Two-Thirds of Organizations Were Hit by a Ransomware Attack Last Year
In SpyCloud’s Ransomware Defense Report, its annual survey of CISOs or Chief Information Security Officers and heads of IT security from Canada, the UK, and US they found that that security teams are starting to lose hope that they can defend against the next ransomware attack. The majority of the 310 participants in the survey came from senior levels: 34% are CIOs, CISOs, and security executives; and 50% are security directors, managers, or team leads. The CISOs and heads of security said in the survey that ransomware is the number one, most concerning issue they face today.
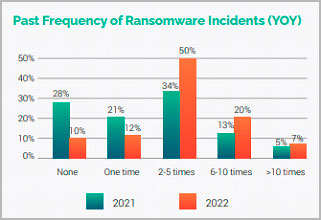
Figure 1 – 77% of Organizations were Hit Over 2x by Ransomware Attacks
More impactful than that last statement is that 66% of organizations were hit by ransomware in 2021, compared to 37% in 2020. Further, the survey showed that although budgets to protect against cyberattacks have swelled by 86%, a full 90% of organizations surveyed said they had been impacted by a ransomware over the past year. In the survey, only 72.5% said they had been affected by a ransomware attack the previous year. We assume the survey results are suggesting that while 66% of organizations were directly hit by an attack, an additional 24% (90%-66%) had a partner or some kind of 3rd party supplier hit by an attack impacting their own company’s supply chain.
“Additionally, more organizations have implemented ‘Plan B’ measures this year, from opening cryptocurrency accounts to purchasing ransomware insurance riders,” the SpyCloud ransomware report said. “These findings suggest that organizations realize threats are slipping through their defenses and a ransomware attack is inevitable.”
Attacks Have Caused Toyota, Lincoln College, and Costa Rico to Suffer Massive Damages
Within the past year, ransomware attacks have forced Lincoln College, a 157-year-old college to close its doors, the leading automaker, Toyota to halt operations for over a day, and Costa Rico, an entire nation state to declare a state of emergency. It is almost daily over the past 2-3 years that we have seen hospitals, schools, and small business impacted by cyber-attacks, particularly ransomware, yet the increase in the number and damage of the attacks on a global basis has become alarming even for those of us keep a close eye on Cybersecurity news stories.
In the first ransomware story we referenced, Lincoln College says it will close in large part due to a ransomware attack that took months to resolve. While the impact of COVID-19 initially impacted activities such as recruitment and fundraising, the ransomware took the Illinois college over the edge from an operations and financial standpoint.
The college has informed the Illinois Department of Higher Education and Higher Learning Commission that it would permanently close as of May of this year. As NBC News notes, it is the first US college or university to shut its door due to the damage from a ransomware attack.
Similarly, Toyota Motor had to halt operations for over a day after a cyberattack on a supplier sparking concerns about vulnerabilities in Japan Inc’s supply chain. While no direct information was available about the criminals behind the attack, it came just after Japan joined Western allies in clamping down on Russia in response to the invasion of Ukraine.
Cybersecurity has become a major issue of concern in Japan, where government critics say responses to hacking threats have stopped operations in a variety of companies, however the Toyota attack was a wakeup call to other major corporations and the Japan government.
Toyota’s (TM) production lines were finally turned back on at all of its 14 factories across the country within 36 hours, Toyota spokespeople said in a statement. However, despite the resilience of the supply chain the attack stalled the output of around 13,000 vehicles.
In our last example of the escalation of ransomware attacks, Costa Rica has declared a state of emergency after ransomware hackers encrypted data on computer networks across multiple government agencies, including the Ministry of Finance. The official declaration, published to a government website in late spring, called the attack “unprecedented in the country” and said that it interrupted the country’s tax collection and exposed citizens’ personal information.
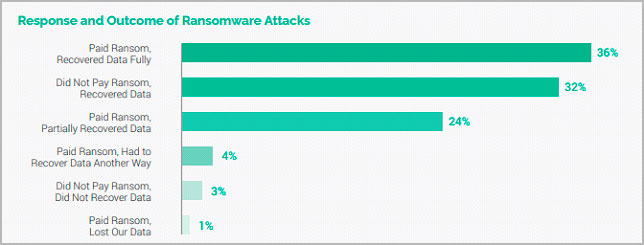
Figure 2 – Surprisingly only 1% of the Sample Paid the Ransom and Didn’t Recover their Data
The hackers initially broke into the country’s Ministry of Finance in mid-April of this year and were able to spread to other agencies in a matter of several days, including the Ministry of Science, Technology and Telecommunications and National Meteorological Institute.
