Nine Out of Ten Organizations Fail to Address Security Risks
Foundry, Formally IDG Survey Points to a Major Shift in Cybersecurity Spending
While CEOs and CFOs develop forward-thinking strategies around new markets, products, and services to attract new customers, CISOs and CIOs continue to adjust their cybersecurity strategies. Changes to organizational processes often happen to adapt to market conditions, competitive edge landscape, and the company’s overall performance.
As organizations continue their digital transformation strategies to revolutionize their businesses, cybersecurity leaders must adjust their approach to protect these new corporate assets. According to a Survey conducted by Foundry, formally IDG’s survey of 872 security leaders from North America (55%), EMEA (18%), and APAC (27%) provided interesting cyber defense insights.
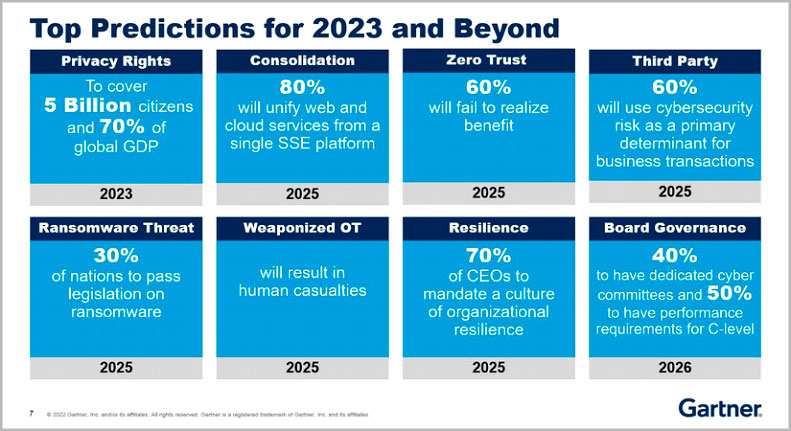
The survey suggests that 87% of most organizations fully know how their companies have been breached in the past year. Most organizations are dealing with the ongoing global ransomware attacks, email phishing, and data exfiltration from their cloud storage data lakes is a daily challenge. Each additional business asset adds new attack surfaces to the threat landscape, and as depicted in the Gartner Top Predictions for 2023 and Beyond, the security challenges will increase significantly.
What strategies will help enable better infrastructure protection and complete visibility?
Increase in Cybersecurity Investment to get ahead of the next wave of attacks.
In 2022 alone, organizations will spend an additional $55 million on cybersecurity protection, up $11 million from 2021. This increase in spending is a direct result of several factors:
- Organizations are rapidly reshaping their organization to be more agile and competitive in the post-COVID world.
- Organizations continue to leverage digital transformation strategies to reduce the cost of their operations while creating new services and capabilities for their clients.
- Most organizations continue migrating to a multi-cloud strategy and are leveraging SaaS-based applications and hosted platforms.
- Many organizations will continue to support a growing number of employees wanting to work from home. The transition to remote work will require a more secure means for remote technologies, including cloud and on-premises access to systems in a single authentication solution.
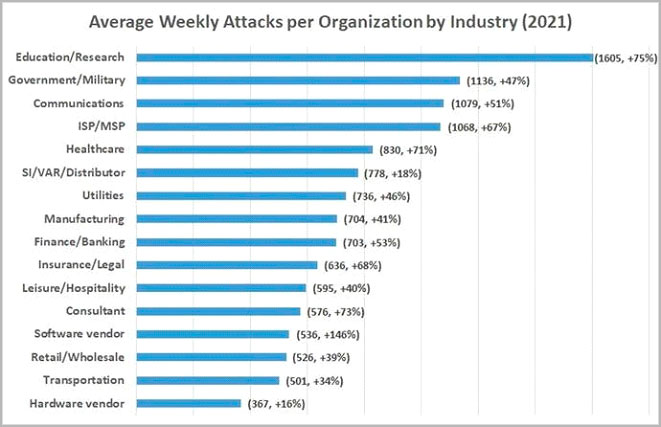
Figure 2 – Forbes – Increase in Number of Cyber Attacks by Industry in 2021
To meet these new and increasing cybersecurity challenges and attacks, CIOs and CISOs are focusing a growing portion of their budgets on critical security adaptive controls to meet the needs of the business.
