What Does Web 3.0 Mean for Cybersecurity?
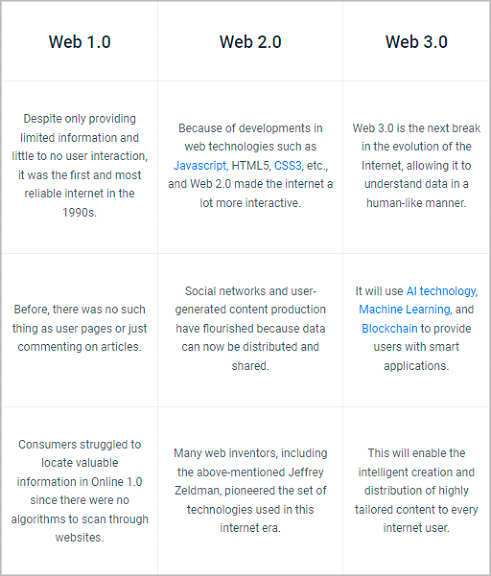
The basic definition of Web 3.0 is it will be the next significant evolution of the internet in which all web data is machine-readable. Each web page has semantic metadata that describes to computers the meaning of the page’s elements. Through semantic metadata, the web is able to operate as a single, massive, connected database. Search queries can leverage this machine readability to provide far more accurate search results. Web 2.0, which is the current version of the internet, has been plagued by attacks and breaches; Web 3.0 promises a new cybersecurity landscape with both positive and negative attributes.
In our recent blog post, CISO’s Earning a Seat at the Board, we discussed digital transformation strategies, including expanding globally into new markets with new products and how it adds new risks and potential cybersecurity concerns across an organization’s attack surface. In this blog post we’ll discuss Web 3.0 and how it represents the next phase of the evolution of the web and potentially could be as disruptive and represent as big a paradigm shift as Web 2.0 did; and in many respects is still doing.
Web 3.0 is built upon the core concepts of decentralization, openness, and greater user utility. The progression of more internet capabilities becoming part of Web 3.0 autonomous systems will require organizations to develop, migrate, and adopt blockchain, adaptive AI, and develop decentralized applications, even with the potential increase in risk and cybersecurity attacks.
Our current web 2.0 systems and content processes will be slowly replaced in large part because of searchability but also because of privacy, data ownership, and security risks. To be clear, web 3.0 is the third iteration or version of the Internet that interconnects data in a decentralized way to deliver a faster and more personalized user experience. It is built using artificial intelligence, machine learning and the semantic web, and uses the blockchain security system to keep your information safe and secure.
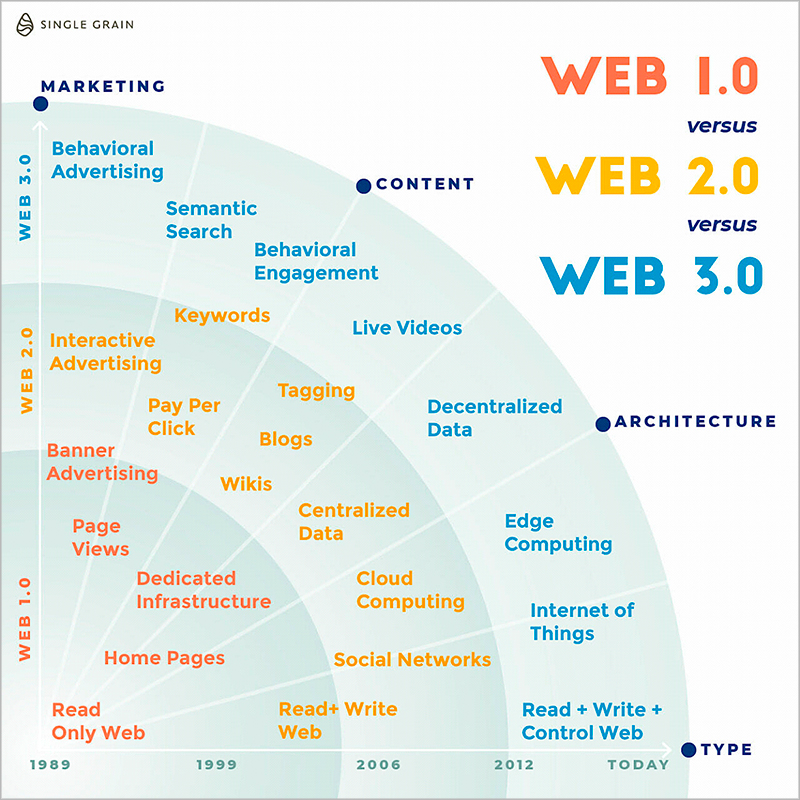
To get us started on our discussion in this post, here is a brief history of the Internet:
- Web 1.0 is a read-only web where people can read information written on websites.
