What are the Benefits of SOAR Security Technology?
Choosing the Most Effective Security Technology – SIEM versus SOAR
In a previous blog post, Why Organizations Are Moving to Managed Firewall and SIEM Solutions, we addressed not only the benefits of Firewall and SIEM security technologies, but also the challenges. We started with the basics suggesting that a firewall is a network security device that examines network traffic. Based on rules and policies, the firewall inspects network traffic to block the traffic that is suspicious or unwanted. Firewalls developed by industry leaders like Cisco, Palo Alto, and Fortinet have been the first line of defense in network security for over 25 years. They establish a barrier between secured and controlled internal networks that can be trusted and untrusted outside networks.
Then we defined SIEM’s, suggesting, “Log Rhythm, Splunk, Alien Vault, and many others provide the critical data and information that IT security teams require including security event data and network flow data. SIEM’s have become the core of most IT security operations and solutions because of their ability to normalize and analyze data. Simply, they collect logs and data from dozens of disparate devices to provide a flow of correlated insights to threats from a single source in real time. Further, SIEMs can be set up to deliver alerts to the security operations team when suspicious activity is uncovered or to simply gain better visibility to vulnerabilities and threats in the environment.”
We also wrote a blog post specifically discussing The Benefits of Using a SIEM to Improve IT Security, where we walked through the functions and benefits of a SIEM including, “SIEM’s have 3 critical capabilities in most organizations: (1) Threat Detection (2) Investigation and (3) Time to Respond. SIEM’s were developed to collect, store, analyze, investigate, and report on a log and other data for incident response, forensics and regulatory compliance purposes.”
Differentiating SIEM versus SOAR Security Technologies
The alphabet soup of security technology acronyms is not only growing but the functionality and use cases are overlapping one another. In our last blog post, Is an MDR Solution or an MSSP Partnership Better for Your Organization?, we discussed the difference between MDR or Managed Detection and Response and an MSSP or Managed Security Solutions Provider like us here at SecureOps. Frankly, the differences are dramatic, however, in an industry where MDR and EDR are leveraging a variety of different security technologies including log analysis, artificial intelligence, intrusion detection, and more, we need to be clear about the functionality and use cases of each technology so you can build the most effective and cost-efficient security defense.
Ok, apologies for the long introduction, however, we wanted to be clear about the different security technologies and the purpose of this blog post. Now the major question of this post is – should security orchestration, automation, and response (SOAR) replace security information and event management (SIEM), or do they serve two different purposes? The short answer is that while the two technologies share several common components, they absolutely serve different purposes in the SOC or Security Operations Center. As heads of IT security search for new technologies to upgrade their security defenses to meet the requirements of cloud environments, automation has become a key priority.
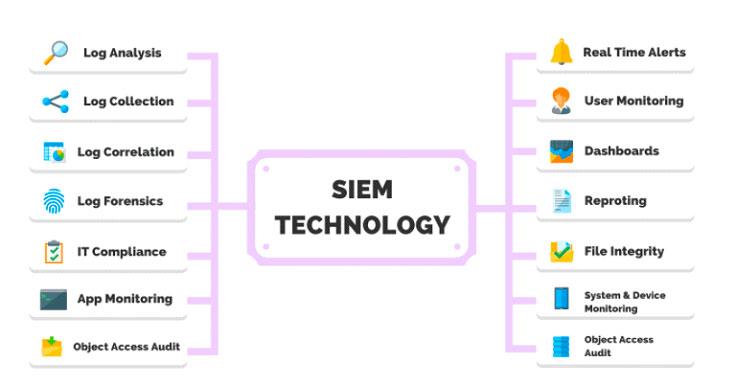
What are the Benefits and Use Cases for SIEM Technology?
