Organizations Struggle Implementing Compliance Requirements Including NIST & Zero Trust Mandates
Over the last year, we’ve seen a literally flood of government legislation and formal guidance concerning cybersecurity best practices. New mandates have been coming or to the cyber community fast and furious, and government agencies and their contractors have had their work cut out for them trying to keep up and abide by them. In this article, we’ll explore some of the practicalities of implementing the government-issued mandates and guidance and explain why this is currently a topic of lively debate in cybersecurity circles.
In May 2021, President Biden issued an executive order (EO) aimed at improving America’s cybersecurity posture – a move largely in response to the SolarWinds breach among other recent high-profile software supply chain attacks. The Executive Order said the following:
- It instructed federal departments and agencies to implement multi-factor authentication and encryption for classified systems within 180 days
- It provided the Committee on National Security Systems (CNSS) 90 days to come up with a cybersecurity framework for systems in the commercial cloud
- It provided the head of each executive department or agency 60 days to update plans to prioritize the adoption of cloud technology and a zero-trust architecture
Reaction to the provisions of the executive order was lukewarm, even conflicted among most organizations and their IT security leaders. Indeed, Mimecast’s State of Email Security Report for 2022 found that fewer than a third of companies think minimum standards will significantly reduce the level of risk they face; including their approach to securing their businesses, and the investment they allocate to improving their security posture.
This month, cybersecurity leaders across the nation noted with interest a new set of software security guidelines published by The White House. Under the rule, all federal government agencies must obtain “self-attestations” from third-party software providers confirming that they’re following secure software development practices as per government recommendations.
What’s interesting about the latest White House mandate is that it states that developers now need to demonstrate that they’re compliant with the Secure Software Development Framework (SSDF) from the National Institute of Standards and Technology (NIST) at the U.S. Department of Commerce. The NIST Cybersecurity Framework (CSF) is a set of software development practices based on established secure software development practice documents from leading security advocates such as BSA, OWASP, and SAFECode.
The mandate further states that government agencies can also require developers to present a software bill of materials (SBOM) and undertake a vulnerability disclosure program to prove they’re complaint.
Once again, the industry’s reaction to the latest mandate has been mixed. Some industry experts see the initiative as a step in the right direction in building cyber-resilience. Others are less convinced, suggesting that the effort and costs involved in complying with the mandate could outweigh the potential benefits.
One of the sticking points is that (as NIST itself points out, is that “Few software development life cycle (SDLC) models explicitly address software security in detail, so practices like those in the SSDF need to be added to and integrated with each SDLC implementation.” That potentially means a whole lot of extra time and effort.
Other commentators argue that a “point-in-time” attestation is of little value given the dynamic and iterative nature of software development: According to one expert, “Stating that SBOMs may be required by the agency in solicitation requirements, however, in fact it doesn’t solve the problem as software is dynamic, and so are the components that fall under the mandate. Dependencies change over time or become obsolete. While requiring these attestations is definitely a step in the right direction, as it stands now, meeting NIST’s security best practices is required only once with an SBOM, which is only a snapshot in time of software dependencies and does not provide the real-time context that organizations need to truly see their attack surface.”
Some experts take issue with the mandate citing the relative immaturity of SBOM best practices and the added cost burden it will introduce for software vendors: “We are very early in the SBOM era. Most vendors are still working to create SBOMs, and that will continue for the foreseeable future. While a vendor being able to provide an SBOM is an indicator of open-source security acumen, it isn’t the only indicator of overall security acumen. Importantly, if an agency requests an SBOM from a vendor but doesn’t have a workflow to process that SBOM and derive value from it, then having a vendor provide SBOMs adds cost for that vendor without benefit.”
How Can the NIST Framework Provide Guidance for Organizations?
