The Indigo Bookstore Ransom Cyber Attack – Lessons Learned
The recent attack on the Indigo Bookstore left many cyber security analysts scratching their heads. How did attackers seize control of systems through ransomware, and how was a zero-day exploit used? It’s not just a matter of understanding what happened but also learning from it to prevent similar attacks from occurring in the future. So, let’s examine the Indigo Hack and determine what steps can be taken based on the principles of cyber defense to avert a successful breach like this from ever happening again.
The Indigo Hack was a zero-day exploit ransomware attack that targeted the Indigo Bookstore. This type of malicious cyber attack is highly dangerous as it is done using zero-day exploits, which means the vulnerabilities being exploited have not previously been identified and leave the victim unprotected until it is too late. Security professionals must be fully aware of zero-day threat vectors and establish secure systems with efficient patches against known and even unknown cyber threats. If Indigo had been consistently patching its system, it might have avoided this incident altogether.
To be clear, a Zero-day vulnerability is sometimes written as 0-day. The words vulnerability, exploit, and attack are typically used alongside zero-day, and it’s helpful to understand the difference:
- A zero-day vulnerability is a software vulnerability discovered by attackers before the vendor has become aware of it. Because the vendors are unaware, no patch exists for zero-day vulnerabilities, making attacks likely to succeed.
- A zero-day exploit is the method hackers use to attack systems with a previously unidentified vulnerability.
- A zero-day attack is the use of a zero-day exploit to cause damage to or steal data from a system affected by a vulnerability.
How were the Criminals Able to Exploit the Vulnerability?
Software often has security vulnerabilities that hackers can exploit to cause to steal data or lock data, as they did with Indigo. Software developers are always looking out for vulnerabilities to “patch,” – which means developing code or a solution that they release in a new software update.
However, sometimes hackers or malicious actors spot the vulnerability before the software developers do. While the vulnerability is still open, attackers can write and implement code to take advantage of it. This is, again, known as exploit code.
The hacker was able to exploit a zero-day vulnerability to gain access to access Indigo’s systems and files. This is why it’s vital for organizations large and small to take cyber security seriously by regularly auditing their security posture. A qualified IT security analyst should be able to pinpoint areas of weakness and provide guidance on how best to mitigate risk – making it less likely for hackers to succeed in exploiting unknown vulnerabilities. By taking cyber defense principles seriously, businesses can avoid the costly repercussions stemming from cyber attacks.
What Cyber Defense Principles can be Applied to Prevent Similar Attacks?
Cyberattacks using zero-day exploits aren’t uncommon, especially considering the rise in cybercrime over the years. To prevent similar attacks like the one Indigo Bookstore underwent, fundamental cyber defense principles are key. A cyber posture assessment is one of the top cyber defense principles that can be applied. This assessment involves identifying and evaluating current cyber threats within an organization and then structuring actions and protocols to establish the appropriate posture for preventing cyber-attacks. Not only will this minimize any potential impact from a successful cyberattack, but it will also help create multiple layers of security against cybercriminals attempting malicious activities. Other cyber defense principles that organizations should take into account include implementing a secure backup solution, rigorous patch management, threat detection systems, and ongoing security awareness training for employees.
Cybersecurity is an ever-changing landscape, so it is important for businesses to stay up-to-date on emerging threats and ensure they have adequate measures in place as well as having skilled IT personnel to identify potential vulnerabilities and assess any risk posed by them. It is also important that security policies are regularly reviewed and enforced – this will ultimately go a long way in keeping business operations safe from malicious entities.