Cloud-Based Security Services
Approximately 36% of the new funding for CIOs and CISOs will be for cloud-based security services. These services specifically address security threats against the organization’s cloud infrastructures. Examples of cloud-based security capabilities include identity and access management, virtual firewalls, distributed denial-of-service protection, cloud-based security broker services (CASB) and DLP, host-based intrusion technology, and security event monitoring.
CASB has provided excellent value for clients operating in a hybrid multi-cloud architecture. CASB provides a centralized data loss prevention strategy integrated with more visibility, enforcement capabilities, and better file control than previous strategies. CASB also is critical for clients considering enabling an XDR strategy by correlating several security telemetries into a single console. CASB vendors and several XDR vendors have proven integration architectures available today.
Cloud Infrastructure Management
Many organizations will move their cloud-based workloads to cloud computing platforms or Infrastructure-as-a-service, software-as-a-service, and platform-as-a-service. Approximately 35% of the net-new spending for cybersecurity goes into these cloud management offerings.
Many service providers offer this utility as a cloud computing service. These firms, including Oracle, Amazon, Salesforce.com, Databricks, and Snowflake, offer various cloud-based security services with integrated security protection for client workloads. Many CIOs and CISOs recognize a faster time-to-market with these platforms and better-integrated security protection at a lesser cost than a traditional in-house model. Further, these cloud providers offer servers, databases, networks, and storage within their cloud infrastructure management offerings.
Even with the continued consumption of multi-cloud services, 55% of companies polled by 451-research reported a cloud-data breach in 2022. 51% of the companies sighted the challenge of adapting to a cloud security model compared to their legacy on-premises environment. Many in the survey commented that they failed to encrypt their data once the content moved into cloud infrastructure hosted systems.
Application Development Security
Once an organization has decided on a cloud infrastructure management platform, they plan to leverage it in their digital transformation strategy; the next critical security event is application development security. 35% of net-new spending in cybersecurity is focused on protection applications before, during, and after the software development lifecycle (SDLC).
Solutions to help protect application development include investments in encryption, authentication, application testing tools, penetration testing services, and application auditing and compliance validation tools. These investments ensure the integrity of the application, along with aligning the application into a security or compliance framework like NIST-800-53, FEDRAMP, HIPAA, or PCI-DSS.
Cloud Data Protection
With the application development protection enabled successfully within the cloud infrastructure, the next critical investment CIOs and CISOs are making is around cloud data protection. Nearly 33% of net-new cybersecurity spending focuses on tools and infrastructure to defend the cloud’s data. Service providers and IaaS providers often provide layers of security protection. However, the ultimate responsibility for data protection typically falls on the client.
For compliance and privacy mandates and reporting, the client is responsible for safeguarding all data within their domain. Organizations will leverage cloud-based data protection capabilities, including backup, restore, and disaster recovery, to ensure their critical information is safe. The client will also enable data encryption for further protection at rest and in transit.
Defining the Next Generation of Cloud-Based Remote Access and Endpoint Security
With the infrastructure, applications, and data cloud security enabled for integrated protection, the next series of critical investments that CIOs and CISOs will focus on is how the users, customers, and business partners will access these new platforms.
Cloud-Based Services and Zero-Trust Access Control
Before COVID, many organizations were investing in better and more secure ways for remote workers and contractors to connect to the various corporate systems; either in the cloud, SaaS, or on-premises. Due to the pandemic, organizations had to accelerate their strategy to accommodate nearly all employees who were forced to work remotely over the past two years.