While it’s likely that the debate around the practicality and impact of government cybersecurity mandates will continue over the coming months, businesses in all industries (whether they’re involved in government agency contracts or not) would do well to:
- Thoroughly understand NIST’s CSF
- Be clear where and how aligning with the framework can contribute to a well-rounded cybersecurity strategy
The CSF categorizes all cybersecurity capabilities, projects, processes, and daily activities into five core functions:
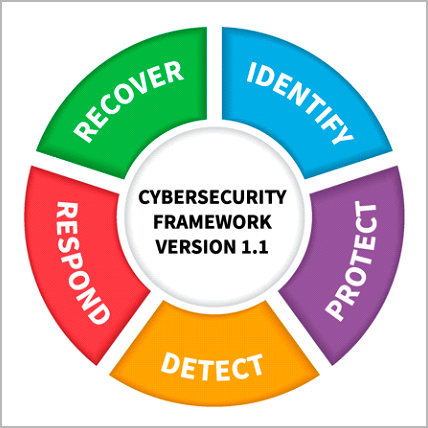
Figure 1: NIST Cybersecurity Framework
Read our Blog Posts on Security Frameworks – Obviously these posts are on the CIS 20, however, many of the recommendations are similar to NIST recommendations:
- How Companies Use CIS 20 to Secure Remote Workers
- The CIS 20 Foundational – Beyond the Basics
- The CIS 20 Organizational Controls – Controls 17-20 Explained
Throughout this lifecycle, IT teams look for anomalies, unusual network traffic, or vulnerabilities and implement security best practices to harden their network’s resistance to hacking.
What’s great about the CSF is that it’s laid out in easy-to-understand terms. That’s good news if not everyone in your company has an in-depth knowledge of cybersecurity terminology and tools. It does a good job of articulating how your data could potentially be put at risk and provides clear actions you can take to mitigate that risk.
Is Every Organization Required to Use the NIST Cybersecurity Framework?
As we touched on earlier, many government agencies and entities are bound to abide by certain provisions of the CSF. However, while the framework can help you improve your cybersecurity defenses and minimize the risk of security breaches, data loss, and potential reputational damage, it’s up to you if you use it.
In the next section, we’ll explore why aligning to the framework makes sense for private sector businesses.
Spotlight On: NIST and the Private Sector
Examples of current NIST workstreams that are relevant to private sector companies include:
Machine learning bias and artificial intelligence bias (also sometimes called algorithm bias) happens when an algorithm delivers results that are flawed or prejudiced as a result of incorrect assumptions being made in the machine learning process. NIST currently has several programs underway to scrutinize this aspect of this emerging technology. It’s also developing an AI Risk Management Framework.
This effort focuses on the implementation of the “zero trust” security approach. With this model, trust is not automatically granted to anything or anyone inside or outside an organization’s perimeters. Access is granted on a least-privileged basis. Anyone seeking access to devices, applications, and data must verify that they are who they claim to be. Under the 2021 Biden Executive Order, federal agencies are required to implement this approach to identity and access management. While private sector companies aren’t compelled to adopt this approach, it certainly makes sense to do so, and thanks to NIST, step-by-step guidance is now freely available.
From smart sensors that can predict manufacturing equipment breakdowns to copiers that order their own toners, IoT helps organizations to better monitor, automate, and manage many aspects of their business operations.
However, IoT devices also represent a clear and present danger. That’s because these devices and their network connections increase a company’s attack surface and create more weaknesses that cybercriminals can exploit.
NIST has been delegated tasks relating to consumer communications, security, and privacy that should be of interest to any business operating in the IoT space.
A recent HSB survey found data breaches among the sample surveyed revealed an uncomfortable truth about the prevalence of cyberattacks on U.S. businesses, the financial impact of these attacks, and organizations’ ability to recover from them:
- Almost a third of US businesses were breached last year.
- 27% of the victim organizations spent between $5,000 and $50,000 to respond to the breach, and 30% spent between $50,000 and $100,000.
- 51% of the executives thought their IT security staff “lacked a plan” to deal with the breach, 41% didn’t have the required knowledge to handle the breach adequately, and 38% lacked the resources.
The good news is that beyond the CSF, NIST has also published a comprehensive incident response framework, an overarching guide that all every business should implement, at least in part.
The four stages of the NIST incident response lifecycle are preparation; detection and analysis; containment, eradication and recovery; and post-incident activity.
