How to Implement an Effective Vulnerability Management Program
We’ve written considerably on Vulnerability Management, Vulnerability Assessments and Patching because they are so critical to preventing attacks. I’ve provided links to several of the most read blog posts we have written on the subject. In this blog post, we’ll discuss several aspects of vulnerability management that has evolved, and we’ll discuss a risk-based patch strategy in our conclusion.
Assessing and Mitigating the Log4j Vulnerability – A Vulnerability Management Case Study
https://secureops.com/blog/log4j-vulnerability-management/
Developing a Risk-Based Vulnerability Management Program A Real-Life Case Study
https://secureops.com/blog/vulnerability-management-program/
ZeroLogon Illustrates Importance of Vulnerability Management
https://secureops.com/blog/zerologon-vulnerability/
What You Need to Know About Vulnerability Assessments
How Vulnerability Assessments Differ Across Providers
https://secureops.com/blog/effective-vulnerability-assessments/
Before we get started, consider the fact that several major cyberattack campaigns, including those like the WannaCry ransomware outbreak and the Equifax data breach exploited vulnerabilities that had patches available and were officially announced as being actively exploited by cybercriminals.
Nearly 60% of data breaches in the past two years can be traced back to a missing operating system patch or application patch, researchers report. Poor patch management can be linked to the high costs of downtime and disruption. The stat comes from Automox, where a team polled 560 IT and security pros at companies with 500 to 25,000 employees. They learned 81% had suffered a breach in the past two years. Thirty-six percent of those incidents stemmed from a phishing attack, which was the most common root cause, followed by missing OS patch (30%), missing application patch (28%), OS misconfiguration (27%), insider threat (26%), credential theft (22%), and brute force (17%).
“Everyone is aware that phishing attacks are a top root cause for data breaches,” says Jay Goodman, strategic product marketing manager with Automox. “What we found is there is a surprising amount [of] OS patches, application patches, and misconfiguration mistakes that led to root the cause for data breaches.”
Less than half of the businesses Automox surveyed would be able to patch critical vulnerabilities within 72 hours of their disclosure, and only 20% could patch zero-day flaws within a 24-hour period.
I wanted to bold those last statistics because they are a perfect segway into why vulnerability assessments, patching, and vulnerability management are so critical. If you consider Log4j/Log4Shell, that vulnerability exists on millions of systems and technologies. If organizations couldn’t patch that vulnerability on high-value systems with sensitive data within 24-72 hours, the risk that a cyber criminal scanned for and exploited that vulnerability is extreme.
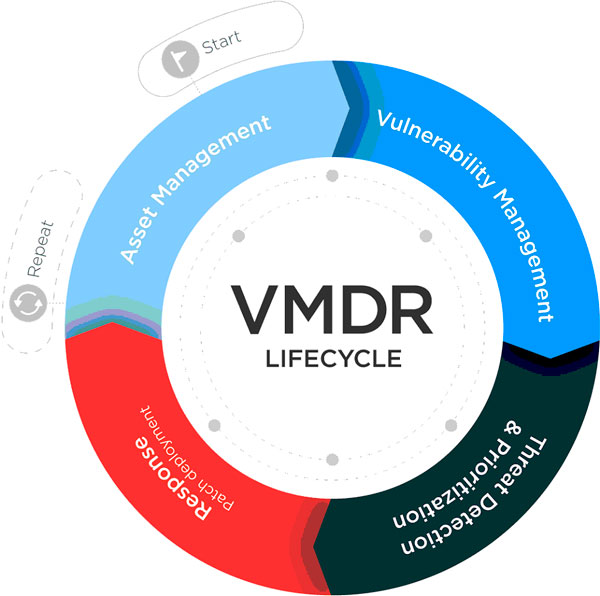
What is Effective Vulnerability Management?
