Why Organizations Are Moving to Managed Firewall and SIEM Solutions
Overcoming the Challenges of Firewall and SIEM Management
This blog post is not a commercial for SecureOps; we have just worked with enough clients to know that tuning firewalls and managing SIEMs, particularly handling the hundreds, if not thousands of security alerts is overwhelming. In addition, the business case for managed firewall and SIEM centers concerning the reduction of cost and the ability to leverage security expertise to help manage operations and protect the business from cybersecurity threats and data breaches is becoming more compelling. The increased complexity of the solutions and the growing number of threats are too much even for the mid-sized and large SOC’s that we serve.
To be clear, managed SIEM is an alternative to on-premise deployment, setup, and monitoring of a firewall and SIEM software solution where an organization contracts with a third-party service provider to host the applications on their servers and monitor the organization’s network for potential security threats. Check out our blog post below which documents the benefits of using a SIEM to improve a company’s overall security defense. Organizations choose managed SIEM and firewall for their corporate security needs to deploy faster, reduce setup and training costs, and leverage the expertise of cybersecurity specialists.
The Benefits of Using a SIEM to Improve IT Security
https://secureops.com/security/blog-what-is-a-siem/
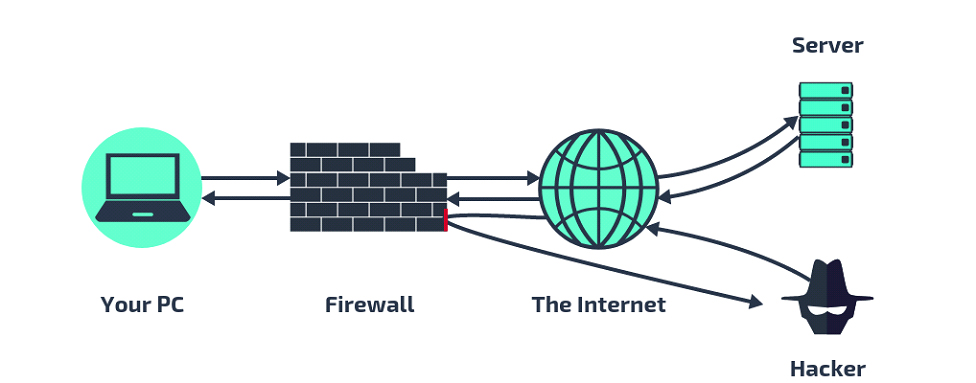
Companies have come to understand the criticality and expense that a firewall and security event and information management (SIEM) solution are to an organization’s cybersecurity defenses. However, just purchasing and deploying these systems is not enough. Organizations commonly make simple mistakes and face challenges in managing these systems that degrade or negate their effectiveness at protecting against cyber threats.
Common Challenges with Firewall Management
A firewall is a network security device that examines network traffic. Based on rules and policies, the firewall inspects network traffic to block the traffic that is suspicious or unwanted. Firewalls developed by industry leaders like Cisco, Palo Alto, and Fortinet have been the first line of defense in network security for over 25 years. They establish a barrier between secured and controlled internal networks that can be trusted and untrusted outside networks.
A strong firewall is a vital component of any organization’s cybersecurity strategy. It serves as the first line of defense and is capable of filtering out a large amount of potential attack traffic before it can reach and impact an organization’s internal systems.
Filtering data packets is the base of how a firewall works. The main thing a firewall looks at is the IP address of the source or destination. If the IP address fails to follow the security rules that have been established, the data packet is rejected so you’re protected against malicious attacks.
Modern firewalls are more advanced (and complicated) and they can filter the traffic based on various criteria such as keywords, domain names, applications, and specific data ports.
However, a firewall is only effective if it is configured and managed correctly. A misused firewall can be worse than no firewall at all since it provides a false sense of security. As a note, you can have hardware or software firewalls and those firewalls can have specialties like Packet filters, Stateful firewalls, Application layer firewalls, and Next-Generation Firewalls or NGFW. We won’t get into the specific firewalls in this blog post.
Poor Rule/Policy Configuration and Management
A firewall is designed to define and enforce a boundary between a protected internal network and the outside world. It does so by inspecting all of the traffic passing through it and allowing or blocking traffic based on predefined rules.
A firewall is only an effective protection against cyber threats if it has good rules. Some common examples of mistakes made when creating firewall rules include:
- Making rules too general. It is easier to define a DEFAULT ALLOW rule or leave a port completely open than to explicitly define the types of traffic that should be allowed through. However, these broad rules create the potential for malicious traffic to slip through as well.
- Failure to restrict internal protocols. Some types of traffic, such as SQL and LDAP, have no reason to cross the network boundary. A failure to block these and other internal protocols at the network boundary can lead to accidental exposure of sensitive data.
- Not limiting access to certain protocols. Some protocols, like SSH, have legitimate uses outside of the network but only for certain users. Firewall rules should be defined to restrict usage of these types of protocols.
A firewall can be a powerful tool for protecting against cybersecurity threats. However, they need to have properly designed and implemented firewall rules to be effective.
Failure to Manage and Monitor
No cybersecurity solution should be “fire and forget”, and a firewall is no exception. If a firewall is set up and then left to do its own thing, then it provides little or no benefit to the organization.
A firewall should be monitored and frequently updated and reconfigured as part of an organization’s cybersecurity strategy. Some common issues that occur due to a failure to properly monitor and manage a firewall include:
- Missed updates. Firewalls require updates just like any other software or firmware. Failing to install these updates on-time could result in a firewall being unable to properly monitor network traffic or even be vulnerable to exploitation.