SIEM technologies combine the capabilities of security information management (SIM) and security event management (SEM) tools into a comprehensive solution for cybersecurity. Typical functions of a SIEM software tool include:
- Collecting, analyzing, and presenting security-related data
- Real-time analysis of security alerts
- Logging security data and generating reports
- Identity and access management
- Log auditing and review
- Incident response and security operations
What are the Primary Benefits of a SIEM
- Vulnerability management – an ongoing process of proactively testing your network and IT infrastructure to detect and address possible entry points for cyber-attacks. SIEM software tools are an important data source for discovering new vulnerabilities, along with network vulnerability testing, staff reports and vendor announcements.
- Incident investigation – When a breach is detected, SecOps teams can use SIEM software to quickly identify how the attack breached enterprise security systems and what hosts or applications were affected by the breach.
- Threat intelligence – The analysis of internal and external cyber threats that could affect your business. SIEM software tools provide a framework for collecting and analyzing log data generated within your application stack.
- Compliance – SIEM software tools can streamline the compliance process for organizations affected by data security and privacy compliance regulations. With SIEM tools, organizations can monitor network access and transaction logs within their database to verify that there has been no unauthorized access to customer data.
What are the Use Cases for SOAR Technology?
In a recent blog post, Why Incident Response Technology has become Critical to Limiting Damage, we said “over 80% of small and midsized organizations reported suffering at least one cyber-attack in the last 12 months, with an average cost of nearly $1 million to restore servers, databases, other systems, and data to return to normal business operation after a successful attack. With such high costs associated with significant attacks, organizations must be prepared to detect and respond to attackers if they are to limit damage and subsequently reduce costs to maintain their business.” SOAR optimizes processes and allows the orchestration of different technologies into standardized response procedures for each type of attack, called Standard Operating Procedures (SOPs). It also automates repetitive tasks within these processes and ensures that all analysts follow the same procedures.
SOAR leverages the power of playbooks, machine learning, and progressive automation to enhance threat intelligence and speed up security processes. SOAR relies on machine learning to predict repeatable patterns to help SOC teams distinguish between false positives and negatives and intercept and approach cyber-attacks proactively, rather than reactively.
What are the Primary Benefits of a SOAR Solution?
- SOC process optimization
- Incident response
- Threat investigation and hunting
- Threat intelligence management
Security analysts recognize the necessity for cloud-based SOAR, with adoption growing over 85% year over year. Cloud SOAR addresses critical customer requirements:
- Reduces false positives and duplicate events reducing SIEM “noise”
- Seamless integration of other security tools and proprietary solutions with little manual coding
- Provides support to both MSSP and complex corporate environments
- Machine learning enables workflow-based automation by providing the right IR playbooks to respond to events or incidents
- Manages all aspects of the incident case management, from identifying an event through response and remediation
What are the Differences Between SIEM and SOAR Security Technologies
Let’s start with the similarities first – both SIEM and SOAR aggregate security data from various sources, that said, the locations and quantity of information sourced are different. While a SIEM ingests log and event data from traditional infrastructure component sources which include dozens, if not hundreds of systems and devices in an organization, a SOAR solution retrieves information from external emerging threat intelligence feeds, endpoint security software, and other third-party sources to get a better overall picture of the security landscape to help create efficiencies in the SOC.
For example, a Security Orchestration, Automation, and Response (SOAR) tool provides one of the best ways to automate the incident response process. By leveraging SOAR (defined here by Gartner), security teams can effectively triage alerts, respond quickly to critical cybersecurity events, and deploy an efficient incident response program.
To re-emphasize, the term was initially coined by the research firm Gartner, which has since outlined three core capabilities of SOAR technologies:
- Incident response workflow
- Data enrichment
- Security controls automation
Automation brings advanced proactivity, consistency, and speed to incident detection, response, and mitigation. Instead of manually copying and pasting evidence of a threat, analysts can focus on stopping attacks before they cause irreparable harm. Security operations also become more efficient as they improve mean-time-to-resolution (MTTR).