Vulnerability management exists for the purpose of identifying and remediating vulnerabilities in systems quickly before they are exploited. Vulnerabilities, which are essentially weaknesses within software can lead to a system or network that can be exploited by attackers. These vulnerabilities must be identified, assessed, and patched regularly to ensure ongoing security. In order to create and maintain a strong security posture, business owners and security officers must be keenly aware of the vulnerabilities in their systems, as well as the process by which they can be quickly patched. If vulnerabilities are not identified or remediated, companies leave themselves open to attacks.
Vulnerability Scanning and Management has Evolved
Vulnerability scanning and assessment used to be a point-in-time exercise with patching often performed on a weekly or monthly schedule. However, for organizations that have a more mature security posture, scanning, assessment, and patching have evolved. The practice is continuous and as we suggested before based on the following considerations:
Four important considerations are:
- The criticality of the affected system
- The exploitability of the vulnerability
- The potential impact of exploitation
- Are there viable alternatives to patching?
1. Continuous Network Scanning
Yearly or quarterly vulnerability scanning is no longer sufficient to detect risks in your IT system. You need a proactive, 24×7 continuous defense to stand a chance against the hackers incessantly probing your network.
2. External Vulnerability Scans
This type of scan looks at your network from the hacker’s perspective. It scans external IP addresses and domains, probing for vulnerabilities in internet-facing infrastructure to determine which ones can be exploited.
3. Internal Vulnerability Scans
Performed from a location with access to the internal network, internal vulnerability scans are more complex than external ones because there are simply more potentially vulnerable assets within your organization. This scan will discover and catalog your core IP-connected endpoints, such as laptops, servers, peripherals, IoT-enabled machines, and mobile devices.
Vulnerability Assessments are Simply a Snapshot of System Vulnerabilities
Vulnerability management is an ongoing process that includes scanning for vulnerabilities, assessing the risk involved with each one, and then prioritizing vulnerabilities for remediation. With an experienced IT security team, this cycle never stops. Scanning and assessment lead to remediation, which then leads to a new cycle of rescanning. It is a process that ensures new vulnerabilities are quickly found and eliminated to minimize the risk of an attack. This long-term vulnerability management process is different than a one-time vulnerability assessment, which gives the company a snapshot of its system vulnerabilities at a single point in time.
A one-time vulnerability assessment is a process of scanning for and identifying possible vulnerabilities and risks within the system. Although an ongoing vulnerability management system is far more effective than a one-time scan and assessment, there are reasons why companies might choose to only do a periodic vulnerability assessment. Reasons include cost savings associated with not having a full-time internal security team or they may have a security program in its early stages, or they simply want some validation of current security efforts and processes. Also, PCI compliance, other compliance requirements, and cybersecurity insurance providers may demand vulnerability assessments and some rudimentary vulnerability management processes.
Clearly, for successful, long-term protection, businesses must invest more in their security program than a one-time assessment. Each organization needs a continual and ongoing vulnerability management program. Software is continually being updated and thus, new vulnerabilities are consistently introduced to the IT environment.
If new vulnerabilities are created after a vulnerability scan is run, they will obviously go unnoticed until the next scan. Many organizations only scan quarterly, however, with 22,000 known vulnerabilities found by the CVE last year up from just 12,000 two years ago, it is wise to scan much more frequently so as not to leave vulnerabilities left unpatched for any significant period of time. Frequent and consistent scans should be implemented to ensure quick identification of vulnerabilities.
Effective assessment and management systems will not only include vulnerability scans, but also proper firewall rules review, VPN configuration, wireless assessment, and infrastructure review. The more areas you are monitoring and configuring for protection, the better your security posture or cyber hygiene will be.
Vulnerability Management Must Include System Value and Vulnerability Criticality
As we quoted in a previous blog post, a recent Verizon Data Breach Investigation Report claimed “98% of security incidents and 88% of data breaches continue to occur within one of nine patterns.” Understanding and taking steps to guard against the common patterns and approaches attackers use to infect your system will greatly increase the security posture of your company. The most important way to do this is to frequently scan for known vulnerabilities. These common weaknesses often have patches available from the software manufacturer that will eliminate the vulnerability.