- Web 2.0 is a read-write web where people can read and write content on websites and applications.
- Web 3.0 is a read-write-interact web (powered by artificial intelligence) where people can read, write, and interact with content, including 3D graphics, on websites and apps.
The Metaverse is Web 3.0
The term ‘metaverse’ is a hybrid term that combines the worlds of ‘meta’ and ‘universe.’ It is used primarily to refer to an anticipated future iteration of the internet that’s often hailed as Web 3.0. This evolution of the internet is expected to see the rise of online 3D or virtually integrated environments that provide users access to virtual reality and augmented reality experiences. The metaverse is a fully immersive successor to the internet. It’s a combination of virtual reality (VR), augmented reality (AR), mixed reality (MR), gaming, cryptocurrencies, and social media.
The evolution of this critical communication medium continues to drive global adoption of the interconnection of people, services, and ideas. How people access services or share ideas continues to push the progression from web 1.0, 2.0, and in the near future 3.0.
Another significant component of web 3.0 is the expansion of artificial intelligence and the adoption of blockchain technology. While AI has a strategic role in web 2.0, this capability to rationalize more data while creating usability functions, including auto-remediation when responding to high-velocity cybersecurity attacks, enables the ability for innovative contract capabilities within the blockchain. AI-fueled data rationalization feeds into machine learning algorithms with little, or no human interaction is the cornerstone of 3.0.
Security Impact on Decentralization
Web 1.0 and 2.0 delivered various platforms to users to store their data, access hosted applications and access content anywhere in the world. However, accessing the user’s data and how the hosting platform was using the user’s data will continue to be controversial. Users want to host their content on a site of their choice.
Tim Berners-Lee (inventor of web 1.0) coined the term web 3.0 to mean a web-based data that both humans and machines could process. Web 3.0 adopts artificial intelligence and the metaverse. Both innovations encourage a completely immersive experience where exploration is cutting-edge and simplified.
One of the main privacy issues with the metaverse is the sheer amount of personal data (PII) available. The data that will likely be collected on users will be far more intimate and in-depth than what is collected in our current web 2.0. Companies will be able to track biometric data such as facial expressions and vocal inflections in real-time. This means user behavior will be monitored and used for personal advertising campaigns. A user’s privacy on Web 3.0 will be non-existent if stolen.
Web 3.0 decentralizes the internet. While this model benefits the user, the lack of central data access expands the attack surface considerably in many ways and makes it more difficult to stop cyber-attacks. In addition, the lack of centralized data will be problematic when it comes to online harassment, hate speech, and inappropriate or criminal images. In a decentralized web, who will enforce worldwide hosted content?
Trusting the Source Data
A significant element of web 3.0 will be the acceptance of decentralization and peer-to-peer relationships. Users will have complete autonomy with their data. Countless stories have surfaced about Amazon’s aggressive business practices, Facebook’s privacy infractions, and Google’s data privacy issues and unethical AI use, all of which raise serious safety alerts about web 2.0.
Source Data Corruption
Source data corruption happens at the inception of the content creation process through the elevation into the adaptive AI layer. Many AI vendors continue to develop intelligent methods to trust and verify data before rationalization, source data corruption, and the sheer amount of data that will carry risks to the organization.
A core component of adaptive AI is the ability to rationalize more defined and integrated data sets across several sources. They feed more data into the adaptive AI. The more defined elements could provide machine learning layers. In a recent paper by Meta engineering, the team concluded, “multiple detections and mitigation strategies bring additional complexity to large-scale infrastructure. A better understanding of these corruptions helps us increase our software architecture’s fault tolerance and resilience of our software architecture.”
Security Issues will be New and Unique with Web 3.0
The complexity of Web 3.0 alone is a leading indicator of expected cybersecurity risks for organizations. Decentralized applications (DAPPS), including car leasing, apartment contracts, medical record billing, and cross-border financial transfers, will benefit from web 3.0 technologies. However, these new capabilities will be subject to a new generation of cybersecurity attacks, including smart-contract logic hacks.