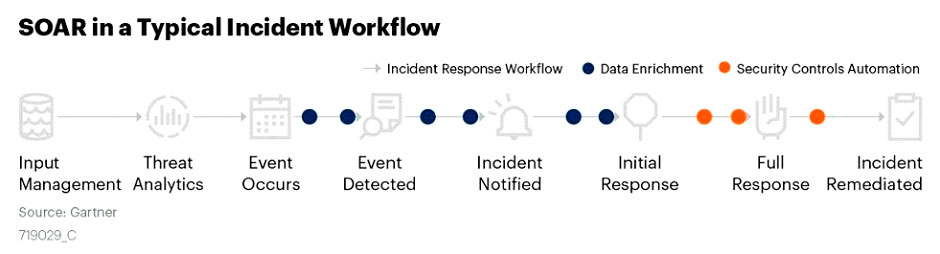
After a SIEM provides an alert, it’s up to the administrator to determine the path of an investigation. In contrast, a SOAR automates investigation path workflows to begin triaging and subsequently apply remediation processes. In other words, a SOAR solution starts from where a SIEM’s capabilities end. In practice, the two are complementary and work best in tandem.
Leveraging SIEM and SOAR technologies to optimize your SOC will answer the following questions
- How can I make our SIEM and threat intelligence data actionable and more effectively investigate alerts and incidents?
- Given the increase in volume and scale across a growing attack surface, how can I prioritize my response to security incidents?
- How can I rapidly respond to security incidents confident that analysts are following defined SOPs?
Conclusion
First, as we suggested previously, the two solutions can work in conjunction: with the SIEM detecting the potential security incidents and triggering the alerts and the SOAR solution responding to these alerts, triaging the data, and taking remediation steps where necessary. With SIEM platforms integrating SOAR-like functionality to increase response, SOAR can add significant value to an existing SIEM solution.
Every organization should take security practices very seriously, and SOAR is a proven solution for all organizations, as they continue to struggle with increasingly high volumes of information about security and network activity. Multiple teams need to interact with security platforms, and SOAR can help keep everything centralized, efficient, and responsive.
A Deep Dive into the Key Benefits of SOAR
1. SOAR helps build workflows & streamline operations
Orchestration layers are more successful with the implementation of plugins for the most common use cases and technology, which provide pre-built workflows. IT processes and security workflows can then be automated, and your technology stack can be connected and collaborative. Many manufacturers of SOAR technologies create plug and play technologies so that bringing in diverse security tools is painless.
2. SOAR empowers teams to increase flexibility and collaboration
SOAR solutions can provide the flexibility to either adapt the templated use case workflows to your processes or build out new workflows easily. There are also collaboration opportunities between other organizations, among teams, and across the enterprise, which can further the need of customization and development of current and new workflows.
3. Respond to events and incidents faster and with better data
SOAR solutions constantly gather information and prioritize incidents using automation that functions based on both pre-planned and custom rules. Leveraging this data delivers faster and more accurate incident assessment and prioritization, which can then be utilized to confirm whether a threat is valid.
4. Improve SOC efficiency and productivity
Automated responses to threats using SOAR allow employees more opportunities to focus on priority tasks rather than digging through the through SIEM alerts to determine which alerts and events warrant further investigation and which do not.
5. Effectively manage security incidents
SOAR technology accelerates incident response time to threats and as we said before also, increases the accuracy of responses. Rather than having to analyze dozens if not hundreds of logs through a SIEM machine and data-driven workflow through SOAR technology significantly reduces the chances of human error, such as missed relevant data, misinterpreted analysis, or also false positives.
6. Automate the handling of alerts
SOAR solutions can make security more self-operating and less manual—this helps eliminate repeated tasks, like constantly checking alerts and data that are continually gathered. Repeated tasks and constant human interaction can increase the chance of human error. Automated programs can significantly reduce errors, especially as monotonous tasks are eliminated.
To Learn More About Managed SIEM and SOAR Technologies or If You Have Been Attacked, Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/