It’s also important to remember that each of the devices, environments, and frameworks that comprise an organizations’ system present a different type of risk. A research report from Ponemon Institute analyzed IT Security spend trends and found considerable gaps between the perceived level of risk for some of the attack vectors and the level of annual spending for the different protection layers. An effective vulnerability management policy will properly address each type of security threat and ensure that the right processes and tools are put in place to address the level of risk introduced by different vectors and layers.
Consider the recent Log4j/Log4Shell Java vulnerability that exists on millions of systems. Organizations were challenged to create a risk-based patch management strategy to identify the most critical systems with the vulnerability, prioritize patching those systems, test the patch, then move to the next system. Organizations were overwhelmed; many had thousands of systems and technologies that ultimately needed to be patched. Further, as you can see from the image above, attackers were scanning for the vulnerability when the Zero-Day was announced. This allowed attackers to infiltrate systems and networks to wait for the right time to strike.
Ultimately, IT Security teams have 3 choices when it comes to patching a system:
- Remediation: Completely preventing exploitation by patching, correcting, or replacing code that contains a vulnerability.
- Mitigation: Reducing the probability or impact of a vulnerability. This is usually a temporary solution that organizations use until they can remediate the vulnerability.
- No action: Acknowledging and accepting the vulnerability. Organizations typically only do this when the cost of remediating the vulnerability is much higher than the consequences of it being exploited.
A Risk-Based Patching Strategy is Optimal
“It’s a scale issue and it’s a prioritization issue,” says Stephen Boyer, co-founder, and CTO at BitSight. “Think about all the vulnerabilities coming at you. The key question is which vulnerabilities [to patch] and when.”
Patching is pricey, and larger businesses suffer greater losses in disruption and downtime. Boyer refers to a defense contractor as an example: There, he says, it could cost $250,000 to roll out a single patch. Not all fixes are this expensive, but let’s say the average hourly wage for a company is $25 per hour, and updating a system disrupts work for 10 minutes per employee. With an employee base of 50,000 people, that amounts to about $208,000 in lost productivity.
Whether or not a vulnerability has been weaponized and is actively exploited should be a major factor in determining the speed at which an organization patches a vulnerability. Several major cyberattack campaigns, including those like the WannaCry ransomware outbreak and the Equifax data breach exploited vulnerabilities that had patches available and were officially announced as being actively exploited by cybercriminals.
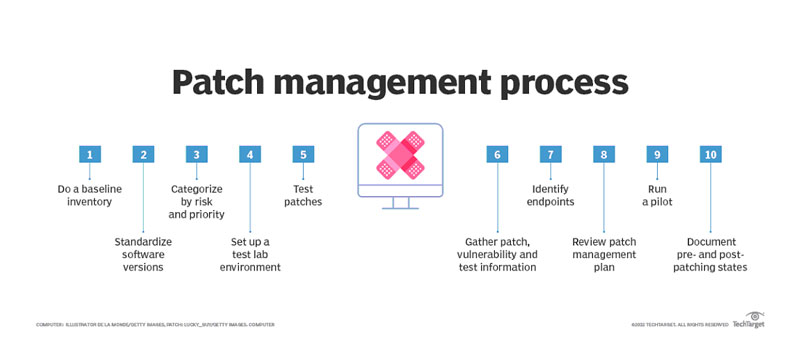
Risk-based patch management is part of an overall vulnerability management program and is an IT security strategy in which organizations prioritize the patching or remediation of software vulnerabilities according to the risk they pose to the organization.
A risk-based vulnerability management or patching strategy has several key components:
- It assesses the importance and the business context of systems; not all systems are created equal and an intrusion into some segments of a network may be more damaging or likely than others.
- It leverages intelligence from CVE to NIST to generate risk scores based on the likelihood of exploitation by attackers.
- It leverages threat intelligence to identify the vulnerabilities attackers are discussing, experimenting with, or using. Meaning have attackers created malicious code or an exploit to take advantage of the vulnerability.
- It combines asset criticality and intelligence risk-based patch management programs focus patching efforts on the vulnerabilities that are most likely to be exploited and that reside on the most critical systems.