Zero-trust spending increased by 32% from the previous year. This new layer of security edge service also had a significant increase in net-new spending. Both emerging security technologies often are deployed together.
Organizations enabled zero-trust frameworks to push the user connections to cloud-based SASE service for the initial remote access connection. The zero-trust philosophy would operate similarly to a proxy connection by handling all authentication, including multi-factor. Once the user is authenticated, zero-trust would apply various policies to control where the user will be allowed to connect. In some cases, zero-trust will establish a front-end/back-end full proxy connection for UDP or TCP-specific connections for enhanced security. Zero-trust with SD-WAN capabilities could direct the user to a more optimized WAN connection based on their GEO location and business requirements.
Approach to Security Management and Automation
Without the means to manage cloud-based security controls and on-premises adaptive controls, organizations will undoubtedly continue to see a rise in cybersecurity breaches. Most security breaches are caused by known issues that continue to be impactful due to a lack of proper security operations. Unpatched systems still generate 27% of all security breaches, and attacks on the software supply chain are around 17%.
Organizations continue to invest in security information and event management platforms (SIEM). This platform gathers security from multiple sources, including Syslog, SNMP, and API, to help correlate and rationalize the data. Many SIEM solutions also incorporate AI and ML within their platforms, aligning the content into the MITRE ATT&CK framework and Lockheed Kill Chain tools. Once the data has been rationalized, organizations continue to expand their efforts to leverage SOAR automation to take security action to stop threat propagation.
Once organizations have enabled various cloud services, infrastructure, security, and data management strategies, a critical component also needs considerable investment. Security orchestration, automation, and response (SOAR) continue to be a crucial pillar for organizations to leverage their security investments to their fullest extent.
The investment in SOAR capabilities also witnessed considerable growth in the last year. SOAR had 34% additional spending by CISOs and CIOs. Without SOAR, organizations will not be able to enable new security capabilities, apply security updates and patches, and spin up and down virtual security appliances quickly. SOAR investments help organizations execute their SecOps and DevOps strategies.
Continuous Challenge to Find and Retain Talent
Before any organization considers a new groundbreaking digital transformation strategy that requires a new generation of cloud-based applications, services, and security controls, the organization needs to evaluate if they have the human capital to ensure these projects will be successful.
Digital transformation strategies often fail due to a lack of talent. Finding and retaining skilled and experienced software engineers, cybersecurity experts, and CISOs is a global problem. Organizations considering reshaping their business models need to have a firm strategy to recruit and retain talent relevant to their forwarding strategy.
Many organizations have begun leveraging the NIST framework for employee evaluation and retention. NIST developed the NICE framework to identify, develop, recruit, and retain experienced cybersecurity personnel. The framework provides a structured method to track performance, identify shortages in skill sets, develop better job descriptions, and interact with HR and recruiters.
The Role of the MSSP in Digital Transformation and Cloud Security
Managed security service providers (MSSP) are critical in an organization’s ability to leverage its security control to align with its digital transformation. These service providers help manage an organization’s complete security posture, including cloud-based security platforms, data management, and zero-trust architectures. MSSPs can access global talent and offer various engagement models, including security operations as-a-service, incident response handling, and monthly security awareness training. Organizations struggling with talent recruitment could leverage MSSPs for staff augmentation along with 24 x 7 x 365 security monitoring.
Conclusion
As the Foundry survey suggests, most organizations continue to struggle to solve their cybersecurity breaches and face increases in their cybersecurity insurance premiums. Companies also continue to invest smaller capital in overall governance risk and compliance (GRC). Organizations that are making increased investments in cybersecurity also should be making an equal or more significant investment in risk management. By managing risk through a proven GRC strategy, deploying new cybersecurity controls to lower risk within their environment will improve their posture and maximize the technology investments.
Even with investments in cybersecurity, unless the organization has qualified talent in cybersecurity and risk management or through a partnership with an MSSP, these investments will never be recognized for the value they could bring to an organization to stop attacks from hackers and cybercriminals.