Redefining Trust Boundaries in Web 3.0
In a Gartner research article, more CEOs and CIOs are approaching the board of directors to make a case for blockchain as a strategic component. CEO’s and fellow business leaders understand that enterprises must speed up blockchain initiatives as part of the enterprise digital transformation, or risk falling so far behind that they permanently lose a competitive edge.”
Blockchain technologies can dramatically improve several key industries or components of industries including supply chains, healthcare, and electronic payments.
Blockchain Reality for Web 3.0
Blockchain plays an essential role in the peer-to-peer relationships by providing levels of data integration through ledger-based security. A significant protection against source data corruption will be the implementation of user-driven access and blockchain deployments.
To make Web 3.0 work, we must eliminate intermediaries. We can do this by eliminating the centralized databases used today. A new type of database called Distributed Ledger Technology (DLT) is being developed. DLTs store information in blocks (groups). Blocks hold a set of data. Once a group is entire, it closes and connects to the previous group. Therefore, a series of blocks form a single file. Different groups of information enter a new group. One of the critical features of DLTs is immutability; every transaction is permanently stored and cannot be changed or deleted. Thus, DLTs are also known as distributed ledgers.
Web 3.0 and Decentralized Applications
With decentralized applications (Dapps), users will control access and implement their governance toward many capabilities, including cross-border payments through crypto-wallets ensuring autonomous privacy protection. Governments and law enforcement will address many challenges in stopping global financial crimes by moving towards an accurate peer-to-peer payment model with no centralized monetary authority.
DAPPSs move freely between platforms by the user or application owner. These users decide which public blockchain they wish to distribute their crypto applications.
According to the latest statistics from CoinMarketCap:
- There are over 20,000 cryptocurrencies on in circulation as of July 2022
- There are about 36.5 million American crypto users and 300 million global crypto users as of 2021
- We expect the global blockchain market value to reach $67.4 billion by 2026, with a CAGR of 68.4%
Cryptocurrency will Present New Security Challenges
Privacy is a driving force behind Web 3.0, however, the ability to contain spam and disinformation will be a continuous challenge. The autonomous system must define whether to accept or deny the content source.
Blockchain technology is becoming an integral part of our lives. Startups and leading digital enterprises use it to solve real-world issues and create value that traditional technologies and processes can’t. We currently value the cryptocurrency market at around $2 trillion, meaning governments and large corporations hold billions of dollars’ worth of cryptocurrencies.
Smart contracts are currently unregulated, which means they’re vulnerable to hackers. Regulators still need to be ready for Web 3.0, so companies need more legal protection using these technologies.
Conclusion
Web 3.0 has the potential to be just as disruptive as Web 2.0 was and still is, however, Web 3.0 promises an enormous paradigm shift. The fundamental ideas of decentralization, openness and increased consumer usefulness form the foundation of Web 3.0. Unlike Web 2.0 however, security needs to be an essential element from the outset of Web 3.0’s design and functionality if this next evolution is to succeed without adding risks to users and organizations.
Web 3.0 will allow personal data to be stored on the edge so that PII can be used to help with buying decisions, search, and information. However, on the devices people use to interact with applications, there’s an even greater need for adequate protection of endpoints and networks through detection and response capabilities.
The same security risks that have plagued Web 2.0 including spam, phishing, social engineering, and identity risks will likely remain a problem in 3.0. For example, spam campaigns will have the ability to deliver malicious JavaScript code or ransomware inside an application and deliver it to anyone using the application. Spam risks could include nation-states manipulating data on web pages in an attempt to feed AI algorithms with disinformation that then spreads to the citizens of a country.
Phishing attacks on Web 3.0 may see malicious threat actors impersonating legitimate third parties in an attempt to harvest confidential information about individuals or businesses. We see this in Web 2.0, however because Web 3.0 will have more personal information, and information stored across a variety of locations, PII will be more difficult to protect.
Nonetheless, Web 3.0 is coming, and cybersecurity teams need to ready for a new set of challenges. Its going to be interesting for certain.
To Learn More About How to Secure Your Organization Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form to Talk with a Security Specialist – https://secureops.com/contact-us/







