Extended Detection and Response (XDR) is Changing SecOps
XDR emerged as a market category in response to the complexity of collecting, aggregating, analyzing, and investigating the thousands of alerts thrown off by dozens of security technologies. The basic premise or the solution is a simple one: XDR is a category of threat detection, investigation, and response solutions that work across all threat vectors in a company’s infrastructure, such as network, endpoint, and cloud, rather than just one piece. By increasing the integration of security tools, XDR tools increase visibility and insight for both the machine-learning models powering them and the security analysts using them.
Detection and prevention technologies like SIEMs, EDR, and IDS generate hundreds or thousands of alerts per day–far exceeding the amount security teams are staffed to handle. These alerts come from many disconnected sources, leaving analysts to piece the puzzle together. Analysis of a potential threat generally requires a number of steps:
- Review available log data to start piecing together what may have occurred.
- Manually compare against threat intelligence sources to determine if indicators are known to be malicious.
- Find information gaps and search for available data that may indicate additional steps in the attack.
- Check if new information links to alerts are being handled by other team members to coordinate efforts.
- Evaluate whether the alert needs to be escalated, discarded, or quickly remediated and closed out.
All of these steps traditionally take a lot of time and multiple tools to complete—and that’s just triage. The net result is that analysts only have time to address the highest priority alerts they come across each day; meanwhile, a disconcerting number of lower priority alerts aren’t addressed at all.
Further, security analysts who are responsible for alert triage are often left with insufficient context to determine the real risk an attack presents to the organization. Thus, the alert is escalated to a higher-level team of analysts for further investigation, requiring additional time, labor, and resources.
Many organizations attempt to use APIs to integrate their detection and response data. This generally involves using an expensive SIEM as the centerpiece of their security operations, which aggregates log data by parsing and normalizing it, thus stripping away much of the valuable context. Security teams get to see the log data in one place, but it isn’t pieced together meaningfully, and the frontline analysts charged with making sense of it often can’t use the tools that contain the richer source data.
What’s really needed is a set of technologies to reduce the total number of alerts while at the same time allowing less experienced analysts to assess threats efficiently and confidently on their own, ensuring that only high-fidelity alerts are escalated to more senior analysts. This is the role XDR is trying to fill.
What are the Main Challenges to Stopping Attacks?
The complexity of modern attacks requires the analysis of multiple data sources to identify and confirm malicious activity. Layering on one-dimensional tools adds significant expense for security teams, creates potential blind spots, and requires a lot of manual effort on the part of security analysts to switch between consoles and make sense of an attack. 451 Research has found that 76% of security teams initiate at least a quarter of their attacks through manual threat hunting, indicating that the detection technologies and processes they have in place to surface attacks are not delivering against the objective. Unless you have full visibility and analysis of all the components in your environment, you could be missing threats. ESG Research found that 66% of organizations feel their threat detection and response effectiveness is limited because it is based on multiple independent point tools.
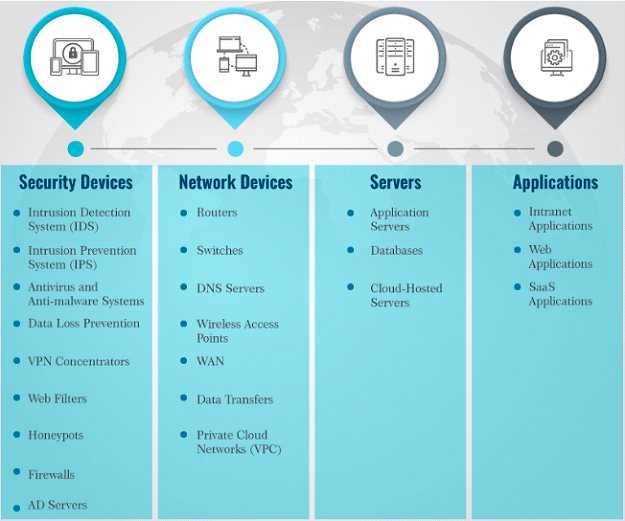
Figure – Alerts are Delivered in the Hundreds or Thousands from Dozens of Devices
Most enterprises receive thousands of alerts from dozens of monitoring solutions overwhelming analysts who often dismiss alerts that should be investigated. Advanced detection is not about more alerts; it’s about better alerts—more actionable alerts. Achieving this requires the integration of not only all of the detection technologies in use, but also better analytics that analyze endpoint, network, and cloud data to find and validate potential attacks.
How Will XDR Technology Help Thwart Attacks?
Let’s start clean here; XDR, or extended detection and response, is a new category that has emerged to meet the need for more comprehensive and sophisticated detection and response. The “X” stands for “extended,” but it really represents any data source, recognizing that it’s not efficient or effective to look at individual components of the infrastructure in isolation. XDR uses machine learning and dynamic analysis techniques to combine capabilities and outcomes associated with SIEM, UEBA, NDR, and EDR.