- Overlooked security events. Firewalls generate logs and alerts based upon the anomalies that they detect. Not looking at these logs could mean that an organization is unaware of an ongoing cyberattack.
- Degraded performance and effectiveness. Organizations grow, and their security needs grow with them. An outdated firewall solution may be incapable of keeping up with traffic volumes or may not be capable of monitoring all of an organization’s network traffic.
Firewalls are powerful tools for cybersecurity, but a mismanaged one can also be a major liability. An unpatched or unmonitored firewall could be the target of an attack or could be allowing malicious traffic to pass by undetected.
Common Challenges with SIEM Management
SIEM’s including Log Rhythm, Splunk, Alien Vault, and many others provide the critical data and information that IT security teams require including security event data and network flow data. SIEM’s have become the core of most IT security operations and solutions because of their ability to normalize and analyze data. Simply, they collect logs and data from dozens of disparate devices to provide a flow of correlated insights to threats from a single source in real-time. Further, SIEMs can be set up to deliver alerts to the security operations team when suspicious activity is uncovered or to simply gain better visibility to vulnerabilities and threats in the environment.
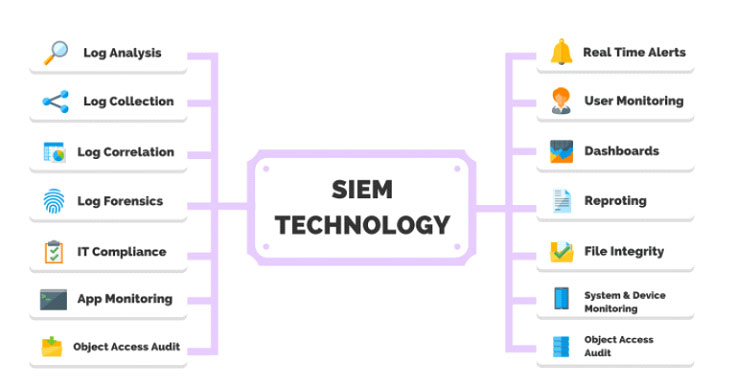
The challenge for most organizations, however, is that the upfront cost of the technology is significant, and implementing it to communicate with other technologies is a manual process and often too time-consuming when handled internally. Further, the noise from the number of alerts or events and incidents is overwhelming and often confusing. Finally, the implementation and integration with other security assets and the ongoing correlation and analyzation of the vast amounts of disparate data that is generated by the SIEM often leave analysts with little time for strategic analysis.
A SIEM solution can be a major force multiplier for a security team. By providing automatic data aggregation and analysis, it can enable analysts to rapidly identify potential threats that would otherwise be overlooked.
However, a SIEM solution is not plug-and-play, it needs to be properly configured and used in order to effectively protect an organization against cyber threats.
Selecting Data Sources
A SIEM solution is designed to aggregate multiple sources of cybersecurity data and provide context to security analysts. This can be a major asset for incident and detection and response since data from multiple sources can often enable the detection of cybersecurity incidents that seem like harmless anomalies from the perspective of a single tool.
However, while access to data is important to the proper function of a SIEM, more data is not better. The more data feeds that a SIEM has to ingest and process, the longer it will take to respond to analysts’ queries.
An effective SIEM requires a carefully curated collection of input feeds designed to provide maximum visibility without including useless data. Developing such a feed requires in-depth knowledge of cybersecurity and the sources of valuable data within an organization’s network.
Defining Use Cases
SIEMs run on use cases. While a SIEM can automatically ingest data from an organization’s network, it needs to be told what to look for in that data. A SIEM use case defines a potential attack scenario and how to find it in the available data.
While some generalized SIEM use cases are available, it is also important to have tailored ones as well. The potential cybersecurity threats faced by a financial institution are very different from those seen in the retail sector. Maximizing SIEM effectiveness requires SIEM use cases tailored to the organization.
Defining these use cases requires deep cybersecurity expertise. The use case developer needs to know a potential attack vector, how it can be detected, and how to find that particular information within an organization’s network.
High Alert Volumes
A SIEM solution is designed to aggregate data from multiple sources and use it to filter out extraneous and false-positive alerts. However, it is not a perfect solution. While a SIEM may emit fewer alerts than a collection of standalone systems, alert volumes can still be high.
Attempting to manually manage security alerts can quickly overwhelm an organization’s security team. The average SOC receives over 10,000 alerts each day, and each alert must be viewed, triaged, investigated, and potentially responded to.
Most organizations lack the resources to handle this volume of alerts. As a result, some alerts are ignored or overlooked, leaving the organization unaware of potential attacks.
The Advantages of a Managed Firewall and SIEM
In many cases, organizations do not have all of the specialized resources and cybersecurity expertise in-house to effectively configure, use, and maintain their firewall and SIEM solutions. While these systems can be a major asset for protecting the organization against cyber threats, they are only effective if properly configured, monitored, and maintained.
For example, managed SIEM providers offer the core services of SIEM, such as security monitoring and incident response, but they can also handle tasks that your in-house team may normally handle. Delivering monthly security reports, installing patches and updates, managing compliance, maintaining the SIEM configuration and asset inventory functions can all be offered by with the help of a MSSP.
Managed firewall and SIEM services enable an organization to achieve the benefits of first-class cybersecurity protections without the need to fully manage the solutions in-house. A managed firewall and SIEM provider will have both the expertise necessary to properly configure and maintain these systems and the tools to ensure that they provide maximum value in the form of high-quality, curated alerts.
To Learn More About Managed SIEM and Firewall Services or If You Have Been Attacked Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/