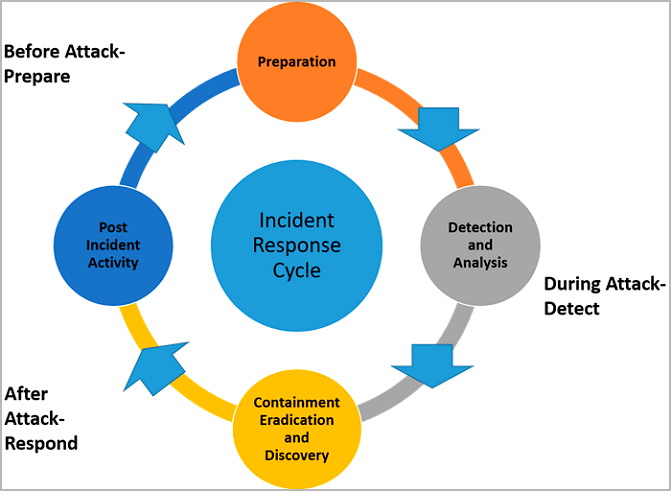
Figure 2: NIST Incident Response Lifecycle
Spotlight On: NIST for Specific Industry Sectors
The NIST framework offers a comprehensive set of guidelines that apply to companies in nearly all industries. Let’s take a look at its relevance to two key sectors: financial services and healthcare.
NIST and Financial Services
Financial institutions carry vast amounts of personal information and other sensitive data that cybercriminals can monetize. While some larger players are ahead of the curve with their information security, it’s not universally true.
Digital technology has seen an explosion in mobile banking apps. It’s also spawned a new wave of smaller fintechs and led to the greater interconnection between these smaller entities and larger traditional players. This introduces the potential for more vulnerabilities to enter the financial services ecosystem.
The average cost of a data breach is around $4 million, according to Ponemon and other resources but in the financial services sector, the costs can run even higher.
NIST is actively working with financial services industry experts and vendors to develop best practices and standards that can help mitigate the various cybersecurity and privacy risks in this sector.
NIST and Healthcare
NIST is updating its cybersecurity guidance for the healthcare industry to help healthcare organizations better protect their patients’ personal health information.
NIST’s July 2022 publication, Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security Rule: A Cybersecurity Resource Guide, is designed to assist the industry in ensuring the confidentiality, integrity, and availability of electronic health information.
Spotlight on: NIST and the Protection of Critical Infrastructure
Arguably of more critical and widespread importance, NIST is currently revising its foundational Framework for Critical Infrastructure Cybersecurity. This document was initially created in 2014 and subsequently revised in 2018.
All this attention on protecting the U.S.’s critical infrastructure is warranted. Research published in June revealed that 89% of electricity, oil and gas, and manufacturing firms have experienced cyberattacks that impacted production and energy supply in the last year.
The research also found that:
- 40% of victims were unable to thwart the initial attack.
- 48% of those whose operations were disrupted said they didn’t always make improvements to minimize the impact of future cyber-risks.
How Managed Services Providers Can Help You Get the Most Out of the NIST Cybersecurity Framework
Many companies see value in enlisting the support of managed services providers to help them achieve the objectives outlined in the CSF.
The best managed services providers have specialized knowledge and many years of experience in identifying organizations’ cybersecurity needs and improving their security hygiene in line with NIST’s recommendations.
Closing Thoughts
The proliferation of government cybersecurity mandates and guidelines have many federal agencies and their contractors and developers scrambling to revise and/or update their security protocols and practices. It’s an interesting area to watch, and we’ll likely be hearing much more from the White House in the months ahead.
As we’ve explored, organizations in the private sector are, for the most part, only tangentially affected by EOs and other government mandates. However, forward-looking enterprises appreciate the wisdom in familiarizing themselves with the latest best practices and guidance issued by the government and NIST.
One strategy to ensure you extract maximum value – and security protection – from this guidance is to work with a managed services provider to understand where implementing these best practices will be most impactful and cost-effective.







