perfect and should largely be used as a temporary fix with actual patches and updates to be applied when possible.
Verifying Patch Application with Vulnerability Scanning
Identifying and applying patches for a particular vulnerability is only part of the vulnerability management process; it is also essential to ensure that the patch was applied properly, eliminated the vulnerability in question, did not create any new security issues and the software and system do not have new bugs as a result of the patch.
This step of the process is critical to ensuring that an organization does not become a cautionary tale in cybersecurity. For example, the Equifax data breach is one of the largest and most famous breaches in history. The organization was widely criticized for failing to apply a patch for Apache Struts that was known to be actively exploited before the attack occurred.
But what if Equifax did apply that patch but it did not work? An interview with Equifax’s CIO during the breach revealed that the organization believed that the vulnerability was patched. A scan by a possibly misconfigured vulnerability scanner supported this conclusion, however, obviously, the vulnerability was not properly patched and was exploited by cybercriminals.
This underscores the importance of performing vulnerability scanning to verify that patches are applied correctly using a variety of internal, external, authenticated, and unauthenticated scans. This helps to ensure that a vulnerability is actually closed and not just hidden from view.
Building a Scalable and Effective Vulnerability Management Program
An effective vulnerability management program is not easy to build and maintain. The large and growing number of vulnerabilities discovered each year forces security teams into a desperate scramble not to fall behind.
In many cases, attempting to patch every vulnerability is an impossible goal. Instead, it is vital to take steps to ensure that the most important vulnerabilities are patched as quickly as possible and to look for alternatives to patching to help scale an organization’s vulnerability management program.
Conclusion
Risk-based patch management is part of an overall vulnerability management program and is an IT security strategy in which organizations prioritize the patching or remediation of software vulnerabilities according to the risk they pose to the organization.
To provide a recap; a risk-based patch management strategy has several components:
- They assess the importance and the business context of systems; not all systems are created equal and an intrusion into some segments of a network may be more damaging or likely than others.
- They use intelligence from CVE to NIST to generate risk scores based on the likelihood of exploitation by attackers.
- They use threat intelligence to identify the vulnerabilities attackers are discussing, experimenting with, or using. Meaning have attackers created malicious code or an exploit to take advantage of the vulnerability.
- By combining asset criticality and intelligence risk-based patch management programs focus patching efforts on the vulnerabilities that are most likely to be exploited and that reside on the most critical systems.
To Learn More About Vulnerability Assessments and Management or If You Have a Security Question Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/