Leon Weinstok, the director of the law firm BLP’s Costa Rica office, who specializes in cybersecurity law, said that the attack had severely impacted the country’s ability to function. “The government has been really affected. It is impossible to quantify the losses at this time,” Weinstok said.
Conti, one of the most destructive of the three or four major active ransomware gangs, is responsible for the attack. Ransomware groups often also try to extort victims by threatening to publish stolen data, and Conti published a large cache of documents, allegedly from Costa Rican government sites to its dark web site Sunday.
Conti is perhaps most infamous for hacking and severely disrupting Ireland’s national health care system last year. The Conti gang is largely made up of Russian and eastern European hackers and declared its allegiance to Russia when the country invaded Ukraine in February, said Brett Callow, a ransomware analyst at the cybersecurity firm Emsisoft.
This week, the U.S. State Department offered a long-awaited $10 million reward for assistance in bringing Conti hackers to justice and said formally that the group was clearly responsible for the Costa Rica hack.
Ransomware Attacks are Increasing Dramatically
Just to give you a final indication of where things are headed in terms of ransomware attacks over the next few years, in last year’s Ransomware Defense Report, the survey found that organizations felt pessimistic about their prospects of avoiding an attack. Only 18% of those surveyed believed a ransomware incident was not likely to happen to their organization, while 22% believed it would likely happen multiple times. We wanted to see if the feeling of the IT security leaders has changed year over year. Unfortunately, but not surprising, this year’s survey found that organizations feel even less confident today in their ability to fight back. The survey found that a significant decrease in the number of organizations that haven’t been hit by ransomware in the past year (10% in 2022 vs. 27.5% in 2021.) And a significant increase in the number of those that have experienced multiple attacks, 50% were hit two to five times in the past year vs. 33.5% the previous year, and nearly 78% of those were hit between two times and 10+ times in the past year vs. nearly 52% the year before. The numbers are concerning because as we noted in a previous blog post, Ransomware and Business Email Compromise (BEC) Account for 70% of Breaches, RaaS or Ransomware-as-a-Service is exploding and giving technical expertise to cyber criminals that would not have had expertise to conduct sophisticated attacks.
In other research that we at SecureOps follow, overwhelmingly points to the ransomware problem continuing its surge. IBM Security researchers in their latest report found that ransomware was, indeed, the biggest issue for IT security leaders across enterprises and small business. The 13% growth seen in ransomware related breaches in the past year is “as big as the last five years combined,” according to the latest Verizon Data Breach Investigations Report (DBIR).
Conclusion
Compared to last year, participants ranked all potential ransomware entry points as more concerning. Unpatched vulnerabilities, phishing, and unmanaged devices are the highest probability threat vectors. We, at SecureOps typically see unpatched systems as one of the main reasons criminals gain a foothold in their victim’s systems. Last year, ransomware was present in 70% of malware-related breaches, according to Verizon’s DBIR.
Phishing, an increasing number of unmanaged personal devices from the work-from-home trend or even shared family devices that are used to access work applications, weak or exposed credentials, and any other of these entry points increase exposure to malware. Each of them creates a risk individually, but together, they act as force multipliers.
Additionally, threat actors target these vectors not only during initial entry but also during multiple stages of an attack, enabling them to escalate privileges, move laterally, and carry out their ultimate
objective.
As we conclude this summary of ransomware incidents and attacks as provided by the awesome work of Spycloud’s Ransomware Defense Report, one of the most concerning issues is that 86% of companies report losing revenue as a result of a ransomware incident and 90% say they lost their ability to operate.
Additionally, 37% report having to lay off employees and 35% say they experienced C-level resignations (which we probably assume they mean terminations as a result of a breach). And while the impact depends on the nature of the business, the overall costs are far reaching. While the average ransom was $812,360 globally last year, the average cost of remediation was much higher – $1.4 million.
We know this blog post was a bit of a bummer due to stunning statistics concerning the growth of ransomware attacks, we will circle back with more positive news about how you and your IT security teams may be able mitigate and defend against attacks.
To Learn More About How to SecureOps Can Help Improve Your Secure Posture Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/