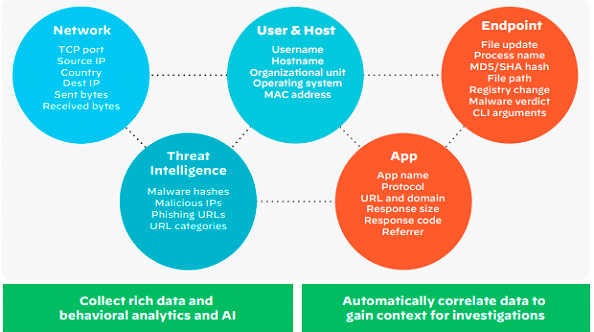
Figure – XDR will Aggregate and Collate Data Across Security Tools for Faster and More Accurate Analysis
The Benefits of XDR for Detection
XDR gives security teams an increased ability to:
- Detect malicious activity from both internal and external resources by finding patterns among activity happening on the network, at endpoints, and within the cloud.
- Utilize cutting-edge analytical techniques on significant amounts of security data to identify abnormal activity without increasing the level of false positives.
- Leverage internal response and external threat intelligence to learn from past attacks and make that experience accessible to less sophisticated analysts, improving the performance of the entire security team.
How is XDR Technology Different than a SIEM or SOAR?
In a recent blog post, Forrester analyst Allie Mellen wrote:
“Until recently there was no reliable, unbiased explanation for what XDR is and how it differs from a security analytics platform, which has led to confusion and disregard from clients who dismiss it as nothing more than yet another cybersecurity marketing buzzword.”
So let’s try and be clear, Extended Detection and Response (XDR) is the next evolution of endpoint detection and response (EDR). XDR takes a holistic approach to threat detection and response that streamlines security data ingestion, analysis, and prevention and remediation workflows across an organization’s entire security stack. With a single console to view and act on threat data, XDR enables security teams to effortlessly uncover hidden and advanced threats, and automate even complex, multi-step responses across their security technology stacks.
SIEM is primarily a log collection tool intended to support compliance, data storage, and analysis. Security analytics is a capability that has been largely bolted on to SIEM solutions and does not adequately identify threats without running a separate security analytic function on top of a huge data set.
A SIEM ingests log data from a variety of network hardware and software and analyzes the data in real-time. A SIEM’s purpose is to correlate events and identify anomalies or patterns of behavior like traffic from suspicious IP addresses or unusual exfiltration of data that may indicate a breach.
SOAR incorporates orchestration, automation, and response capabilities to the SIEM and enables disparate security tools to coordinate with one another. However, bi-directional connectivity is where SOAR begins and ends. While valuable, SOAR does not solve the big data analytics challenge, nor does it protect data or systems on its own.
XDR has risen to fill the void created by SIEM and SOAR through a distinctly different approach anchored in endpoint data and optimization. XDR has advanced analysis capabilities that enable the organization to focus on the highest priority events and respond rapidly.
SecureOps Resources on Logs, SIEMs, and Network Security Design
We want to make life easy so if you want to know how networks are designed, logs are generated, collected, correlated, and analyzed, often by a SIEM we put together a series of blog posts. Let’s start with our Log Monitoring and Management blog post and learn why logs are so critical to gathering insight into an organization’s IT Security status and issues. Then learn exactly What a SIEM Does in this blog post.
Next, we addressed “The Fundamentals of Network Security Analysis and Monitoring” in a blog post where we discussed active versus passive security devices, flow analysis versus packet analysis, and several of the security technologies used to analyze or stop traffic including IDS/IPS technology. Prior to that blog post, we wrote another post titled “Network Security Design is Critical to Eliminating Security Gaps and Reducing Costs” – “The 5 Pieces to the Cybersecurity Puzzle,” where we discussed the five core elements of Secure Network Design.
Conclusion
Ok, let’s try and put a wrapper on this here in the conclusion. Does XDR replace SIEM and SOAR? Not today and probably not for a while. While XDR offers organizations new security capabilities and enhanced protection, it cannot and should not fully replace SIEM or SOAR. XDR is not a substitute for SIEM because the SIEM has use cases outside of threat detection, such as log management, compliance, non-threat-related data analysis, and management. While an XDR can often fulfill threat-centric and cyber-attack use cases and replace SIEM in that regard, the organization will still have other needs to be fulfilled by the SIEM – particularly compliance such as PCI-DSS.
As for SOAR, this platform offers valuable orchestration capabilities that help the security team optimize resources and prioritize activity. An XDR solution generally does not have these capabilities, which makes it important to maintain the SOAR system and integrate it with XDR.
SIEM and XDR provide value in two different but potentially complementary ways, with SIEM having had its genesis in compliance and evolving to serve as a broader threat and operational risk platform, while XDR had its genesis specifically focused on threats and provides a platform for deep and narrower threat detection and response.
That said, many analysts like Forrester’s Mellen suggested, “The approach that XDR is taking is to continue to increase protections on the endpoints, and then enriching on top of that with all of this really powerful information from the network and different clouds, from identity and access management.” So, while SIEMs hunt for threats by collecting a ton of data, running security analytics on top of it, and “trying to find a needle in the haystack,” XDR approaches threat investigation and response from a different or more holistic angle, thus suggesting that as XDR evolves SIEM’s may as least lose their centerpiece position in security operations and be positioned more of compliance technology.