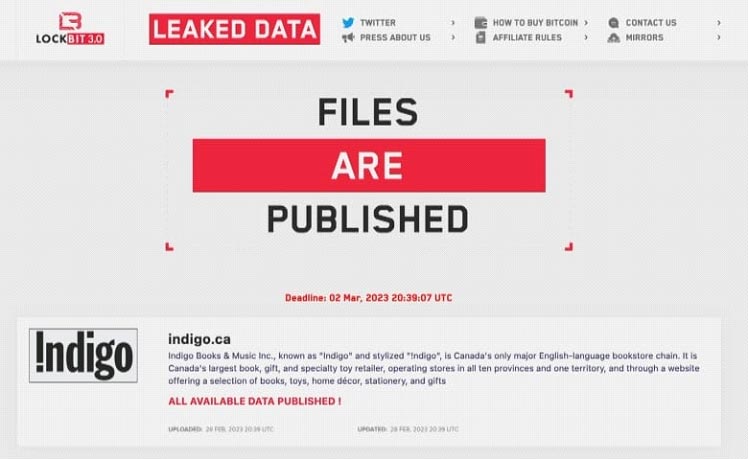
The Indigo Bookstore Ransom Cyber Attack – Lessons Learned
Ways to Patch Existing Vulnerabilities Before they are Exploited
CISO’s and CIO’s should consider the best course of action for their company to ensure the most up-to-date security solutions are in place, to prevent further cases of ransomware attacks from taking advantage of existing vulnerabilities. By having measures in place such as continuous patching of all systems, companies can save themselves from incurring huge damages resulting from cyber attacks. Therefore, it is imperative that CISO’s develop a consistent risk methodology to deploy and review frequently updated threat intelligence sets to effectively identify and prioritize threats for private organizations. CISOs must use proactive cyber defense principles, along with relevant compliance standards, security tools, and training procedures such as patching existing vulnerabilities quickly before they are exploited by malicious actors.
Previous Blog Post Dealing with Adopting a Risk-Based Patch Management Process – https://secureops.com/blog/taking-a-risk-based-approach-to-patch-management/
Previous Blog Post Dealing with Patch Management Best Practices – https://secureops.com/blog/patch-management-best-practices/
Lessons Learned from the Indigo Cyber Attack
Let’s start this final section by taking a step back to find a good starting point before we get into the “Lessons Learned.” Ransomware has become one of the biggest cybersecurity threats facing individuals, businesses, and organizations worldwide. Ransomware is a type of malware that encrypts the victim’s files, rendering them unusable, demanding a ransom payment in exchange for the decryption key. In recent years, ransomware attacks have become more sophisticated, targeted, and costly, causing billions of dollars in damages and lost productivity. Ok, now that we’ve stepped back and defined the threat, let’s move forward with the 6 strategic steps you can take to prevent being a victim of a ransomware attack and many other types of attacks.
- Backup Your Data Regularly
One of the most effective ways to defend against ransomware is to back up your data regularly. Backup your important files and data to an external hard drive or cloud-based storage service regularly. This will ensure that you have a copy of your data in case your files become encrypted by ransomware.
- Keep Your Software Up-to-date
Keeping your software and operating system up-to-date is crucial to defending against ransomware. Cybercriminals exploit vulnerabilities in outdated software to gain access to your system and launch ransomware attacks. Install the latest security updates and patches as soon as they become available.
- Use Antivirus and Anti-malware Software
Antivirus and anti-malware software can help detect and prevent ransomware attacks. Ensure that you have reputable antivirus and anti-malware software installed on your computer and keep it up-to-date. Regularly scan your computer for viruses and malware to detect any potential threats.
- Train Employees and Staff
Human error is one of the leading causes of ransomware attacks. Train your employees and staff on how to recognize and avoid suspicious emails, links, and attachments. Encourage them to report any suspicious activity or security concerns immediately.
- Implement Access Control and Security Policies
Implementing access control and security policies can help defend against ransomware attacks. Limit access to sensitive data and systems, and implement a password policy that requires strong and unique passwords. Use multi-factor authentication for additional security.
- Have a Cybersecurity Incident Response Plan
Having a cybersecurity incident response plan can help you respond quickly and effectively to ransomware attacks. Your plan should include procedures for isolating and containing the infected systems, communicating with stakeholders, and restoring data from backups.
In conclusion, ransomware attacks are a serious cybersecurity threat that can cause significant damage and financial losses. However, by implementing these cyber defense measures, you can protect yourself and your organization from ransomware attacks. Remember to back up your data regularly, keep your software up-to-date, use antivirus and anti-malware software, train your employees and staff, implement access control and security policies, and have a cybersecurity incident response plan. By taking these steps, you can reduce your risk of becoming a victim of ransomware.
To Learn More About How to Defend Against Malware Attacks or If You Have Been Attacked, Please Call Us – as Always; We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/